API & Application Protection for Financial Services
Secure the APIs and applications that manage your customers’ sensitive data and financial transactions with confidence – not complexity.
Effectively Block Threats Targeting FinTech, Banking, and other Financial Organizations
Segpay is in the digital payment processing space and, therefore, attracts a fair amount of cyberattacker attention. “We have this target on our back constantly,” said Segpay’s Director of Operations Marco Escobar. “And though the attackers haven’t been able to penetrate our systems, they’re becoming smarter, and more evasive.”
This past fall, Segpay experienced cyberattacks that featured bots inputting a series of different credit card numbers into the system to see if any would get approved. None of the attacks were successful, but Segpay did face thousands of transactions in a short period of time, which obviously required a time- and resource-intense response.
Segpay found that ThreatX’s behavioral threat detection gives them more accuracy and flexibility when bots are carrying out attacks by cycling through multiple IP addresses. ThreatX identifies the behavior as malicious and immediately blocks the attacker without having to block individual IP addresses – which can be both time-consuming and inaccurate.
“ We look at our ThreatX dashboard and pinpoint whether attackers are just getting their feet wet, or really trying to exploit us. It’s a good visual because we can see clearly what to focus on. With other solutions, it was just an immediate block for anything that met a rule. ”
What Our Customers Are Saying
