LAST UPDATED July 5, 2023
Credential stuffing has become one of the most common and significant threats facing organizations today and is a risk for virtually any application that has login functionality (which is to say most applications). Let’s take a closer look at what exactly credential stuffing is, how it can be a challenge to control, and what sorts of things organizations can do to defend themselves today.
To get a detailed look at the credential stuffing attacks we see, check out the new research report from ThreatX Labs, Anatomy of a Targeted Credential Stuffing Attack.
What Is Credential Stuffing?
In a credential stuffing attack, attackers attempt to reuse credentials that were compromised in a previous breach in order to log in to another website or application. For example, take the recent PayPal data breach, which impacted 35,000 accounts.
Knowing that many end users will often reuse the same password on multiple sites, attackers often take breached credentials and try them on other high-value applications, such as a bank or online shopping account. In the PayPal attack, the company has yet to detected any unauthorized transactions, so the attackers may have carried out the attack simply to figure out which log-ins are re-used across multiple accounts so they can then sell those lucrative credentials.
Since data breaches are a relatively common occurrence, attackers have an almost never-ending trove of credentials that they can try against a virtually endless supply of targets.
In fact, a recent study has found that there are approximately 15 billion stolen logins stemming from around 100,000 breaches. This leads to somewhat of a cybersecurity feedback loop in which one breach can fuel downstream impacts to other apps and accounts.
The Value of Compromised Accounts
Credential stuffing plays a key role in the underground hacker economy. Naturally, an attacker could seek to directly profit from a compromised account. However, more often than not, access to the account is resold to other actors on the dark web and underground forums, as is suspected in the PayPal case.
This is an example of the ongoing specialization seen in criminal ecosystems in which certain actors will specialize in gaining access, while others will specialize in using the access to commit fraud or other activities.
These attacks are so common that compromised accounts have well-established commodity prices based on the value of the account. For example, financial and payment services accounts such as banking accounts, PayPal, or Western Union accounts can fetch between $30 and $120 depending on the amount of money in the account.
A wide variety of retail accounts are also prized targets with compromised Amazon accounts going for an average of $30. Social media user accounts are likewise common targets. These accounts can be used in astroturfing campaigns or can be used to spearphish and spread malware to users in a victim’s social network. For example, Facebook accounts are typically sold for $65, Instagram accounts for $45, and Gmail accounts for $80.
Find out how ThreatX helped a financial services organization defend against persistent credential stuffing attacks.
What causes Credential Stuffing Attacks?
Credential stuffing can be caused by a variety of different reasons.
1. Data Breaches:
User credentials are often targeted by cybercriminals during massive attacks on sensitive databases, who can use them for credential stuffing attacks.
These attacks occur when attackers infiltrate a company’s network and access sensitive user data, including usernames, passwords, and personal information. Data breaches can be caused by weak security practices, insider threats, or large scaled attacks.
2. Weak and reused passwords:
Users often choose weak or easily guessable passwords for their accounts. They may also reuse the same password across different websites and applications. This increases the risk of credential stuffing attacks, which occur when compromised login information from one data breach is used to access multiple user accounts on different platforms.
3. Phishing attacks:
Phishing is defined as an attack where attackers impersonate trusted entities like banks or social media platforms to get users to reveal their login credentials. These credentials are then used for credential stuffing attacks. Phishing attacks can come in the form of emails, phone calls, text messages, or social media messages.
4. Credential leaks:
Sometimes, users or employees accidentally leak credentials by sharing them with others or storing them insecurely (e.g., in plaintext files or on sticky notes). These leaked credentials can be discovered and used by cybercriminals for credential stuffing attacks. Additionally, online forums or dark web marketplaces may host databases of leaked or hacked credentials, making them easily accessible to attackers.
5. Automated tools and botnets:
Attackers often use automated tools and botnets to carry out large-scale credential stuffing attacks. These tools allow attackers to test millions of username and password combinations in a short period of time, increasing the likelihood of successfully accessing user accounts. Botnets are networks of compromised devices that can be controlled by an attacker to distribute and amplify their attacks.
How to Detect Credential Stuffing Attacks?
Generally, standard credential stuffing attacks can be detected using the following key techniques
1. Unusual Login Patterns:
Monitoring and analyzing user login patterns, identifying irregularities, detecting failed login attempts, recognizing multiple geolocation inconsistencies, utilizing machine learning algorithms, detecting rapid changes in IP addresses, implementing time-based restrictions, identifying bot-like behavior, flagging atypical user agents, and verifying login sources.
2. Rate Limiting:
Throttling login attempts, implementing CAPTCHA, using progressive delays, setting maximum request thresholds, monitoring for spikes in failed logins, enforcing account lockouts, deploying real-time monitoring systems, adopting adaptive rate limiting, customizing rate limits per user, and establishing time-based rate limits.
3. Multi-Factor Authentication (MFA):
Requiring additional verification methods, using One-Time Passwords (OTPs), employing biometric authentication, leveraging mobile device-based authentication, utilizing hardware tokens, implementing SMS-based authentication, offering software-based authenticators, integrating push notifications, leveraging email-based verification, and adopting time-sensitive tokens.
4. Device Fingerprinting:
Collecting device-specific information, analyzing browser configurations, monitoring installed plugins, identifying unique hardware characteristics, tracking device usage patterns, creating device profiles, detecting anomalies in device attributes, leveraging machine learning techniques, cross-referencing known device fingerprints, and establishing device reputation scores.
