LAST UPDATED December 21, 2023
Runtime threats aren’t new, and runtime protection is not a new concept. But it’s been plagued with significant challenges over the years. eBPF isn’t new either, but it offers new hope for the challenging problem of runtime API and application protection.
The challenges of runtime protection
The term runtime application self-protection (RASP) was coined in 2014. However, obtaining visibility beyond HTTP has proven difficult and the technology has not always lived up to its promise. RASP solutions required teams to deploy an agent for every tech stack and component, making deployment burdensome and maintenance untenable. The agents needed to run constantly, and the high CPU load impacted performance and increased the cost to run applications.
Alternative approaches to obtaining runtime visibility required teams to deploy kernel modules, which essentially meant installing code that had root access deep within the kernel. Thus, using kernel modules added risk and instability, putting the OS at risk.
Get our new whitepaper that covers All You Need to Know About Protecting Against Runtime Threats to APIs and Applications.
Bringing visibility to runtime threats with eBPF
To be effective, runtime protection must allow a security technology to monitor events in the processes running on the application host — without impacting application performance, introducing risk, or increasing operational overhead. Today, eBPF makes that possible.
Extended Berkeley Packet Filter (eBPF) is a framework that extends the ability to attach at the kernel level within a Linux environment. The advanced Linux kernel technology enables real-time performance monitoring, networking, and security. It allows developers to create programs in user space and inject them into kernel space without modifying kernel code, providing low-impact, adaptable solutions for various use cases – one of those being runtime threat protection.
eBPF provides real-time, detailed kernel-level monitoring, enabling comprehensive insights into system components and activities. eBPF is ideal for runtime threat protection because it allows you to safely peer into that kernel-level data, without modifying the kernel, and stop malicious processes and infected containers without any performance degradation.
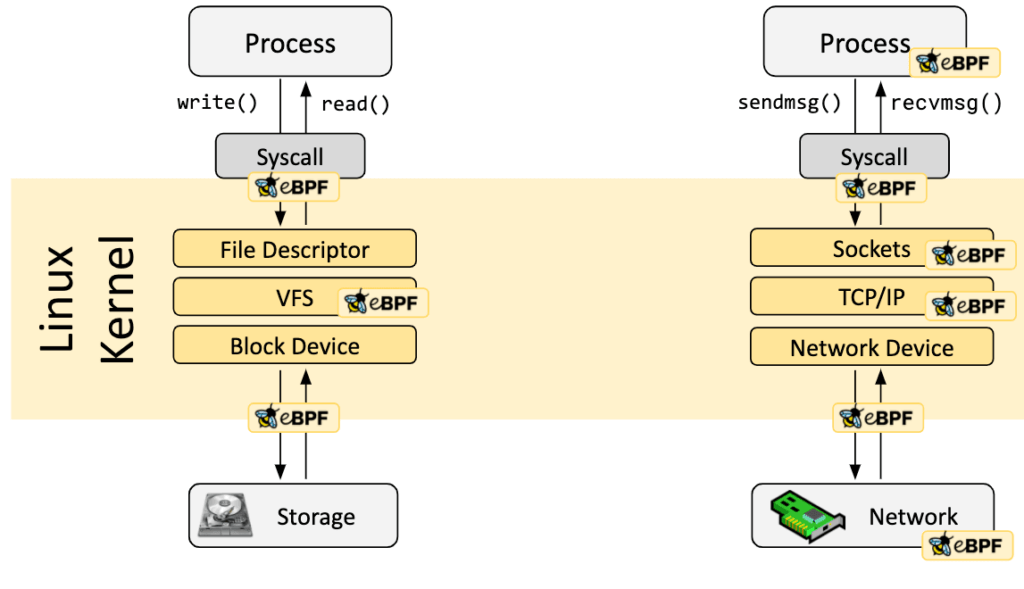
Source: https://ebpf.io/what-is-ebpf/
Note: eBPF is a capability built specifically to allow access to kernel-level activity, but in a safe, sandbox environment — an environment that has to be validated by the kernel so that you cannot cause any kind of outages or performance interrupts.
Runtime protection leveraging eBPF can monitor events in the processes running on the application host. As a result, it provides a lot more data beyond typical HTTP, from monitoring at the kernel level, seeing all the way down to network flows, the process tables, arguments, environment variables, etc. eBPF can monitor and analyze traffic patterns and perform packet inspection associated with protocols. It can also correlate with process monitoring and command line to detect anomalous process execution and command line arguments associated with traffic patterns (e.g., monitor anomalies in use of files that do not normally initiate connections for respective protocols.) In this way, if an anomaly occurs in the monitored events that appears to be related to any traffic that goes through the WAF, a security team could take action.
Ultimately, the benefits of eBPF include:
- Advanced Linux kernel technology for real-time monitoring and security
- User-kernel bridge allows seamless program integration
- Low impact, custom security rules, and improved visibility
- Ideal for diverse use cases, including networking and observability
- Cloud-native support for securing modern infrastructures
- Highly efficient with minimal system resource requirements
Learn more about how ThreatX is leveraging eBPF for runtime API and application protection
Visit ThreatX Booth 3028 at the 2023 Black Hat Conference August 9 and 10 to get a demo of ThreatX Runtime API and Application Protection.