We could see query strings, IP addresses, and details on attacker behavior that we couldn’t get from other solutions, and that helped us mitigate future risks. “
Senior Director of Operations | Segpay
We were spending a lot of weekends, late nights, and holidays managing these attacks. It seemed like these attackers would always take my Christmas Day, my New Year’s Day. I couldn’t sleep at night.”
Information Security Analyst | Global Financial Services Organization
ThreatX has been a game changer for my team and me, and has provided an additional layer of security for our members.”
Director of IT | Large Credit Union
With ThreatX, I’m in the console a lot, but not because I’m trying to troubleshoot and stop threats, I just like going in there and taking screenshots to show all of the blocks. “
Security Operations Manager | Large Banking Organization
Solutions

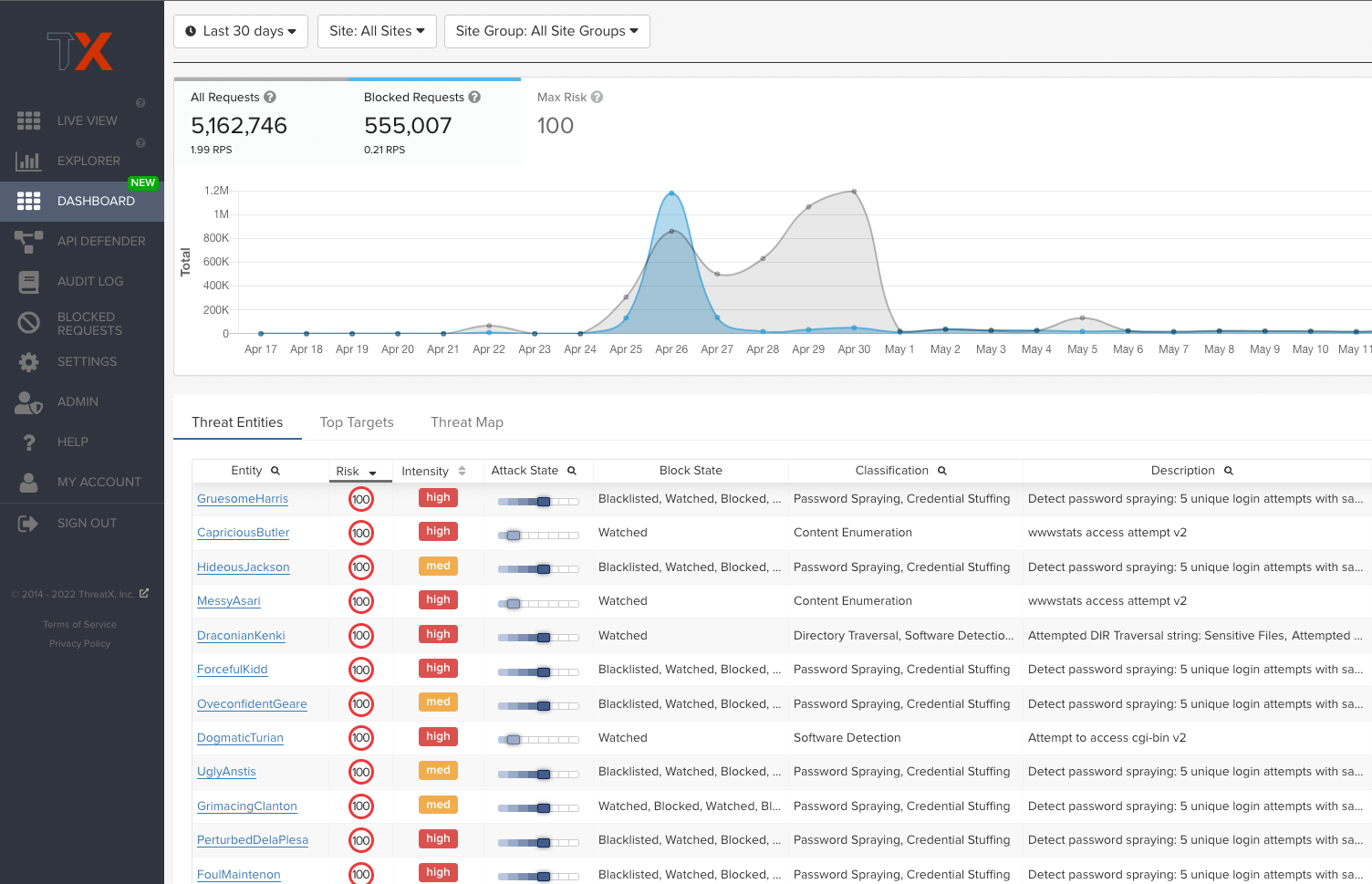


Immediately Protect Sensitive Customer Data
Secure your APIs and applications with real-time detection and blocking of complex attacks.
It’s best practice to build APIs and web applications as securely as possible from the start, but that’s not always an option, particularly for the legacy apps and APIs that many financial organizations have relied on for years. Defending your perimeter in depth has become table stakes, but finding the right partner that secures the full spectrum of your layer 7 traffic from nearly any threat is challenging. That’s why ThreatX exists.
We protect our customers from threats like:
- Credential Stuffing
- DDoS Attacks
- OWASP Top 10 Threats
- API Abuse
- Botnets
- Account Takeovers
- SQL Injection
- Zero Day Vulnerabilities
Learn more about how ThreatX helps protect high-risk APIs by taking a product tour Sensitive Data Exposure Tour.

