A Bot Management Solution That Won’t Feel Like Playing Whack-a-Mole
We help busy teams detect and block bot-based attacks as well as other forms of malicious traffic automation
- Set-it-and-forget-it bot management
- Protect APIs & applications against DDoS, botnets, and more
- On-board sites in minutes
- Fully managed, with 24/7 support
Confidently prevent bot attacks against APIs and applications without burdening your team or hindering legitimate user traffic.
How We Help
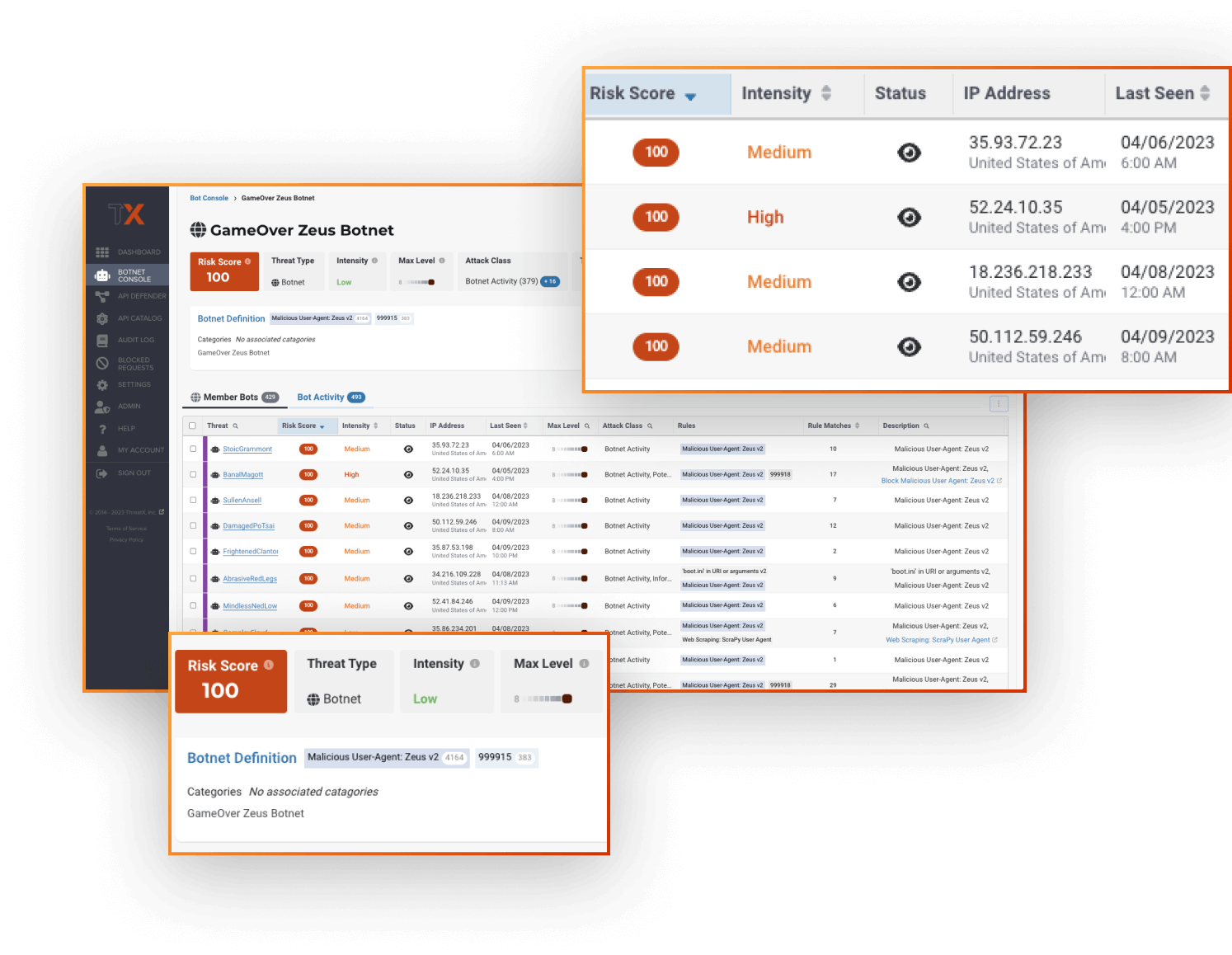
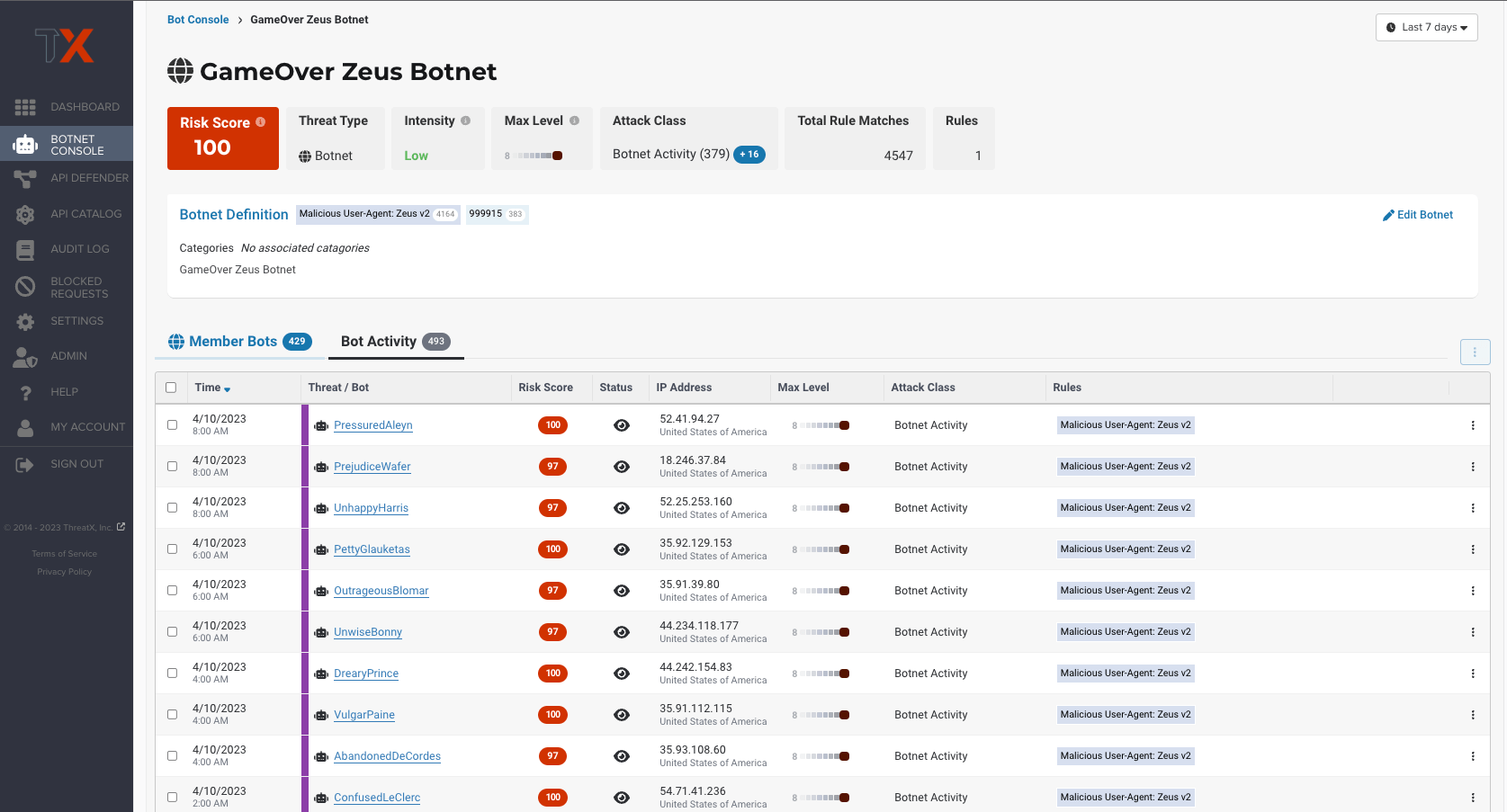
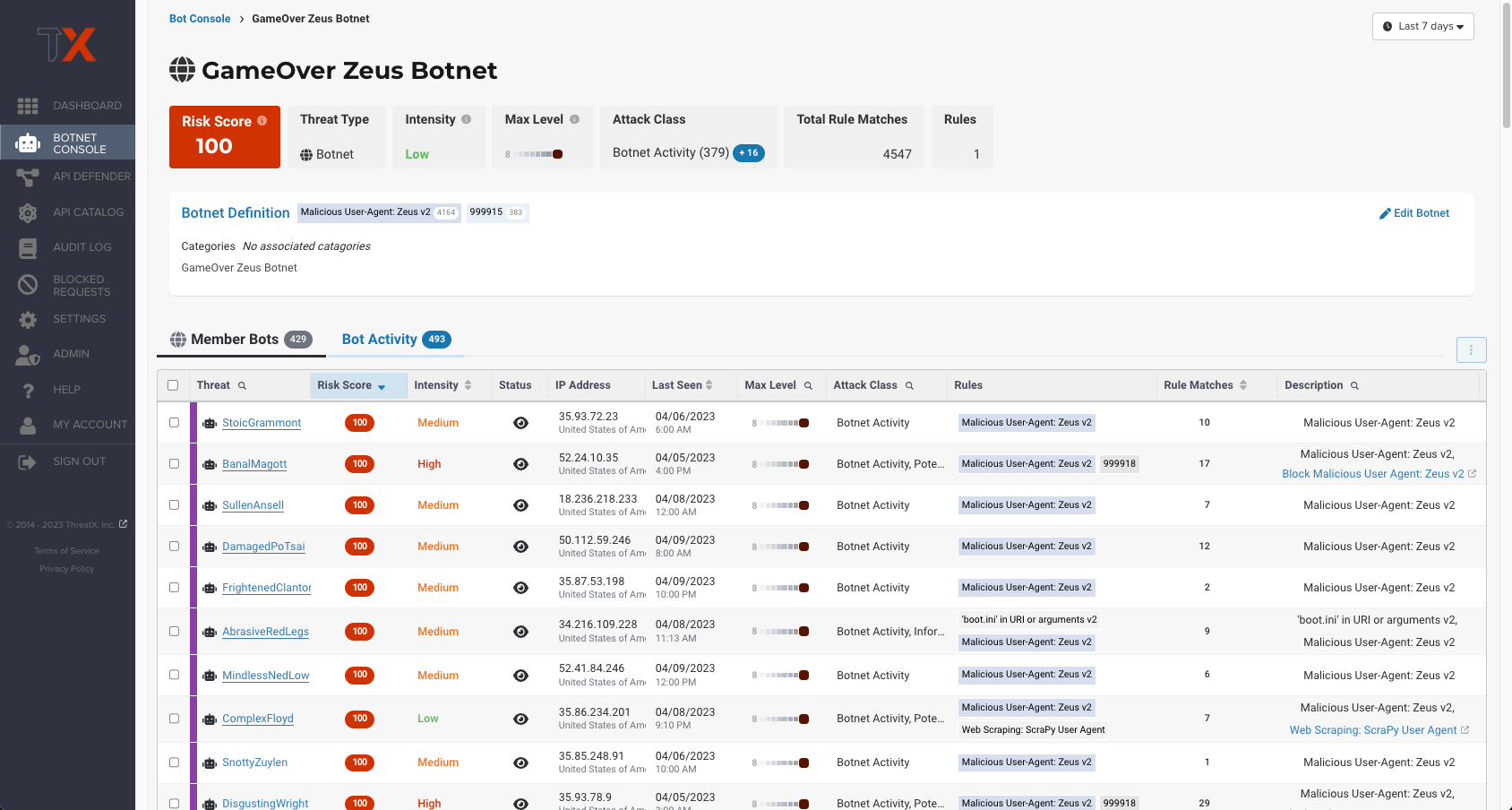
Bot Console & Analytics
Monitor all bot & botnet activity, at scale – without wading through complex dashboards
Stay ahead of advancing bots and botnets with real-time visibility and protection that evolves with changes in behavior. ThreatX’s botnet console & analytics provide an overview of all detected bot activity within one dashboard, allowing security teams to quickly identify the largest and most risky botnets generating malicious automated traffic. Track changes in attack behavior by drilling down into analytics for a specific botnet at a time, identify which member bots are generating the most noise or growing in intensity.
