“It’s been easy to work with the Protection-as-a-Service team. I feel, and the team feels, like they’re an extension of our information security team.”
Information security analyst at financial services organization
Read our case studies
“It’s been easy to work with the Protection-as-a-Service team. I feel, and the team feels, like they’re an extension of our information security team.”
Information security analyst at financial services organization
Read our case studiesProtecting running applications and APIs is an important part of a layered defense against zero-day vulnerabilities, because it blocks attacks while giving teams time to address vulnerabilities – without trying to keep up with attackers who are jumping on vulnerabilities and spinning up variants at a lightning-fast pace.
For example, in the aftermath of the Log4j zero-day vulnerability announcement, security engineers spent precious time analyzing HTTP requests to understand what attackers were targeting, what techniques they were using, and how they were going about it.
Take a self-guided tour of ThreatX Prevent
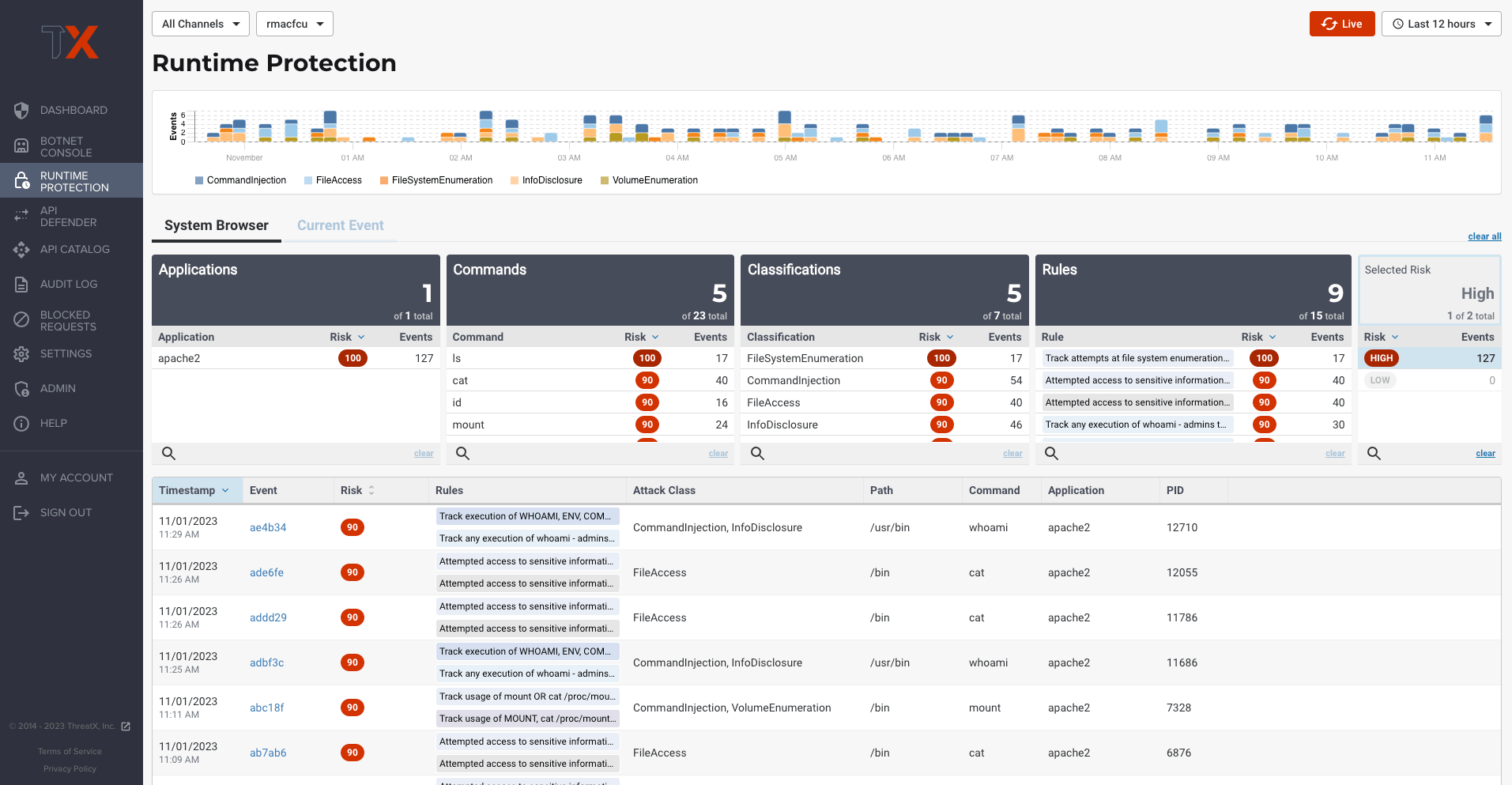

More vulnerable applications and APIs are being pushed into production every day –leaving user’s data and organizations at risk. The flexibility and ease of deploying cloud and containerized environments makes it easier than ever to add new capabilities but also introduce new vulnerabilities.
The ThreatX Prevent solution is deployed as a sidecar container within a Kubernetes environment. Leveraging extended Berkeley Packet Filter (eBPF) technology, ThreatX Prevent enables deep network flow and system call inspection, process context tracing, and advanced data collection, profiling, and analytics. With eBPF, ThreatX Prevent inspects all network traffic from one place – without requiring an in-line deployment.
Get more details on ThreatX API and App Runtime Observability.
Effective zero-day attack protection requires layers of defense – including constant research and analysis of emerging threats. ThreatX takes on this role for you with its Protection-as-a-Service team backed by ThreatX Labs research. Rest easy with our Runtime API and Application Protection backed by experts investigating and analyzing recent threats for you.
Learn more about the ThreatX Protection–as–a–Service team.


Key Benefits

Experience user-friendly security designed to focus on what matters most. Leverage simplified dashboards so you can effortlessly oversee your API and application’s security posture and risks.
Get your nights and weekends back with always-active security that ensures your APIs and applications stay safe. Our visionary technology provides continuous protection and prevention without the need for manual intervention. Enjoy peace of mind knowing that your APIs and applications are secure even when you’re off the clock.
ThreatX solutions are always monitoring, assessing, and identifying risks to APIs and applications continuously based on behavior. Our technology learns to recognize threats and vulnerabilities specific to your system, and proactively stops them based on risk level. This ensures your business remains operational and efficient, without interruptions.