Detect and Block Malicious Bots
Comprehensive coverage that scales against large, volumetric botnet attacks
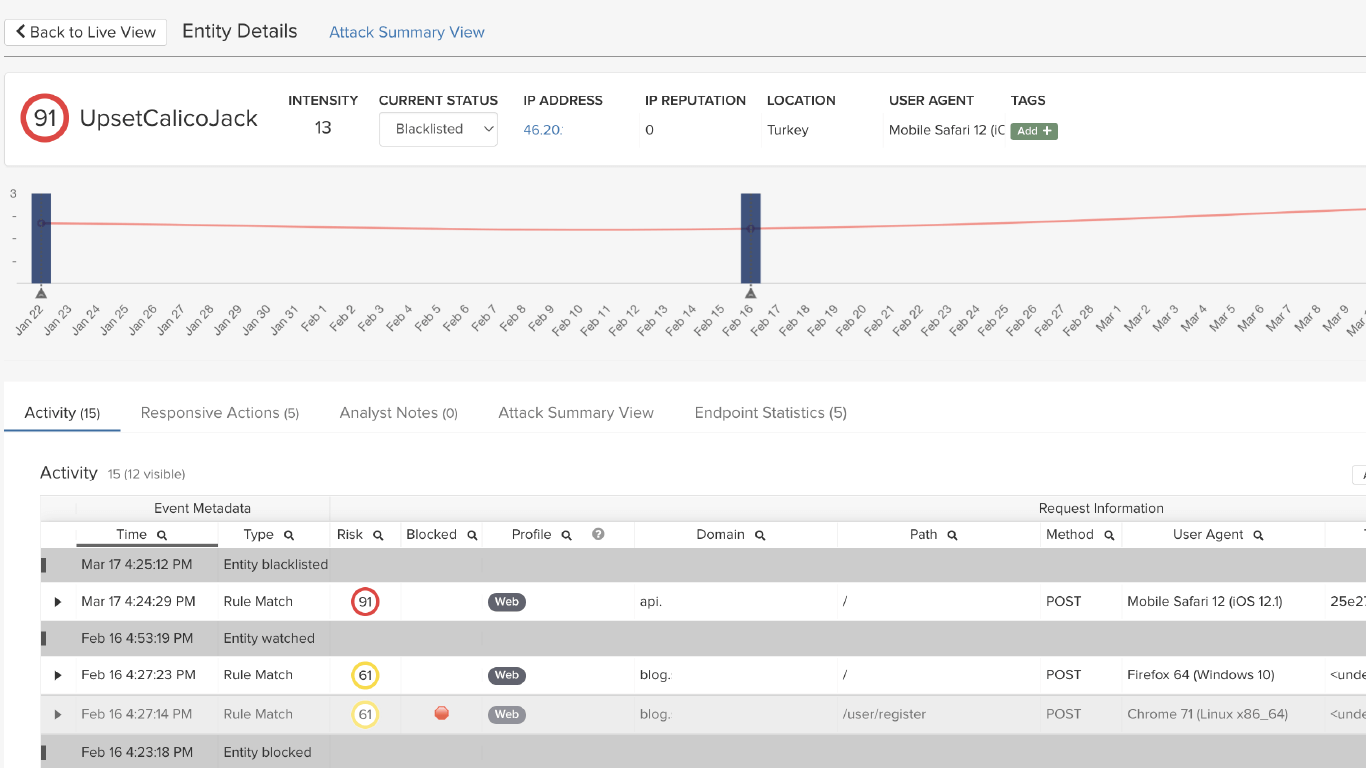
ThreatX provides critical visibility on bot-based attacks by using application profiling, IP interrogation, entity fingerprinting, and risk attribution to establish whether a sophisticated attacker is customizing malicious requests or if a distributed botnet is automating them. This combination of bot detection techniques and application intensity analysis means ThreatX can reveal a wide range of automated attacks such as ATO, credential stuffing, reputation attacks, and more.
Get comprehensive protection against:
- Brute force attempts
- TCP attacks
- HTTP flooding
- Spoofing
- Ping of death
- Smurf
- Teardrop
- Zero-day DDoS attacks and more…
Check out ThreatX’s approach to DDoS Protection & Bot Defense.

Prevent Fraud & Account Takeover Attempts
Risk-based blocking increases confidence that threats are blocked and legitimate users are never locked out
ThreatX goes far beyond signatures and anomaly detection with behavior-based analytics to identify and track malicious entities even as traits such as IP addresses and user agents change. This lets us track a complete picture of an entity’s attack attempts and risk so that enforcement is both highly accurate and laser-focused on what matter the most.
Benefits of this approach include:
- Fewer false positives
- Fewer custom rules
- Less time managing and mitigating rule conflicts
- Less time spent documenting rulesets
- Less resource requirements when FTEs change over
Learn more about our behavioral threat detection.

