LAST UPDATED April 30, 2024
In today’s fast-paced world, where code is continuously pushed to production, many DevSecOps teams struggle to manage and prioritize API vulnerabilities. There are many Application Security Testing (AST) tools on the market, but they all fall short in providing one essential element: real-time, production level monitoring. Without this, comprehensive API security, from code to runtime, cannot be easily obtained.
Lacking this crucial element leads to:
Insufficient Testing Scope
Manual setups for API testing often result in inadequate coverage, missing real-time insights that are crucial for comprehensive protection. During application runtime, the data collected can differ significantly from what was available at development, creating a disconnect. This gap between runtime behavior and initial documentation leads to challenges in maintaining accurate, up-to-date comprehensive testing plans.
Fragmented Comprehension of APIs & Usage
The understanding of APIs and their usage is fragmented because a combination of different tools (DAST/SAST/IAST) is needed to paint the full picture of vulnerable APIs in both production and pre-production applications. Often, DevSecOps teams will utilize multiple testing tools and engage in manual data consolidation efforts to ensure comprehensive visibility is achieved. Furthermore, maintaining API documentation is a constant challenge, as it requires continuous updates to align with the ever-evolving application features and the discrepancies observed between development and actual runtime data.
Lack of Insight into Zero-Day Exploits
There is a lack of deep insight into zero-day exploits, as there is a difficulty in detecting vulnerabilities that were previously unknown. Moreover, there is not enough data available to properly train and refine predictive security models, which are crucial for proactively addressing zero-day exploits before they can be exploited.
These few factors emphasize the importance of adopting an integrated, real-time observability solution that connects the dots between identifying vulnerabilities in pre-prod applications and during actual production. These considerations were a strong impetus for the ThreatX Team to intervene.
Our Runtime API & Application Protection (RAAP) solution utilizes eBPF technology to provide always-active API security with persistent observability into network and runtime traffic data exchanges, threats, and vulnerabilities in real-time. By leveraging these insights and analyzing the traffic, we can identify current usage patterns and potential weaknesses in API endpoints, including zero-day vulnerabilities. We can then execute targeted, dynamic API test scans for pre-prod and production applications. This method allows us to be more aggressive in identifying potential vulnerabilities while adding confirmation to minimize false positives and unnecessary alerts.
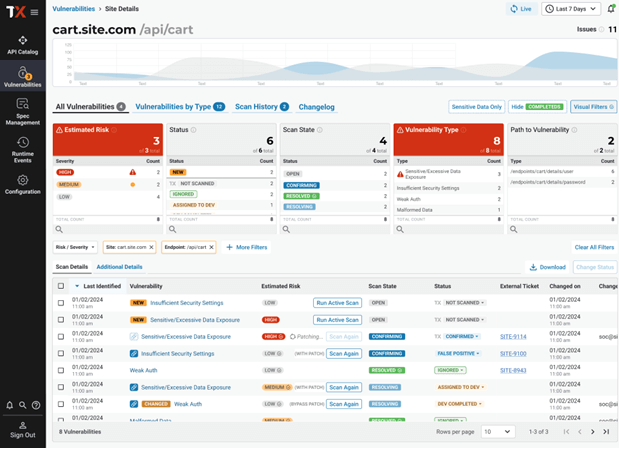
Our comprehensive Vulnerabilities Dashboard provides DevSecOps a holistic view of vulnerable APIs in pre-prod and production applications with workflows to address them including, virtual patching at the edge and integrations with development team’s ticketing systems. This approach ensures both development and security teams have one unified solution to identify, prioritize, and manage vulnerabilities to keep their digital assets secure.
To learn more about ThreatX’s Runtime API and Application Protection (RAAP) and vulnerability management for always-active API security, request a personalized demonstration HERE.
