Need a DDoS Protection Solution Deployed Fast?
Immediately shut down DDoS attacks targeting your APIs and applications. Quickly restore your websites and services and ensure they remain protected against future threats.
- Set it and forget it DDoS mitigation
- Protect APIs and applications against DDoS, botnets, and more
- On-board sites and APIs in minutes
- Fully Integrated DDoS Protection That Scales
Managed DDoS protection for APIs and applications that deploys quickly and easily across multi-cloud environments
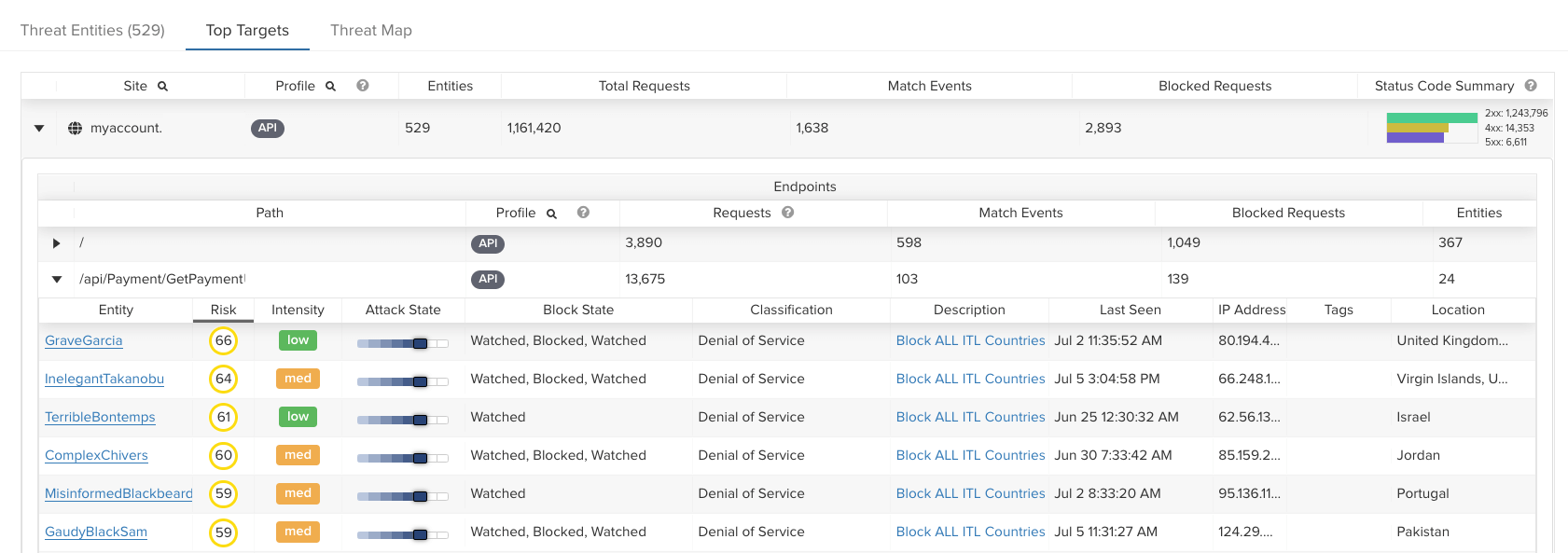
How We Help
DDoS Attack Mitigation
Out-of-the-box protection against DDoS attacks without endless configuration and rule management
Busy teams with few resources need solutions that provide value fast and don’t require on-going maintenance. ThreatX is purpose-built to help you do more with less. Deploy in minutes, with protection from day one to immediately block attacks.
Once ThreatX is in place, you’ll be able to leave those sleepless nights behind. As a fully managed platform, our experts will have your back and ensure your websites and services remain protected.