Advanced Bot Detection
Reliably detect malicious bot activity without impacting good bots or legitimate users
Using multiple detection methods, including IP fingerprinting, interrogation, and tarpitting, ThreatX detects bots with high confidence. By creating attacker profiles for every threat, ThreatX tracks attack strategies over time as attackers move through the attack kill chain. For example, if an attacker were using a bot to perform reconnaissance, and then came back a month later to attack, ThreatX will have the history to make a confident blocking decision.
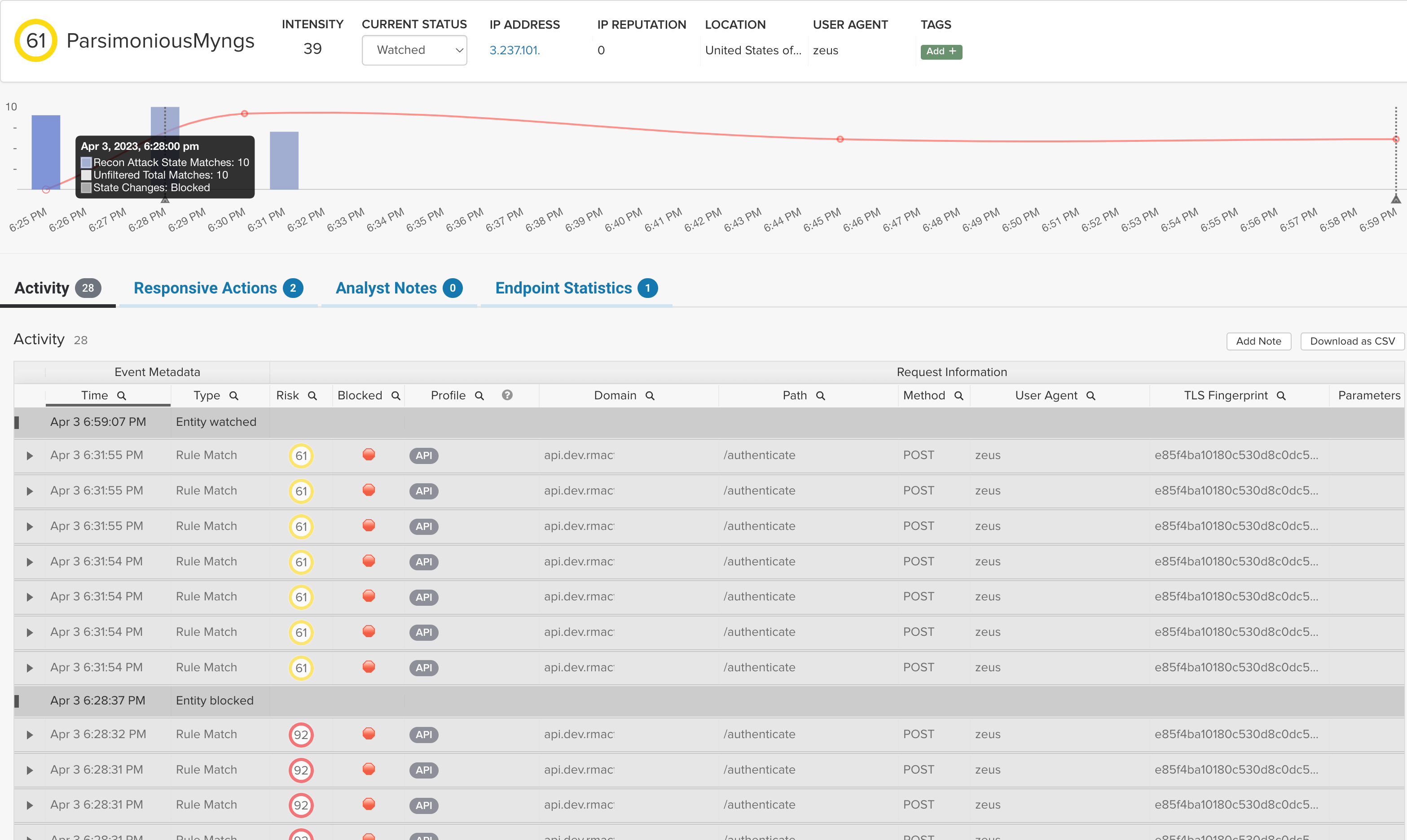
Risk-Based, Real Time Blocking
Detect and block bad bots in one platform, no transferring data between systems
ThreatX blocks malicious bots automatically, rather than giving you information to analyze then transfer to another solution for blocking. And we only block when the behavior reaches a certain risk threshold, so confidence is high and false positives are low. In addition, our risk scores evolve over time, continuously updating based on the latest observations, automating blocking as the risk score rises or falls.
