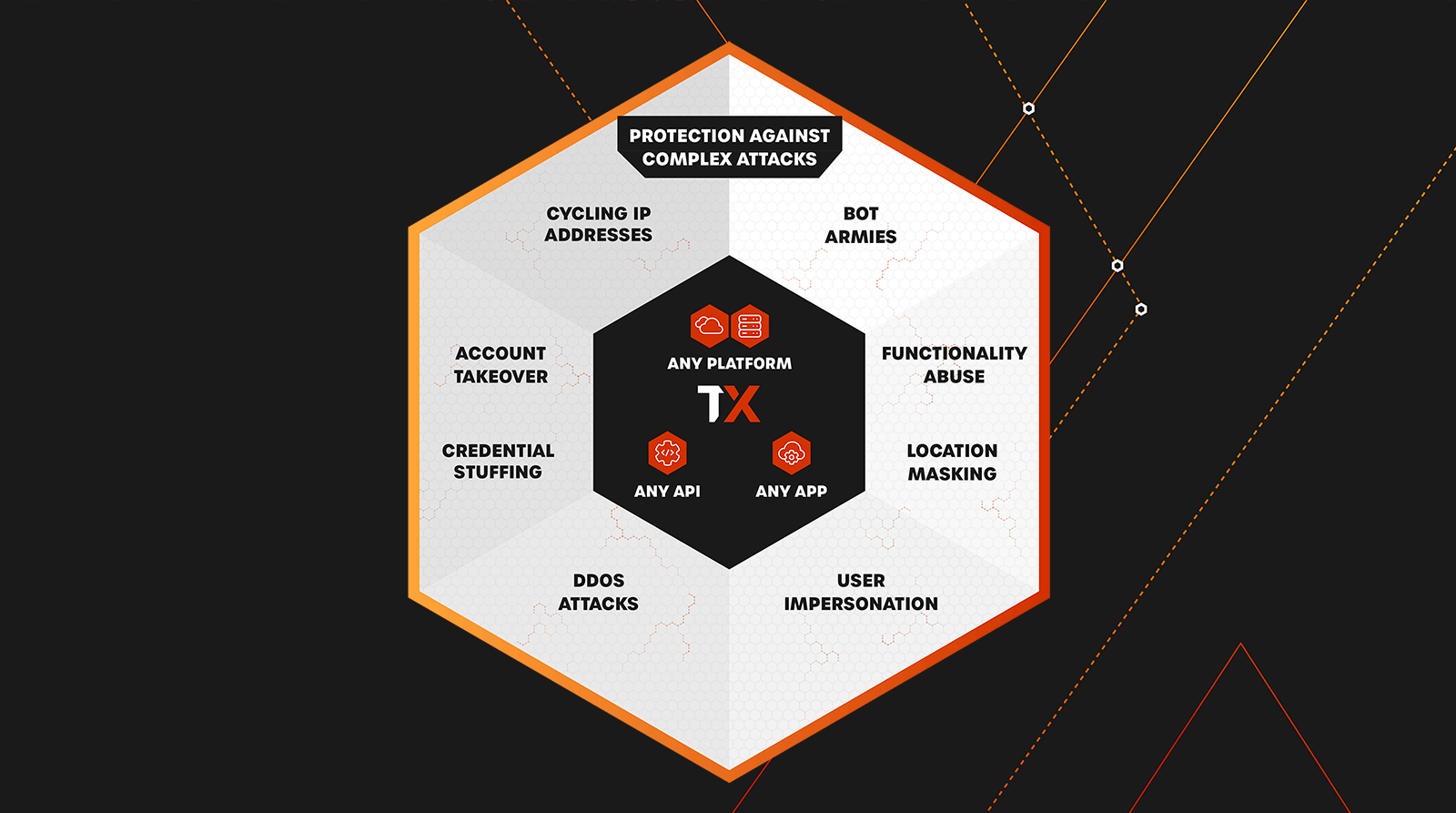
Struggling to Keep Up with Credential Stuffing Attacks?
Stop credential stuffing attacks at scale, without affecting your legitimate users.
ThreatX helps organizations defend against these fast-moving and elusive attacks by:
- Detecting Early-stage credential stuffing attacks
- Enabling teams to observe automated threats in real time
- Blocking attackers attempting to gain unauthorized access
Prevent unauthorized access and secure user accounts with early detection of credential stuffing along with risk-based, automated protection.
How We Help
Detect Early-Stage Credential Stuffing Attacks
Identify and block credential stuffing attacks without impacting users
ThreatX uses a combination of techniques to detect a wide range of automated threats, including credential stuffing, without introducing false positives or additional friction like CAPTCHAs. ThreatX challenges suspicious actors with active interrogation to see how they react when tar pitting traffic or returning web cookies. ThreatX also automatically profiles the application’s “normal” behavior by monitoring usage and underlying services, enabling early identifiers of credential stuffing attempts.