5. Web Application Firewalls (WAFs) & Security Solutions:
Deploying advanced WAFs, implementing intrusion detection systems, utilizing behavior-based security solutions, monitoring server logs for suspicious activity, creating custom security rules, leveraging AI-driven security tools, blocking known malicious IPs, employing content delivery networks (CDNs) with security features, implementing Distributed Denial of Service (DDoS) protection, and using threat intelligence feeds.
Credential Stuffing Detection Challenges
Credential stuffing techniques are able to sidestep traditional WAF signatures and rate-based rules for several reasons. Most notably, the techniques do not rely on an exploit or other overt malicious action, and instead, use/abuse the exposed functionality of an application in unexpected ways.
In this case, the attacker, usually in the form of a bot, is using the application’s login functionality in much the same way that a legitimate user does.
Additionally, since attackers have many username/password combinations to cycle through, the work is typically done by a large, distributed botnet or other forms of malicious automation. This not only speeds up the work, but it allows the attacker to distribute the attack over a large number of IP addresses so that it isn’t obvious that the attack traffic is coming from a specific set of IPs.
And unlike a brute force attack, credential stuffing attacks don’t typically try to iterate through multiple passwords for a given account. They simply try the stolen name/password pair, and if that doesn’t work, they move on to the next. As a result, rules that lock out an account after a certain number of failures will never trigger.
This all results in a situation where the attackers can blend in with valid users. On aggregate, it may be obvious that an application is under attack because it is inundated with login traffic. But for each login attempt, security teams often have no way to know which attempt is malicious and which is a real user.
Credential Stuffing vs Password Spraying
Although credential stuffing and password spraying share a common goal – unauthorized access to user accounts – they employ distinct methodologies. By understanding the differences between these two attack vectors, businesses can better protect their sensitive data and bolster their security defenses.
| Comparison | Credential Stuffing | Password Spraying |
| Methodology | uses large sets of stolen credentials to target multiple platforms | targets multiple users with a few commonly-used passwords |
| Automation | involves automated tools or bots to rapidly input credentials | is often a more manual, targeted approach |
| Detection | can generate numerous failed login attempts per user, hence, easier to detect | results in fewer failed attempts per user, making it harder to detect |
| Focus | relies on exploiting the common practice of password reuse across multiple accounts | exploits weak or default passwords such as ‘Alpha123’ |
| Prevention | employ unique, complex passwords with multifactor authentication and deploy advanced bot mitigation | employ strong password policies, monitoring anomalies in login attempts and better password hygiene |
Impacts of Credential Stuffing
Credential stuffing leads to a wide range of problems. Most obviously, a successful credential stuffing attack paves the way for an account takeover or ATO.
However, suffice it to say, attackers can abuse a compromised account in a variety of ways to commit fraud and pursue other malicious goals. Financial accounts can be used to steal funds, retail accounts to illegally buy items, and social media accounts can sway opinions or spread malware.
However, the influx of traffic from a credential stuffing attack can also quickly overwhelm an application’s resources, leading to a denial of service situation. One industry analysis estimates that, on average, 16.5% of traffic on a login page is tied to credential stuffing. However, this can be a drop in the bucket when a specific group sets its sights on a particular application or industry.
For example, in a recent series of credential stuffing attacks targeting credit unions, we were able to detect that 90% of traffic was malicious, and automatically block that traffic from ever reaching the target customers’ servers.
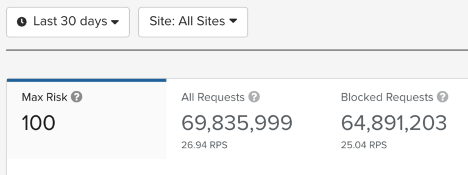
How ThreatX Protects Against Credential Stuffing
As seen in the example above, ThreatX has considerable real-world experience in mitigating bot-based attacks, including credential stuffing. The platform is able to do this by bringing together a variety of detection and analysis techniques to reliably separate the valid users from the malicious bots. While the details are naturally always changing as we adapt to stay ahead of attackers, we have highlighted some of the most important traits below:
- Active Interrogation of Visitors: ThreatX actively challenges visitors in ways that are completely transparent to valid users but can cause a bot to reveal its identity. This could be observing how the entity responds to automated challenges such as how the entity handles javascript or other types of code.
- Advanced Fingerprinting: ThreatX leverages some of the most advanced fingerprinting techniques in the industry in order to reliably identify and track malicious entities and infrastructure over time. This allows the platform to recognize attackers even as they change IP addresses, user agents, or other identifying characteristics.
- Automated Deception Techniques: The platform can introduce deceptive techniques such as fake fields that are readable to bots but invisible to users. Any interaction with these fields or functions can reveal that the visitor is a bot and not a human.
- Attacker and Application Behavior Analysis: In addition to tracking complex behaviors over time, ThreatX can identify atypical behavior at the user or application level. For example, if a visitor is able to fill a login form with abnormal speed or if applications seem to be getting overloaded with login traffic.
- Global Correlation and Tracking: By fingerprinting attacking entities, ThreatX is able to track their behavior across the Internet and across organizations. This allows organizations to benefit from intelligence gathered in previous attacks and preemptively block threats before the attack even gets started.
These techniques represent just a few of the techniques and countermeasures that ThreatX uses every day against credential stuffing attacks.
Get a detailed look at trends in credential stuffing, how we identify these attacks, plus identification tips and best practices, in new research from ThreatX Labs, Trends in Credential Stuffing and How to Identify It.
