“Within 72 hours, we implemented ThreatX and successfully moved into blocking mode with no production impact. That’s a major game-changer for us.”
Security Architect, Global Retail Organization
View all case studies
“Within 72 hours, we implemented ThreatX and successfully moved into blocking mode with no production impact. That’s a major game-changer for us.”
Security Architect, Global Retail Organization
View all case studiesEasily secure any API or application with the freedom to adopt new technologies as needed. ThreatX is designed to be easy to deploy so that your team can get protection in place, even under the pressure of being attacked.
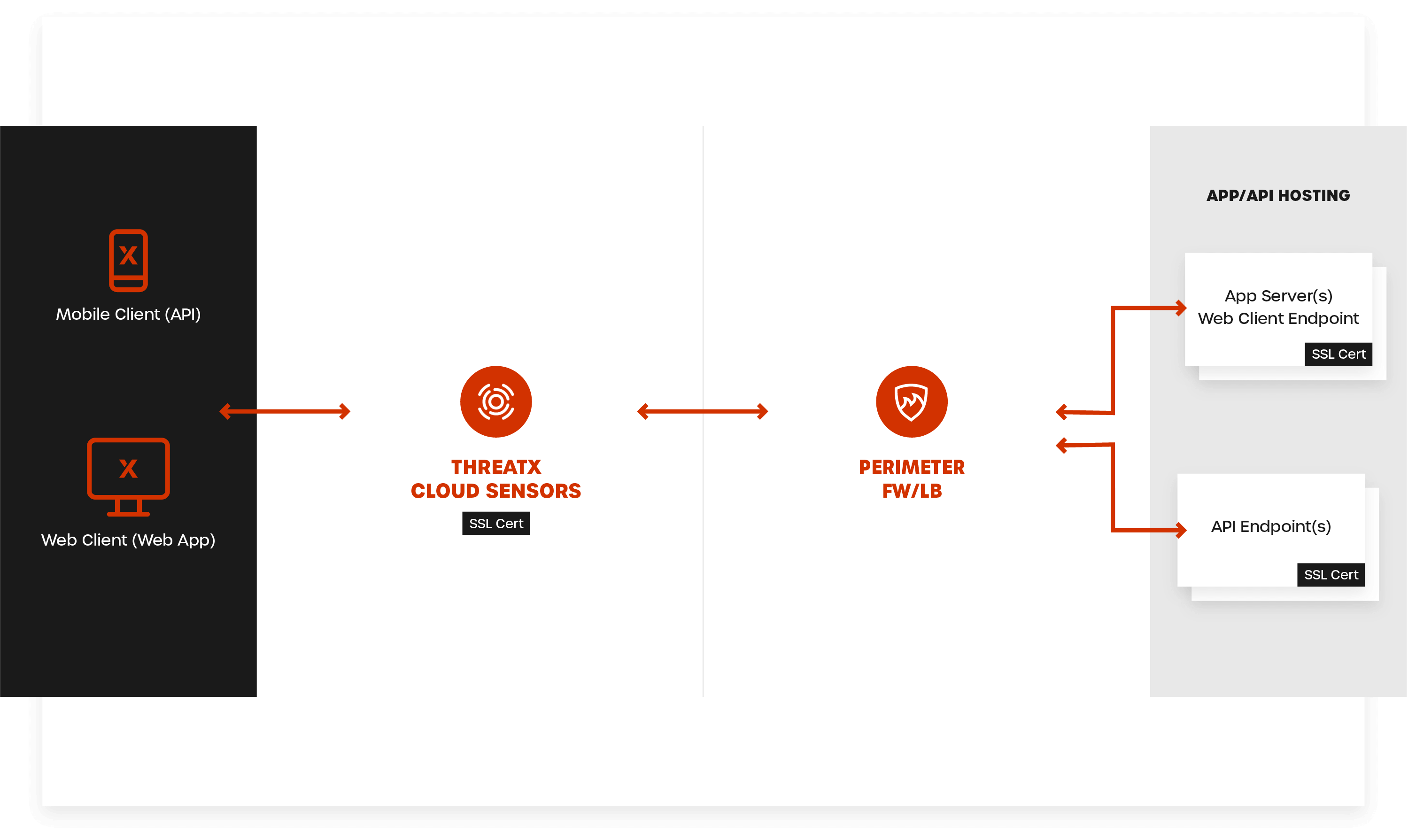
ThreatX offers a variety of deployment options to maximize our ability to easily protect any mix of APIs and applications, across any mix of cloud or on-prem infrastructure. You’ll never need to worry about slowing down innovation again.
