“It’s been easy to work with the Protection-as-a-Service team. I feel, and the team feels, like they’re an extension of our information security team.”
Information security analyst at financial services organization
Read our case studies
“It’s been easy to work with the Protection-as-a-Service team. I feel, and the team feels, like they’re an extension of our information security team.”
Information security analyst at financial services organization
Read our case studiesWho is targeting us, and what are we doing to stop them? ThreatX is built to help teams answer these questions quickly and easily.
Most organizations getting started with API security programs are simply looking to visualize their API attack surface and protect the APIs that are powering their brands, and they’re looking to do it fast. With ThreatX, you’ll get instant visibility and protection in minutes. Furthermore, ThreatX conducts continuous API discovery for every API endpoint – anywhere, any status – with no extra work from you.
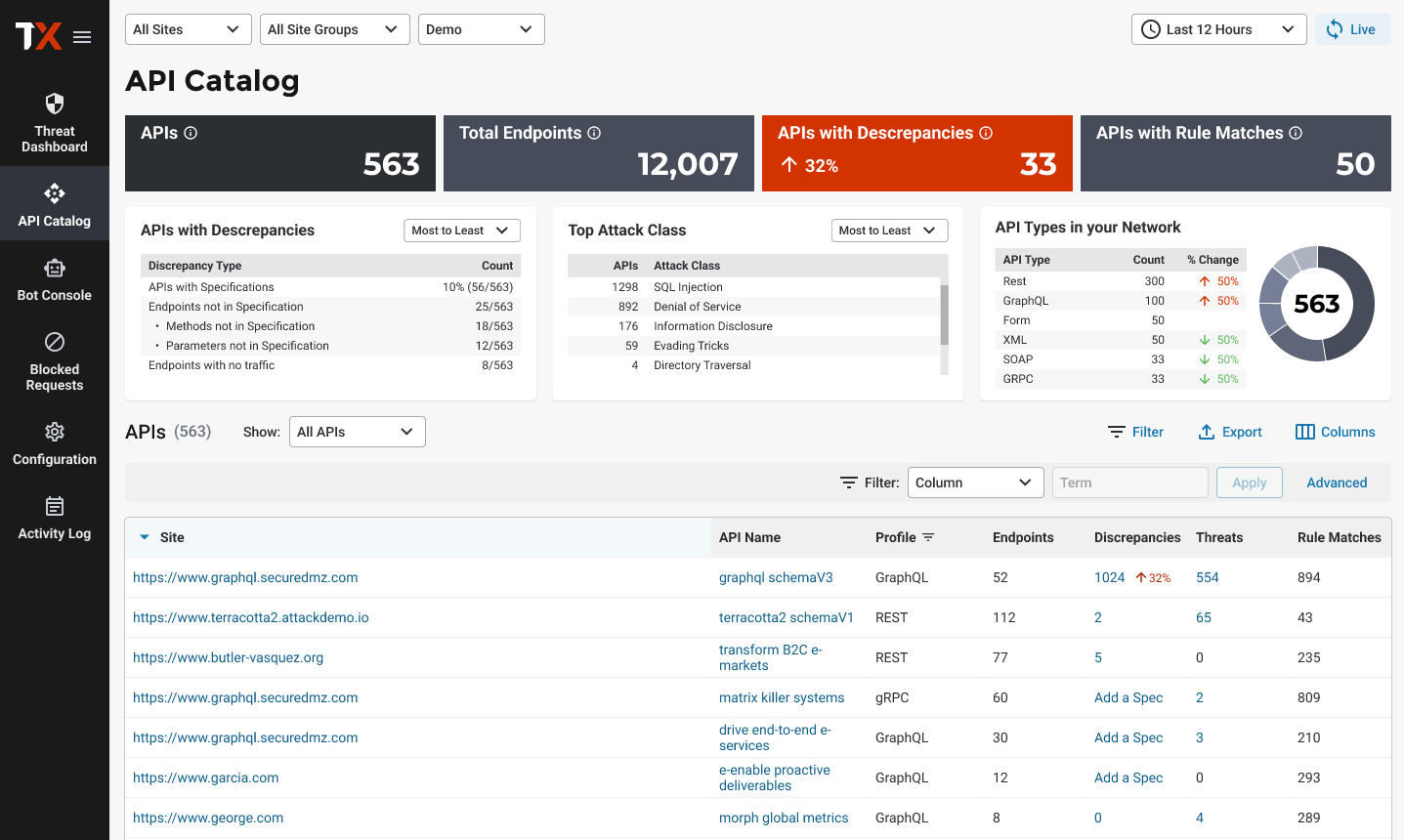
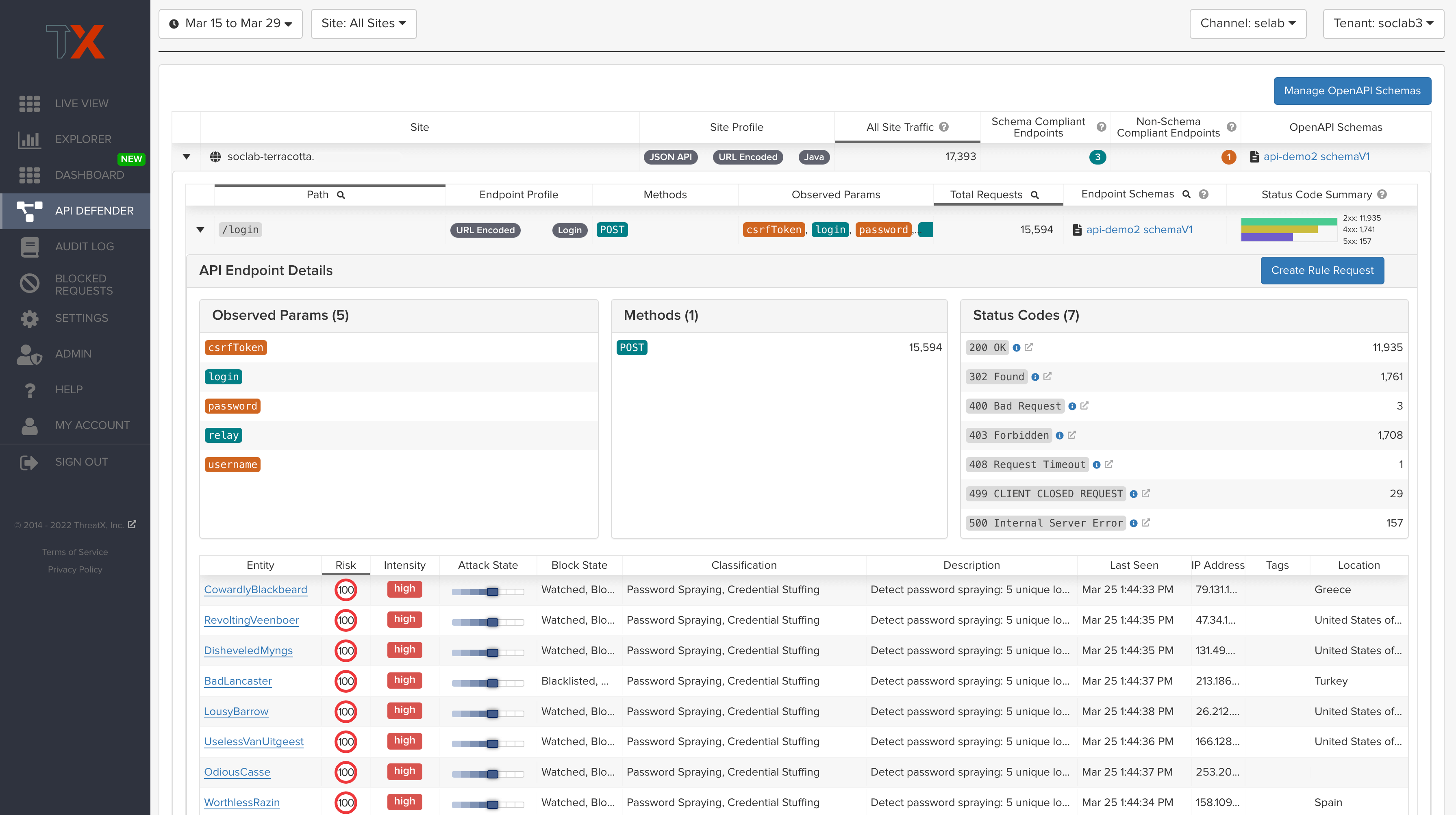
For many organizations, particularly those with distributed DevOps teams, API schemas provide a central way of defining how APIs should work. Without a schema, it’s difficult for security teams to understand whether any API call is legitimate or malicious, creating a significant security risk for organizations.
To address this challenge, ThreatX centrally manages OpenAPI 3.0 schemas for the API endpoints it discovers and protects. This capability enables organizations to compare API traffic to specifications, determine whether compliance gaps exist, and work to mitigate them.