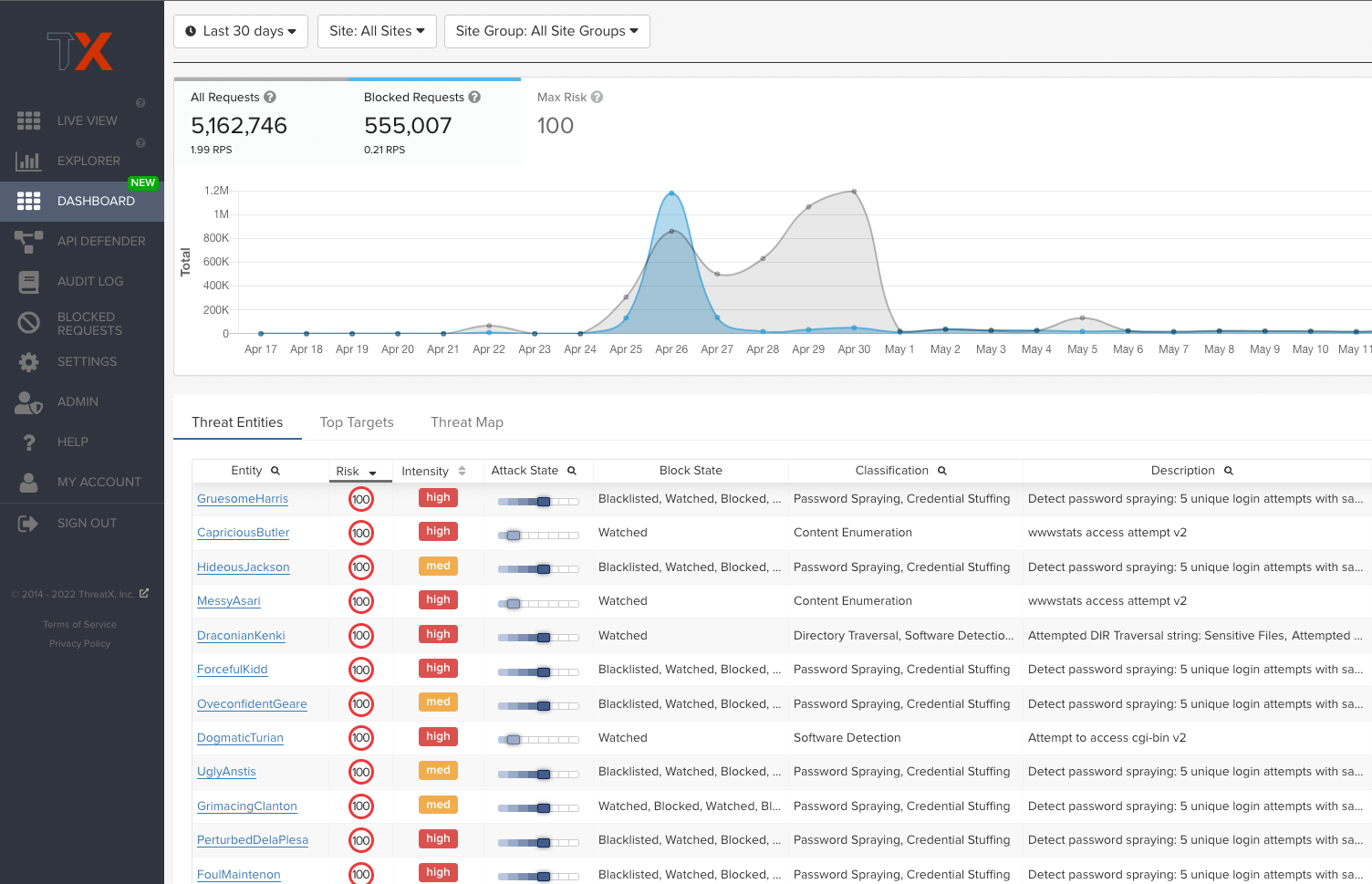
Observe Automated Threats in Real-Time
Monitor automated threats in real time to pinpoint and block bad traffic
ThreatX continuously monitors attackers and botnet activity as these threats progress over time to provide security teams with comprehensive behavior analytics and attack forensics. ThreatX uses attacker fingerprinting to track threat behavior over time no matter if they attempt to evade detection by cycling IP or user agents. It learns what threats to your system look like and stops them based on their risk level, so you can keep sites available and business humming.
Don’t Just Identify Attackers, Block Them
Stop unauthorized logins without disrupting legitimate users accessing their accounts
With ThreatX in place, organizations attempting to protect their login pages can finally block credential stuffing attacks effectively and accurately, without negatively impacting the experience of customers trying to access their accounts and ensure platform performance isn’t degregated. Given the increasing use of bots to carry out volumetric attacks, such as credential stuffing, account takeover, and DDoS, ThreatX is a necessity for our customers to maintain a strong security posture in today’s threat landscape with the platform’s automated risk-based blocking.

Key Benefits
Secure APIs and applications with Observability, Prevention, and Protection
Eliminate risks without compromising your time or peace of mind.

Easy-to-Use
Experience user-friendly security designed to focus on what matters most. Leverage simplified dashboards so you can effortlessly oversee your API and application’s security posture and risks.
Easy-to-Manage
Get your nights and weekends back with always-active security that ensures your APIs and applications stay safe. Our visionary technology provides continuous protection and prevention without the need for manual intervention. Enjoy peace of mind knowing that your APIs and applications are secure even when you’re off the clock.
Eliminate Risks
ThreatX solutions are always monitoring, assessing, and identifying risks to APIs and applications continuously based on behavior. Our technology learns to recognize threats and vulnerabilities specific to your system, and proactively stops them based on risk level. This ensures your business remains operational and efficient, without interruptions.