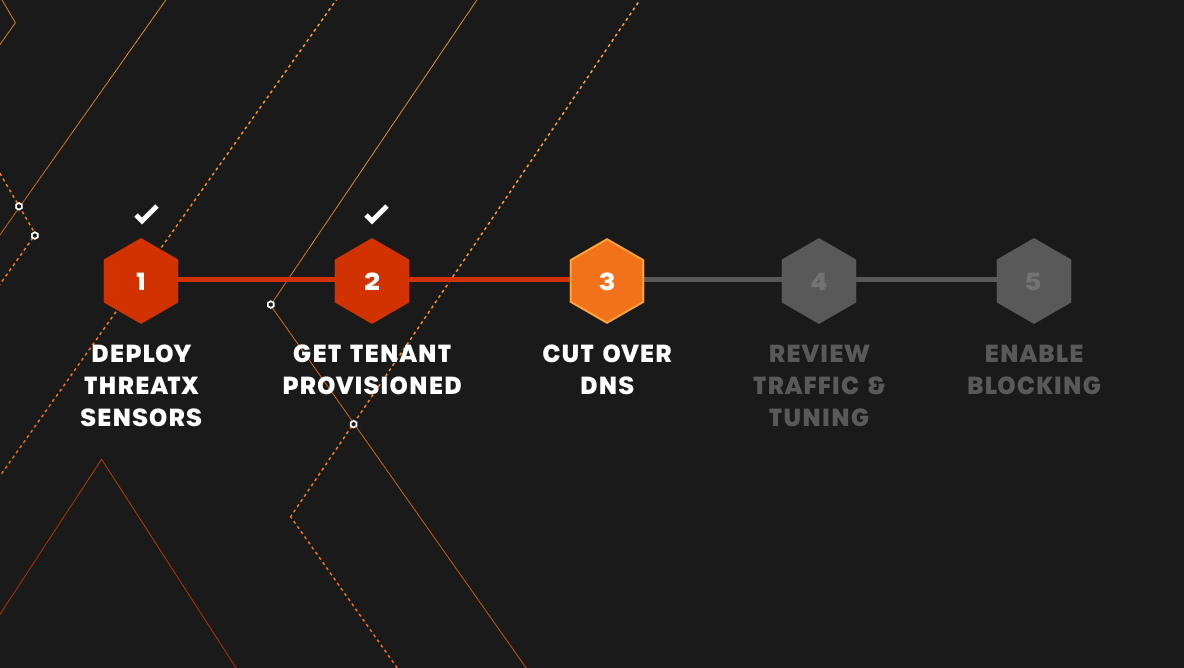
Attacks don’t operate on your schedule. In a world where downtime means lost revenue, protection you can be confident deploying and trusting is more critical than ever.