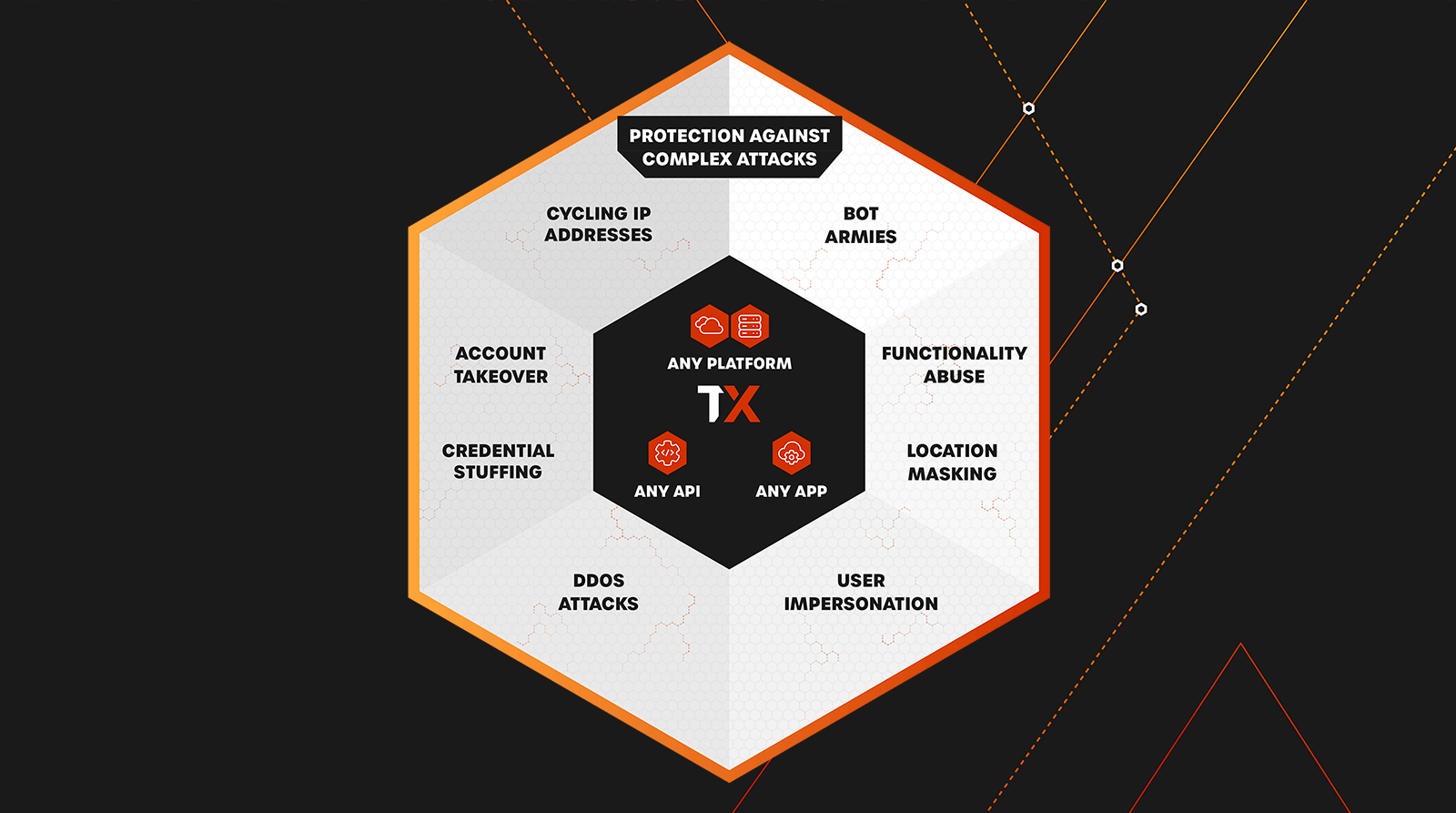
Automated Bot Protection
Stop even the most sophisticated botnet attacks without adding work for your team
Attackers are evolving their bot tactics and programming botnets to evade defense systems. For instance, many attackers today will program botnets to rotate IPs to avoid geo-blocking or integrate solver services to make botnets bypass specific bot management technologies.