Fully Managed, With 24/7 Support
Leave the details to our experts so you can focus on your most important projects
ThreatX is available as a fully managed service, to any customer. Our team of experts are available 24/7 to support any issues you face or answer questions you have. In addition to consultation, our managed services team helps our customers by:
- Actively monitoring for threats in real-time
- Alerting you to suspicious or malicious-looking anomalies
- Proactively responding to zero-day threats
- Quickly deploying and configuring ThreatX protection
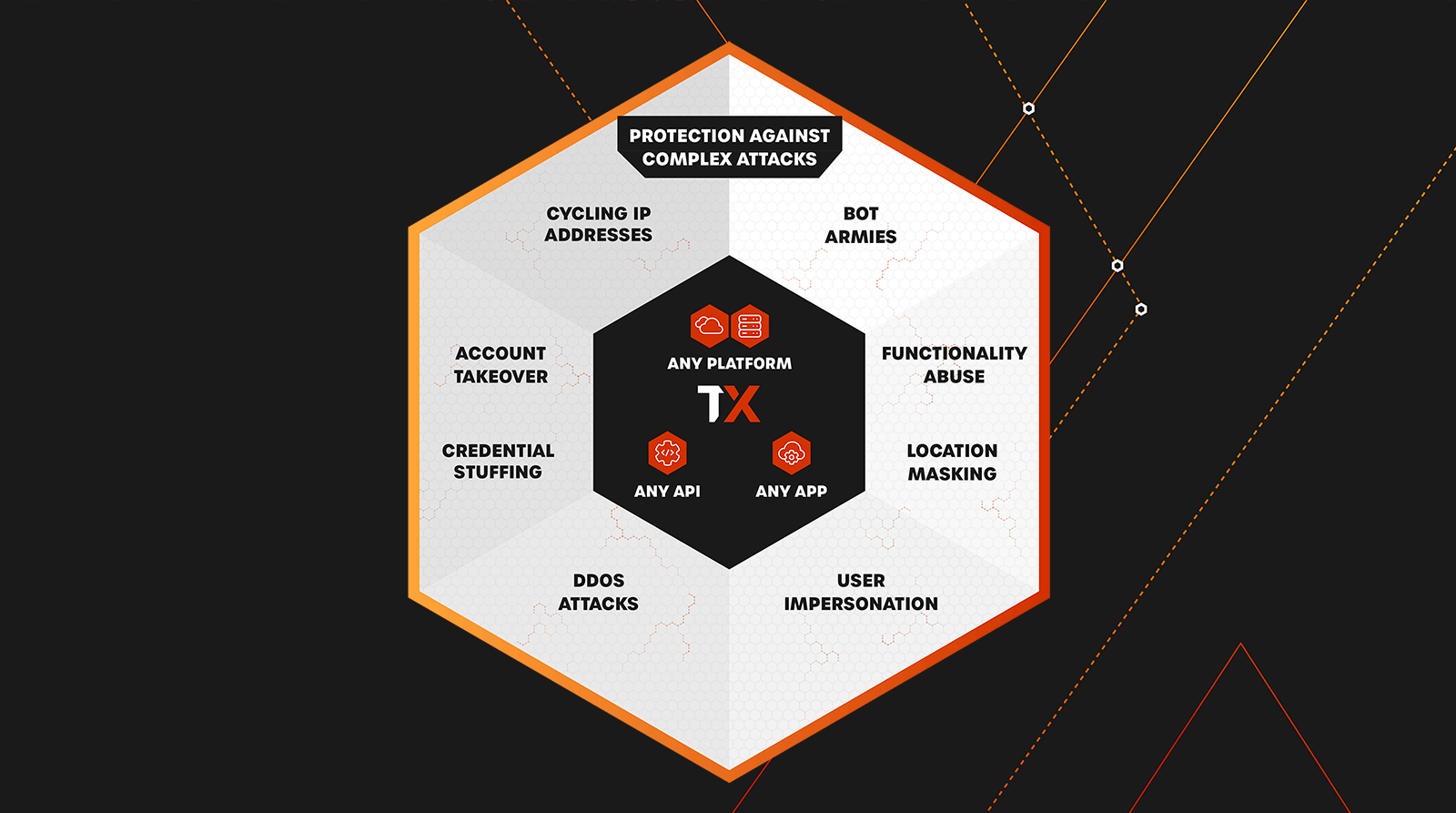
In-Depth DDoS Prevention and More
Defend against any threat targeting APIs and applications without managing multiple products
Simplify your stack and protect your APIs and applications against DDoS attacks.
You’ve also got more to worry about than DDoS. Attackers are constantly changing tactics and finding new exploits; you should have protection that meets this challenge. With ThreatX in place, you’ll also be protected against all manner of attacks, including malicious bots, credential stuffing, account takeovers, along with standard OWASP and OWASP API Top Ten attacks.
Our fully managed protection platform will allow you to protect more with less, and ensure your team isn’t left scrambling in response mode from one incident to the next.

Key Benefits
Secure APIs and applications with Observability, Prevention, and Protection
Eliminate risks without compromising your time or peace of mind.

Easy-to-Use
Experience user-friendly security designed to focus on what matters most. Leverage simplified dashboards so you can effortlessly oversee your API and application’s security posture and risks.