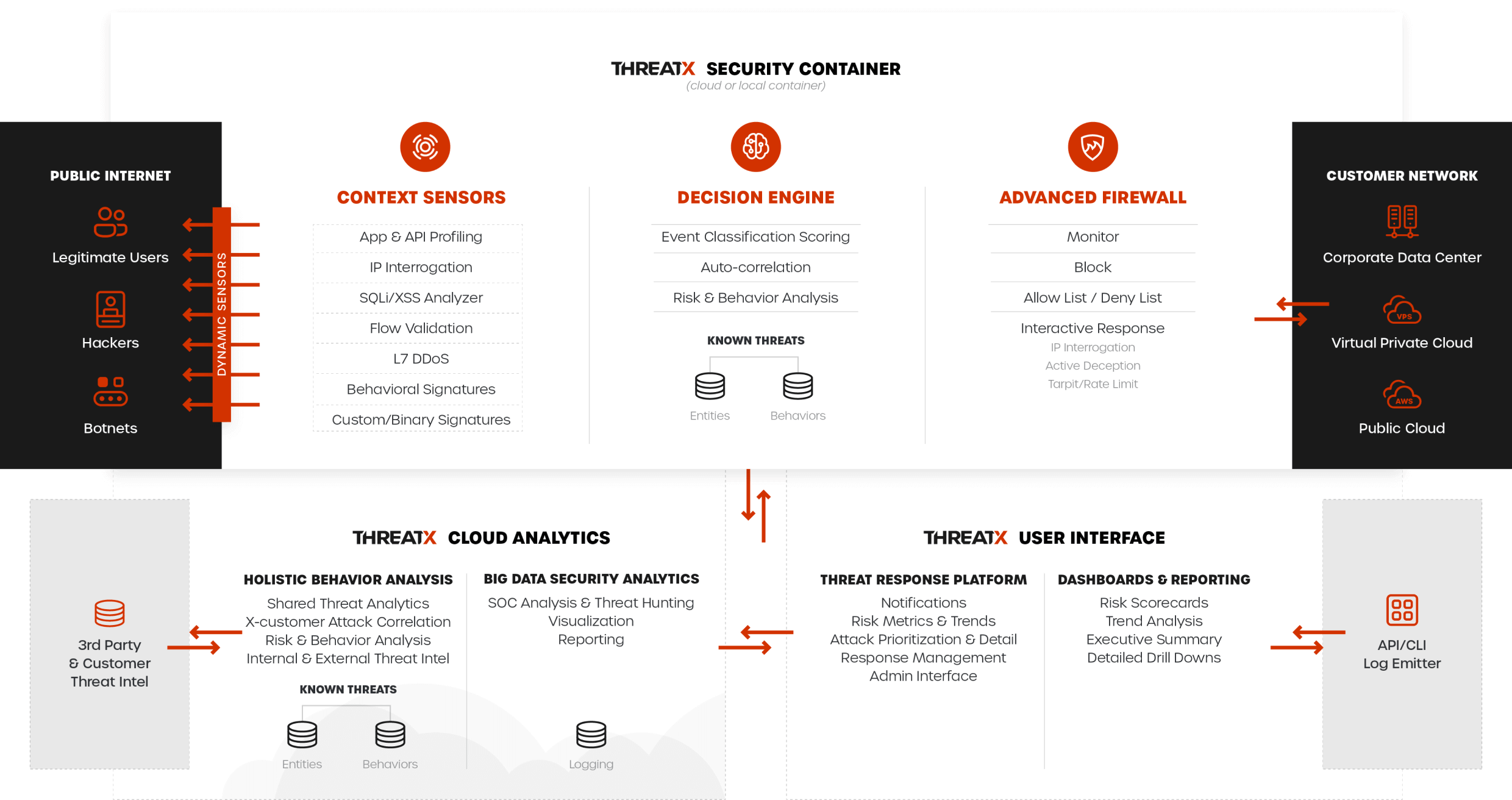
Cyberattacks also don’t follow patterns, so protection that can continuously monitor attackers over time, and provide defense against the widest variety of attacks, is critical.
ThreatX will give you protection out-of-the-box against the following and much more:
ThreatX recognizes the need for flexible deployment options that scale. Keep APIs and websites up and business humming with the ability to deploy in any region, and auto-scale across multi-cloud architectures or geographically dispersed application environments.

Key Benefits

Experience user-friendly security designed to focus on what matters most. Leverage simplified dashboards so you can effortlessly oversee your API and application’s security posture and risks.
Get your nights and weekends back with always-active security that ensures your APIs and applications stay safe. Our visionary technology provides continuous protection and prevention without the need for manual intervention. Enjoy peace of mind knowing that your APIs and applications are secure even when you’re off the clock.
ThreatX solutions are always monitoring, assessing, and identifying risks to APIs and applications continuously based on behavior. Our technology learns to recognize threats and vulnerabilities specific to your system, and proactively stops them based on risk level. This ensures your business remains operational and efficient, without interruptions.