ThreatX detects and blocks a wide range of advanced bot attacks including large-scale volumetric botnets, low and slow bot reconnaissance, as well as other forms of malicious traffic automation. By fingerprinting attackers and tuning detection criteria, ThreatX tracks threat actors over time, even when they cycle IPs or user agents, ensuring they stay blocked.

Key Benefits
Secure APIs and applications with Observability, Prevention, and Protection
Eliminate risks without compromising your time or peace of mind.

Easy-to-Use
Experience user-friendly security designed to focus on what matters most. Leverage simplified dashboards so you can effortlessly oversee your API and application’s security posture and risks.
Easy-to-Manage
Get your nights and weekends back with always-active security that ensures your APIs and applications stay safe. Our visionary technology provides continuous protection and prevention without the need for manual intervention. Enjoy peace of mind knowing that your APIs and applications are secure even when you’re off the clock.
Eliminate Risks
ThreatX solutions are always monitoring, assessing, and identifying risks to APIs and applications continuously based on behavior. Our technology learns to recognize threats and vulnerabilities specific to your system, and proactively stops them based on risk level. This ensures your business remains operational and efficient, without interruptions.
Frequently Asked Questions
Q: How does ThreatX manage bot traffic while detecting malicious bots?
A: ThreatX will give you insight into all bot traffic hitting your APIs and applications so that you can understand the full picture of your bot traffic. Using a dynamic risk score, ThreatX highlights malicious bots by incrementally increasing their risk score as more nefarious activity is registered. This allows users (and the ThreatX platform) to quickly understand which bots are likely to be threats, what they’re targeting, and if desired – block them.
Q: How does ThreatX prevent account takeover?
A: Key tactics to protect against account takeover include the following:
Active Interrogation of Visitors – Actively challenge visitors in ways that are completely transparent to valid users while reliably revealing malicious automation.
Fingerprinting and Entity Tracking – Advanced fingerprinting techniques can track attackers even as they change IP addresses, user agents, or other identifying characteristics.
Automated Deception Techniques – deceptive techniques such as fake fields that are readable to bots but invisible to users. Any interaction with these fields or functions can reveal that the visitor is a bot and not a human. Additionally, tarpit or further deceive attackers to monitor and observe ongoing malicious behavior.
Application Profiling and Behavioral Analysis – Baseline and monitor the normal behavior of applications. Since many ATOs rely on malicious automation, it’s important to be able to detect anomalous and suspicious application behaviors to reveal a previously undetected account takeover.
These techniques represent just a few of the techniques and countermeasures that ThreatX uses every day against account takeovers.
Q: Does ThreatX include any manual management?
A: Other than a quick DNS redirect and perhaps some implementation tuning for complex environments – ThreatX is fully managed Protection-as-a-Service. There are no manual tasks for users unless desired. ThreatX managed services are available for support 24/7/365.
Q: How does ThreatX differentiate between good and bad traffic?
A: ThreatX detection methods are primarily looking for indicators of attack. This focus on attacker-centric behavioral analysis combined with a flexible approach to permanent and temporary blocks allows the ThreatX decision engine to identify threats with a high degree of accuracy.
Q: How does ThreatX behavioral analysis work?
A: The ThreatX platform correlates seemingly disparate activity across numerous IP ranges back to single entities and tracks them over time. As these entities perform various activity across your APIs and web apps a risk score starts accruing for malicious or potentially malicious actions.