Easy-to-Manage
Get your nights and weekends back with always-active security that ensures your APIs and applications stay safe. Our visionary technology provides continuous protection and prevention without the need for manual intervention. Enjoy peace of mind knowing that your APIs and applications are secure even when you’re off the clock.
Eliminate Risks
ThreatX solutions are always monitoring, assessing, and identifying risks to APIs and applications continuously based on behavior. Our technology learns to recognize threats and vulnerabilities specific to your system, and proactively stops them based on risk level. This ensures your business remains operational and efficient, without interruptions.
Why do you need Managed DDoS protection solutions?
Savvy attackers know that they can map your applications to understand which pages or API calls consume resources such as memory, session handles, or CPU cycles. Armed with that information, they can design a sophisticated, multi-mode attack to consume resources, degrade your app’s performance, and generally muddy the waters while trying more pointed exploits. This is the outline of the modern distributed denial of service attack (DDoS) which requires DDoS protection that never sleeps!
How does ThreatX work?
ThreatX provides attack protection against complex, multi-mode attacks including API abuse, distributed botnets, and DDoS attempts by delivering real-time protection on a scalable platform. ThreatX defends organizations from many forms of modern DDoS attacks and is one of the key pillars of an attacker-centric security solution.
Our attacker-centric behavioral-based detection protects organizations from today’s increasingly prevalent Layer 7 (application-layer) DDoS attacks. ThreatX also has many customers that rely on our platform to scale and power protection against large-scale volumetric (Layer 3 and Layer 4) DDoS attacks.
ThreatX DDoS Protection solution – Key features
- Sophisticated bot detection driven by behavioral analytics, active interrogation, and application analysis
- Automated blocking driven by risk-based scoring that ensures both extremely low false positives and low false negatives
- AI and ML single risk engine that detects and correlates threats across all API and web app assets by analyzing attacker behavior
- Managed services and security operations assistance, to ensure our customers get the highest protection possible from the ThreatX platform
- Real-time detection and blocking, deployed in-line as a reverse proxy to instantly stop DDoS attacks
Comprehensive Multi Layered Protection against multiple DDoS Attack vectors
Attackers will often throw all these attack types together, into a sophisticated multi-mode attack, spanning tens of thousands of bots. You need protection that covers all the bases.
Legacy, low-level DDoS attacks, such as:
- Reflected ICMP & UDP attacks
- ICMP and Ping floods
- UDP floods
- Mixed SYN + UPD or ICP + UDP floods
- Ping of Death
- ICMP Echo attacks, aka Smurfing
Layer 3 attacks:
- TCP SYN+ACK floods
- Bulk TCP resets
- TCP ACK floods
- TCL ACK + PSH attacks
- TCP fragment attacks
Layer -7 attacks:
- HTTP flood attacks
- Connection floods
- Zero-day exploits
- CVE exploits
Behavioral attacks, including:
- Suspicious or malicious bot traffic
- Brute force
- Spoofing
- Teardrop attacks
Why ThreatX for DDos Protection?
ThreatX uses a combination of entity analysis, active interrogation, and application analysis to distinguish bots from true human visitors. It starts by tracking an entity’s behavior across many attempts, and if activity seems suspicious, ThreatX will engage with potential threats via active interrogation techniques like injecting fake fields or tarpitting traffic to see how the threat responds.
Other detection techniques allow for detailed fingerprinting and analysis of the host, and ongoing tracking allows the ThreatX platform to differentiate legitimate machine-to-machine communication from suspicious or malicious bot traffic.
Lastly, application analysis tracks how a threat is attempting to interact with an application. To detect and protect against large-scale botnet attacks — a powerful tool in DDoS attacks — ThreatX continuously analyzes the intensity of traffic to alert staff of any significant influxes of suspicious traffic and deliver seamless but effective DDoS protection.
DDoS Protection FAQs
Does ThreatX provide DDoS Protection service?
ThreatX also provides additional DDoS services for customers with high-bandwidth or service-level requirements. ThreatX partners with multiple enterprise-class L3/L4 DDoS providers with extremely large infrastructures capable of absorbing multiple-terabyte attacks. ThreatX actively manages these services through our 24×7 SOC, working with partners to identify and mitigate even the largest attacks in real time.
How does ThreatX protect against new DDoS attacks?
DDoS attacks are often unpredictable and, by design, they strike at the most inopportune times. All ThreatX DDoS services are supported in real time by a dedicated team of highly trained application security experts. This means that even as situations and adversary techniques change, the ThreatX team is on the job to diagnose problems and respond in real time.