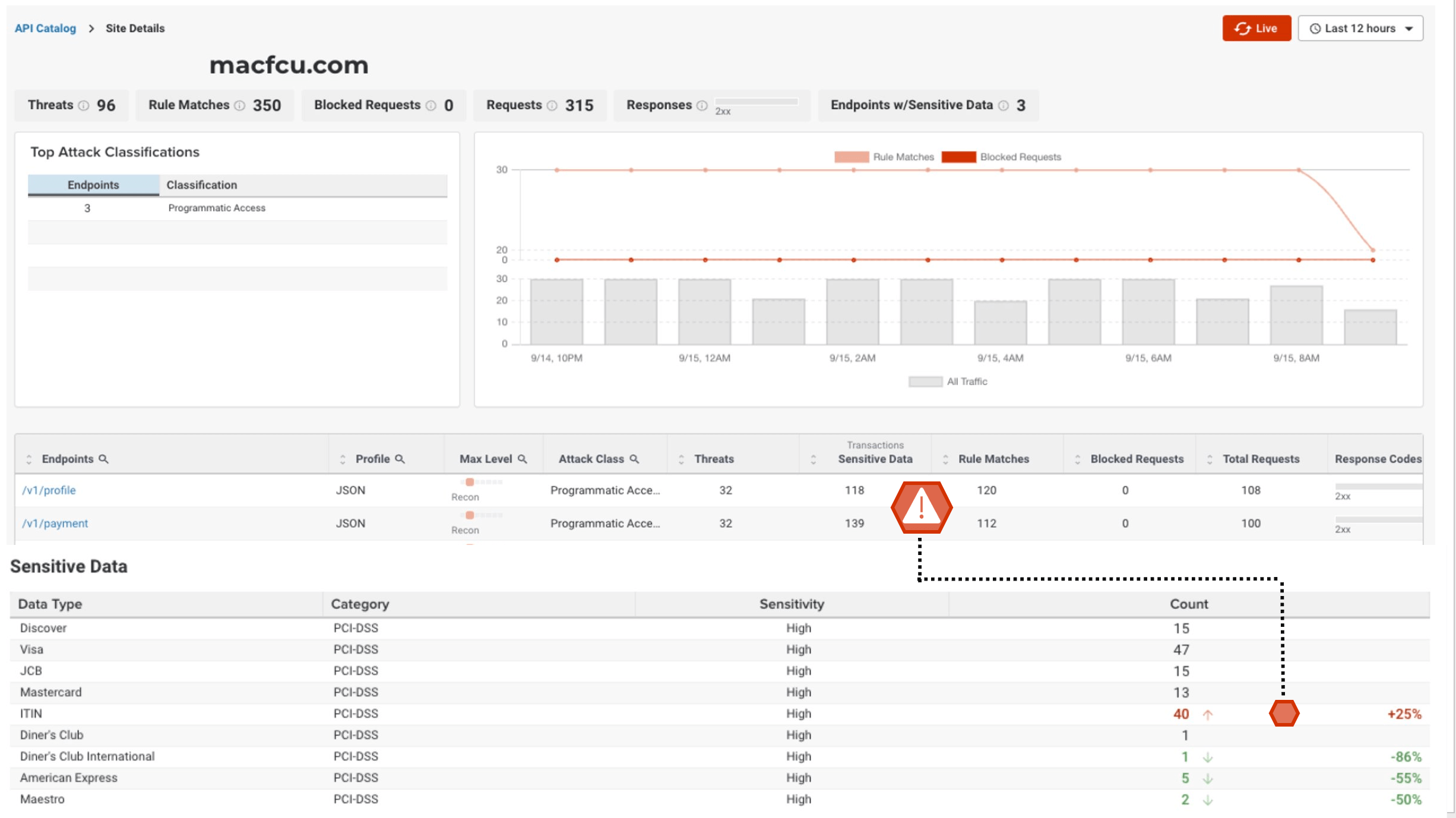
Wholistic View of API Attack Surface
Gain insight into your complete API attack surface with ThreatX’s API Catalog
ThreatX provides a comprehensive view of organization’s API attack surface and the threats targeting them. This empowers teams to manage APIs and investigate suspected abuse by leveraging advanced traffic analytics, metrics, and visualizations to track attackers down to specific endpoint transactions.
Benefits include:
- Visualize sites powered by APIs
- Visualize API’s endpoint traffic
- Track API usage vs. malicious traffic
- Less time understanding API traffic
- More confidence to block API abuse
Learn more about our API threat protection capabilities.

