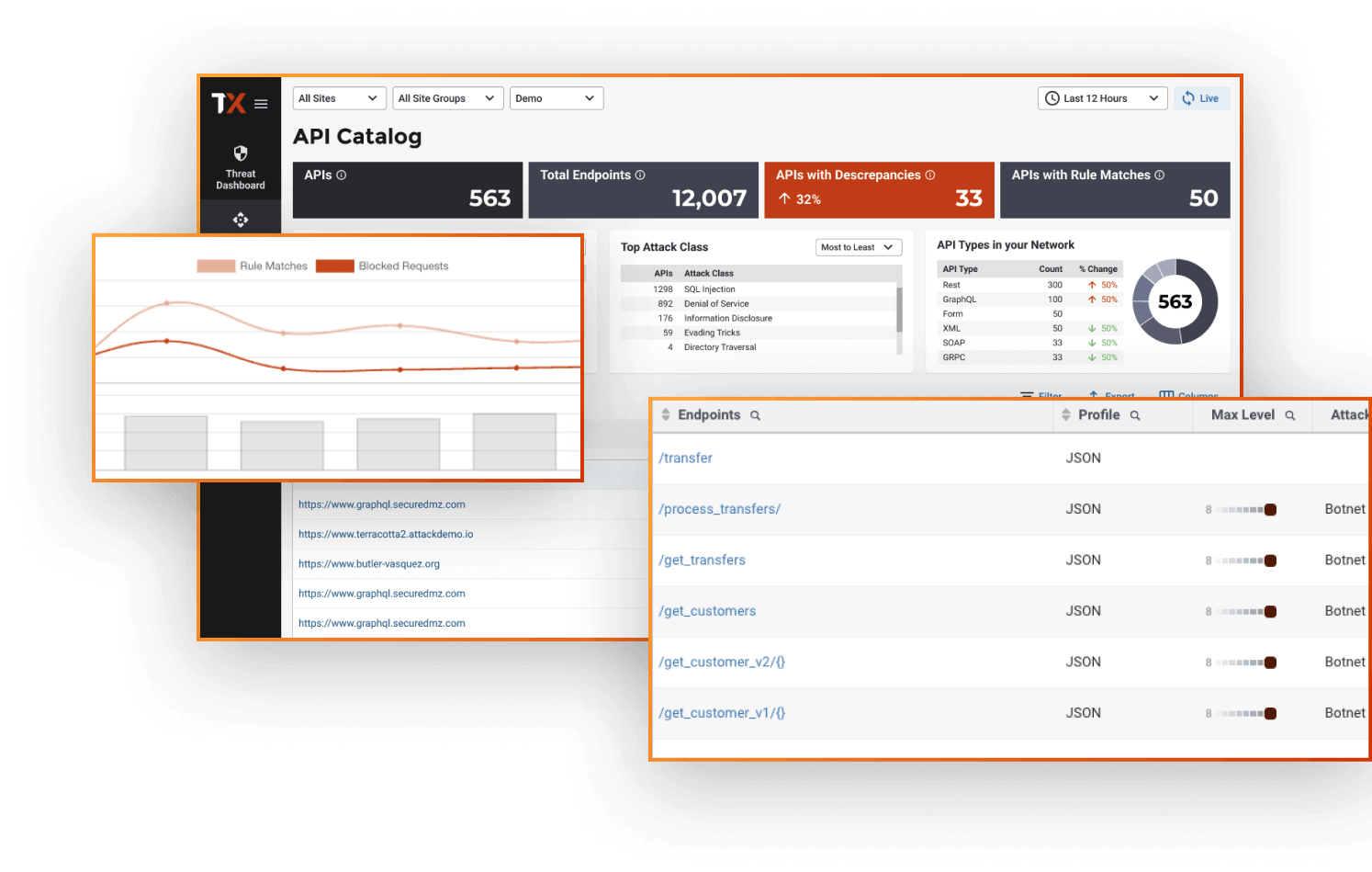
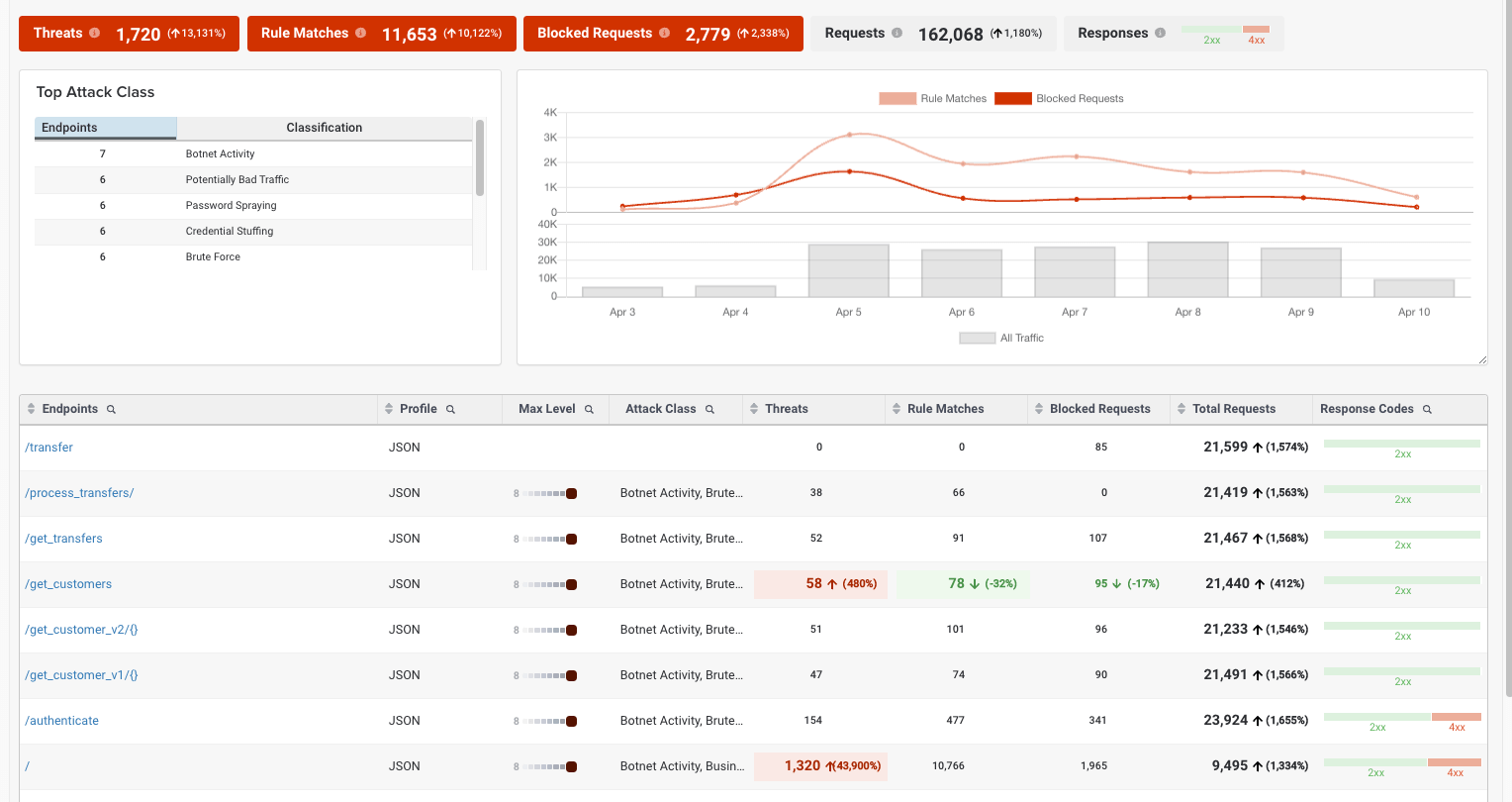