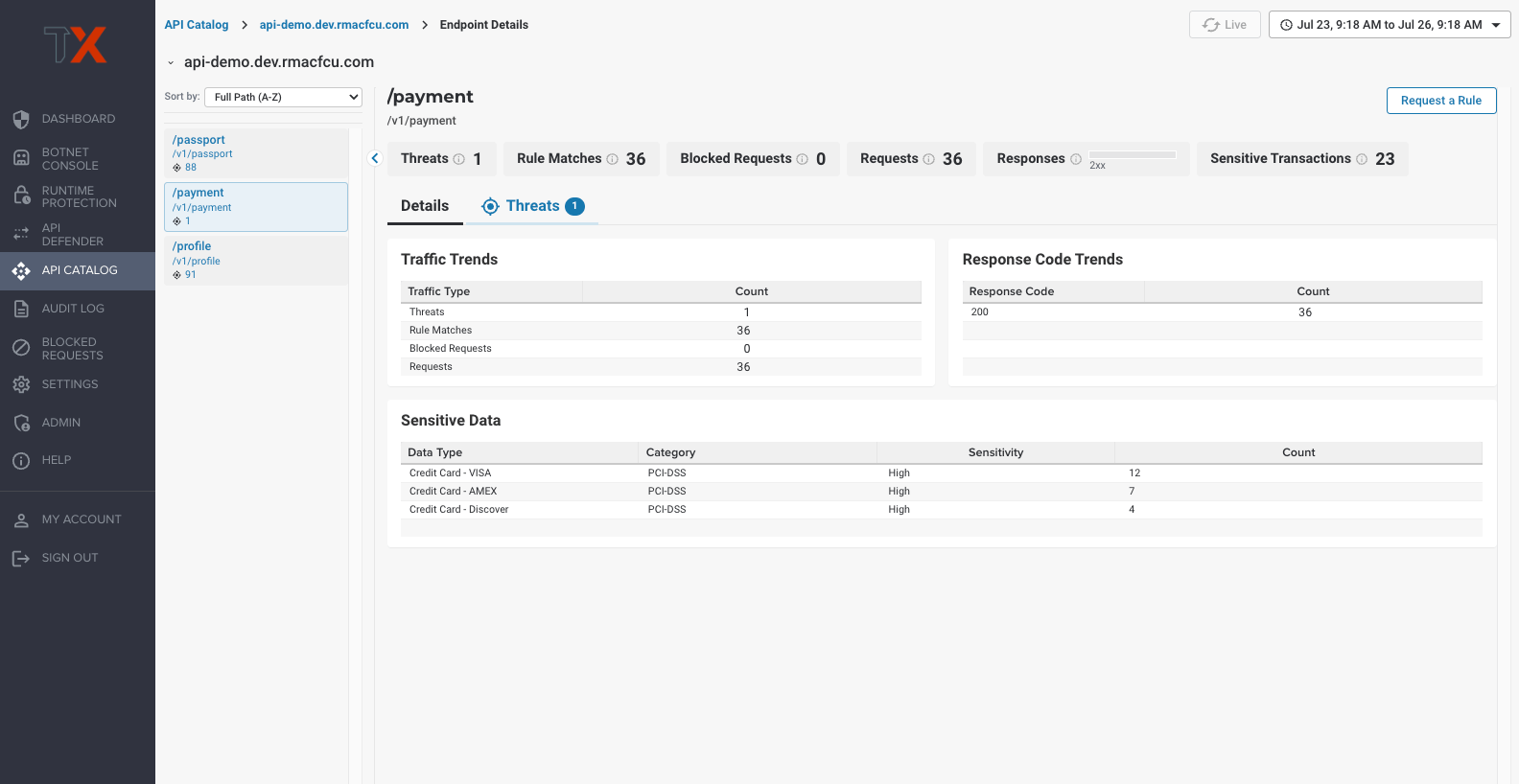
The risk of sensitive data loss is significant and can have serious consequences, such as identity theft, financial losses, damage to a brand’s reputation, and legal and regulatory fines. ThreatX enables security teams to detect and visualize API transactions that contain sensitive user information and authentication data — helping them boost the protection of high-risk APIs, prevent data breaches, and comply with privacy regulations.
This capability helps organizations adhere to privacy regulations like PCI DSS and GDPR by identifying and monitoring API traffic containing personal information, payment card data, and authentication information that would expose the risk of unauthorized access to systems.
Take a quick interactive tour to learn how ThreatX protects sensitive data

Key Benefits

Experience user-friendly security designed to focus on what matters most. Leverage simplified dashboards so you can effortlessly oversee your API and application’s security posture and risks.
Get your nights and weekends back with always-active security that ensures your APIs and applications stay safe. Our visionary technology provides continuous protection and prevention without the need for manual intervention. Enjoy peace of mind knowing that your APIs and applications are secure even when you’re off the clock.
ThreatX solutions are always monitoring, assessing, and identifying risks to APIs and applications continuously based on behavior. Our technology learns to recognize threats and vulnerabilities specific to your system, and proactively stops them based on risk level. This ensures your business remains operational and efficient, without interruptions.