Meet PCI Requirements Consistently and Efficiently
Secure all systems that manage your customers’ personal identifiable and cardholder data while reducing the burden of maintaining compliance.
ThreatX helps you meet PCI requirements, but also improves the overall security of application and cardholder data while reducing the burden of maintaining compliance.
This includes help with the following PCI requirements:
- Requirement 6: Develop and Maintain Secure Systems and Software
- Requirement 1: Install and Maintain Network Security Controls
- Requirement 5: Protect All Systems and Networks from Malicious Software
- Requirement 10: Log and Monitor All Access to System Components and Cardholder Data
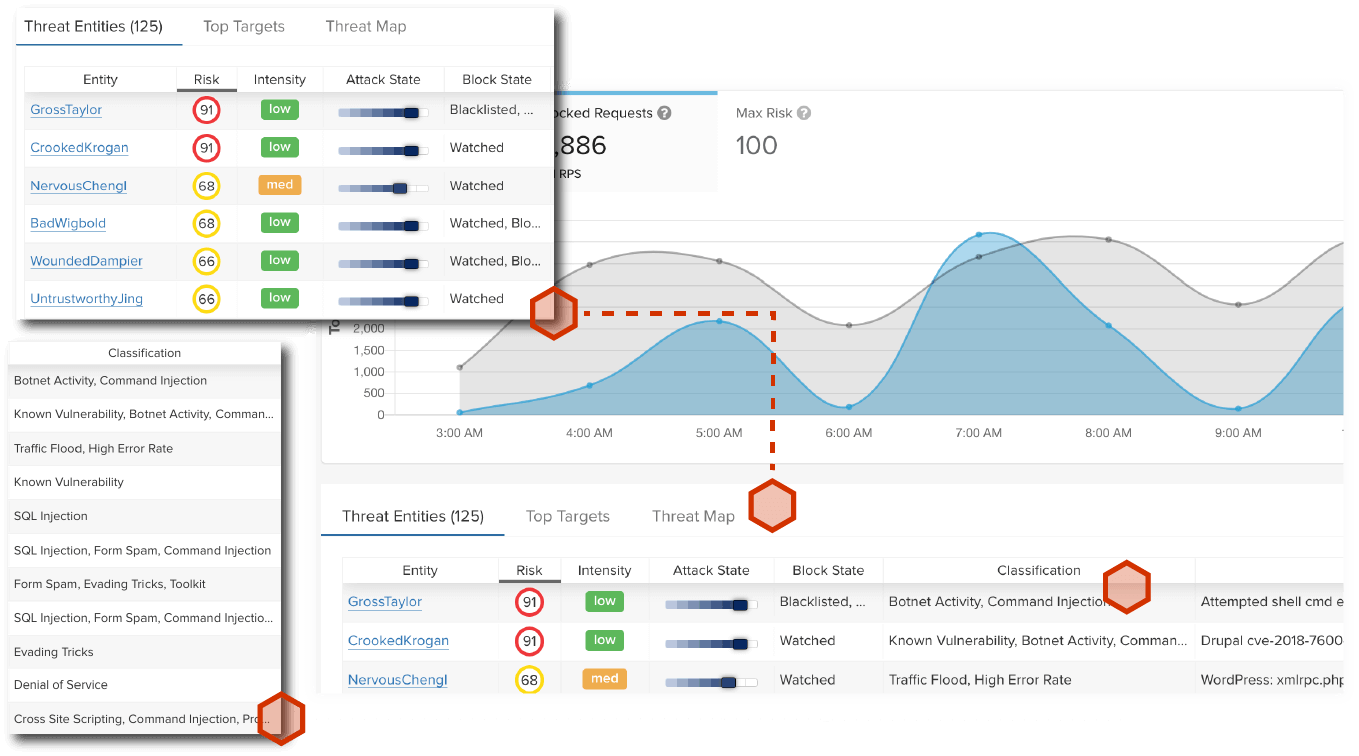
A Unified API & Web Application Protection Platform
Secure the APIs and Web apps that manage Financial Transactions