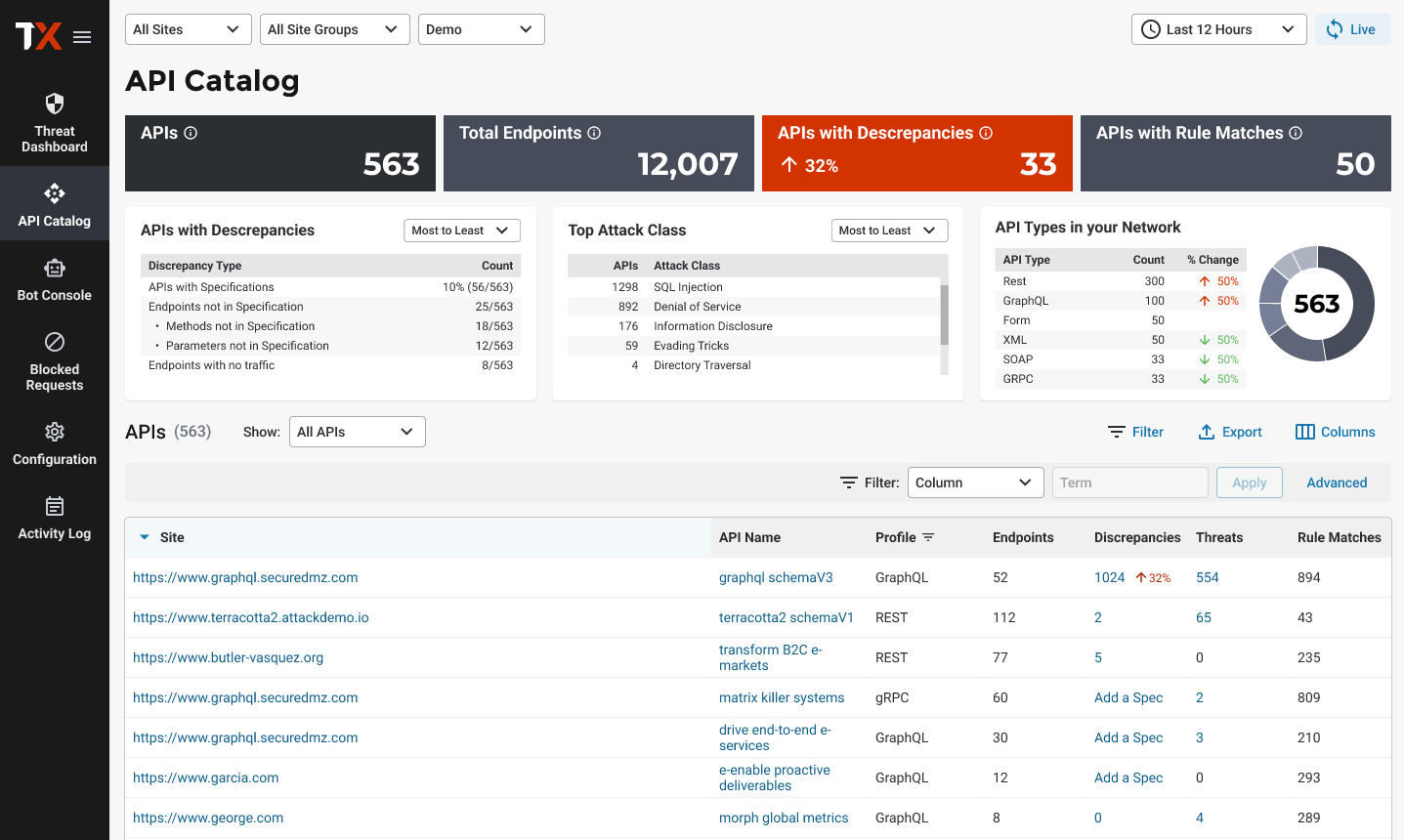
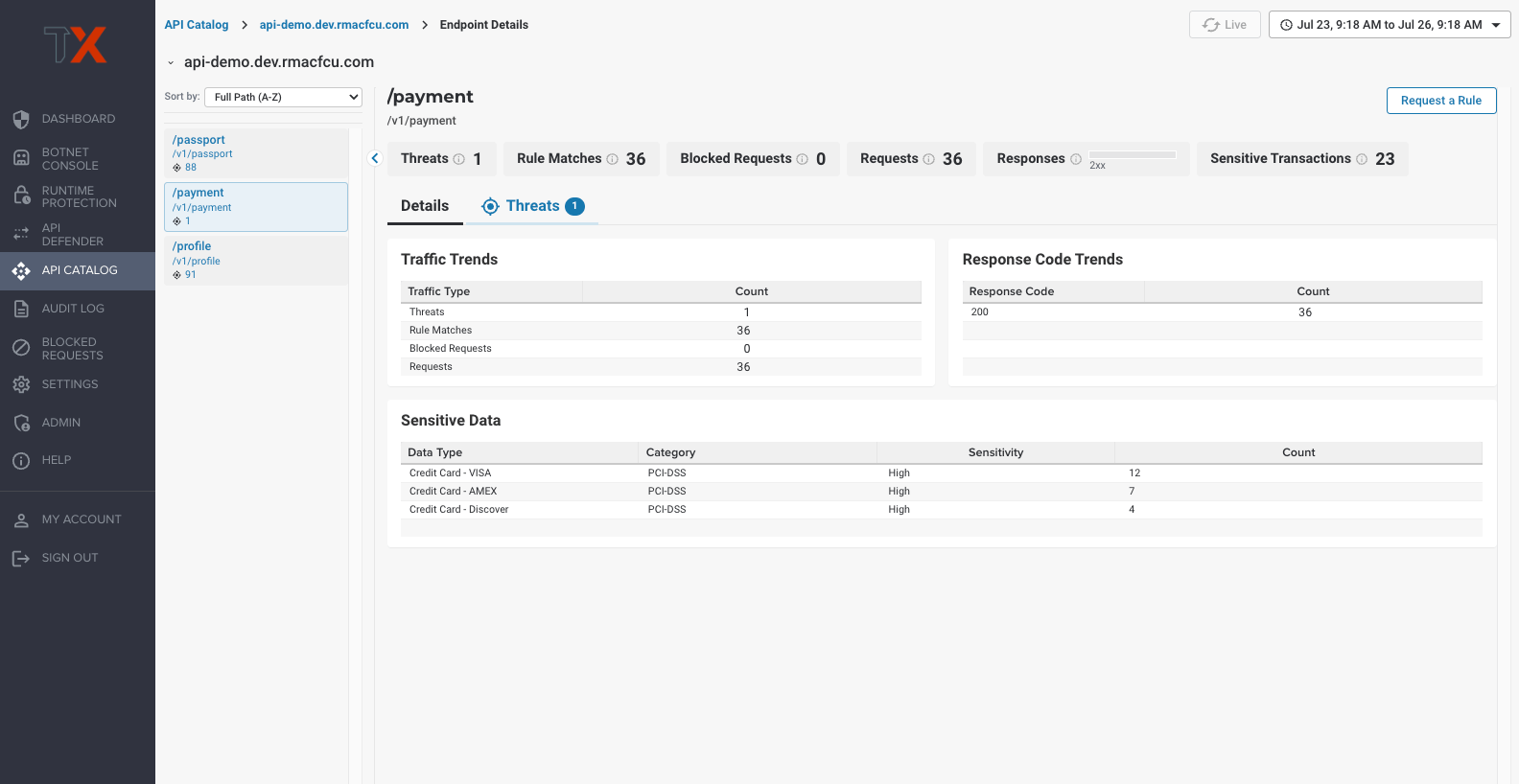
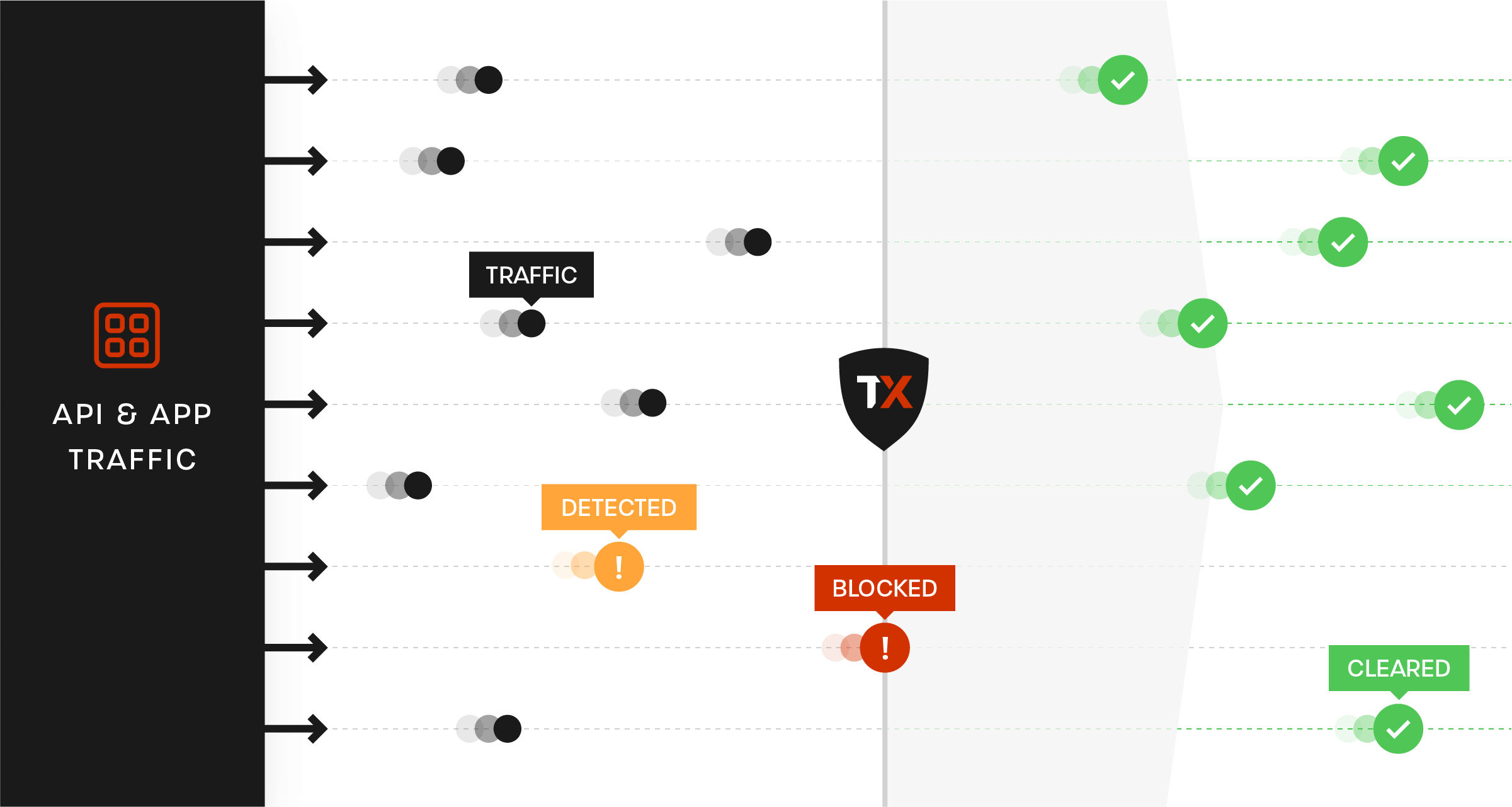
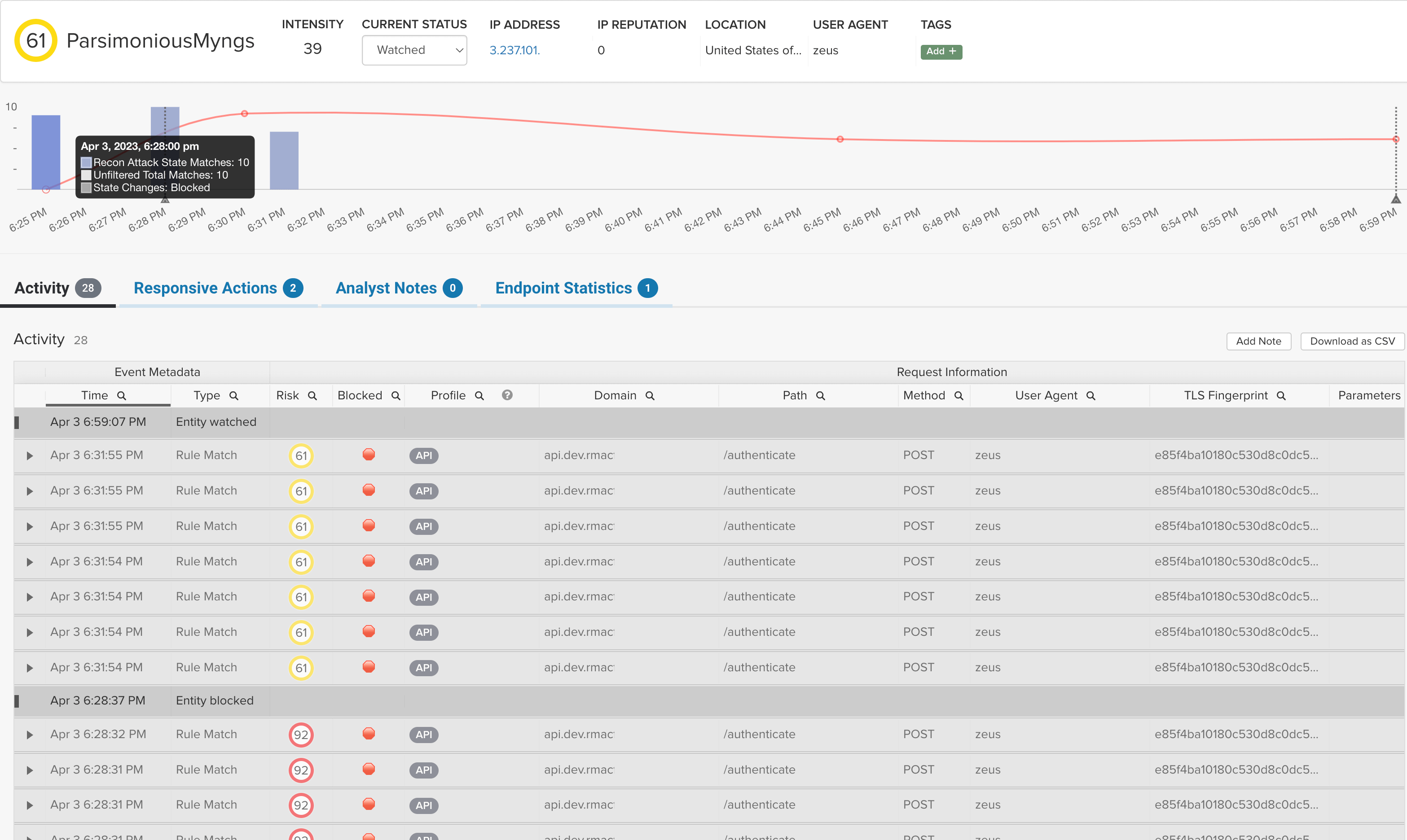
“We look at our ThreatX dashboard and pinpoint whether attackers are just getting their feet wet, or really trying to exploit us. It’s a good visual because we can see clearly what to focus on. With other solutions, it was just an immediate block for anything that met a rule.”
Marco Escobar, Senior Director of Operations, Segpay
Read the full case study