Attacker-Centric Behavioral Analytics
Stay ahead of an ever-changing threat landscape and defend against attackers intent on exploiting traditionally vulnerable APIs and applications.
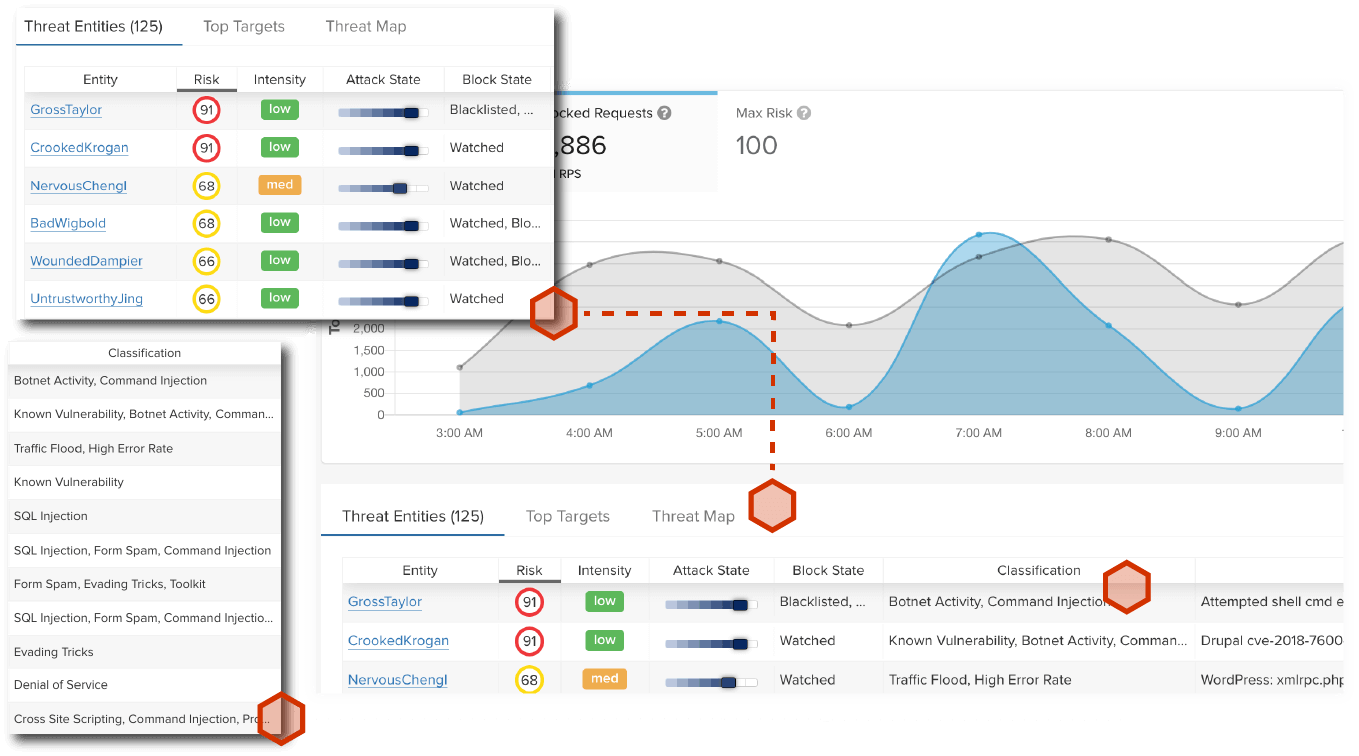
Protection that evolves with attacks
APIs and applications are often the holy grail for attackers. These adversaries see great value in these assets and exert significant time and creativity to evade rules-based detection techniques. ThreatX goes far beyond the basics of rules by inspecting the specific behaviors of an adversary over time. Through this inspection, ThreatX’s Attacker-Centric Behavioral Analytics (ACBA) enable security teams to stay ahead of an ever-changing threat landscape and defend against attackers intent on exploiting traditionally vulnerable applications and APIs.
How We Help
Quickly Identify, Monitor, and Block the Riskiest Threats in APIs and Applications
ThreatX identifies and correlates attackers’ behavior across multiple attack vectors to more precisely identify threats than is possible via a signature-based approach
Relying on signatures to identify threats used to work – but today, such approaches fall short and assume attackers are not as capable and creative as they are. By tracking and analyzing the behavior of attackers over time, ThreatX gains a much more complete and precise view of risk – both immediately and borne through low and slow attacks over time. This level of behavioral insight gives you the most complete defense against API and application attackers.
Learn more about the shortcomings of signature-based approaches to protection
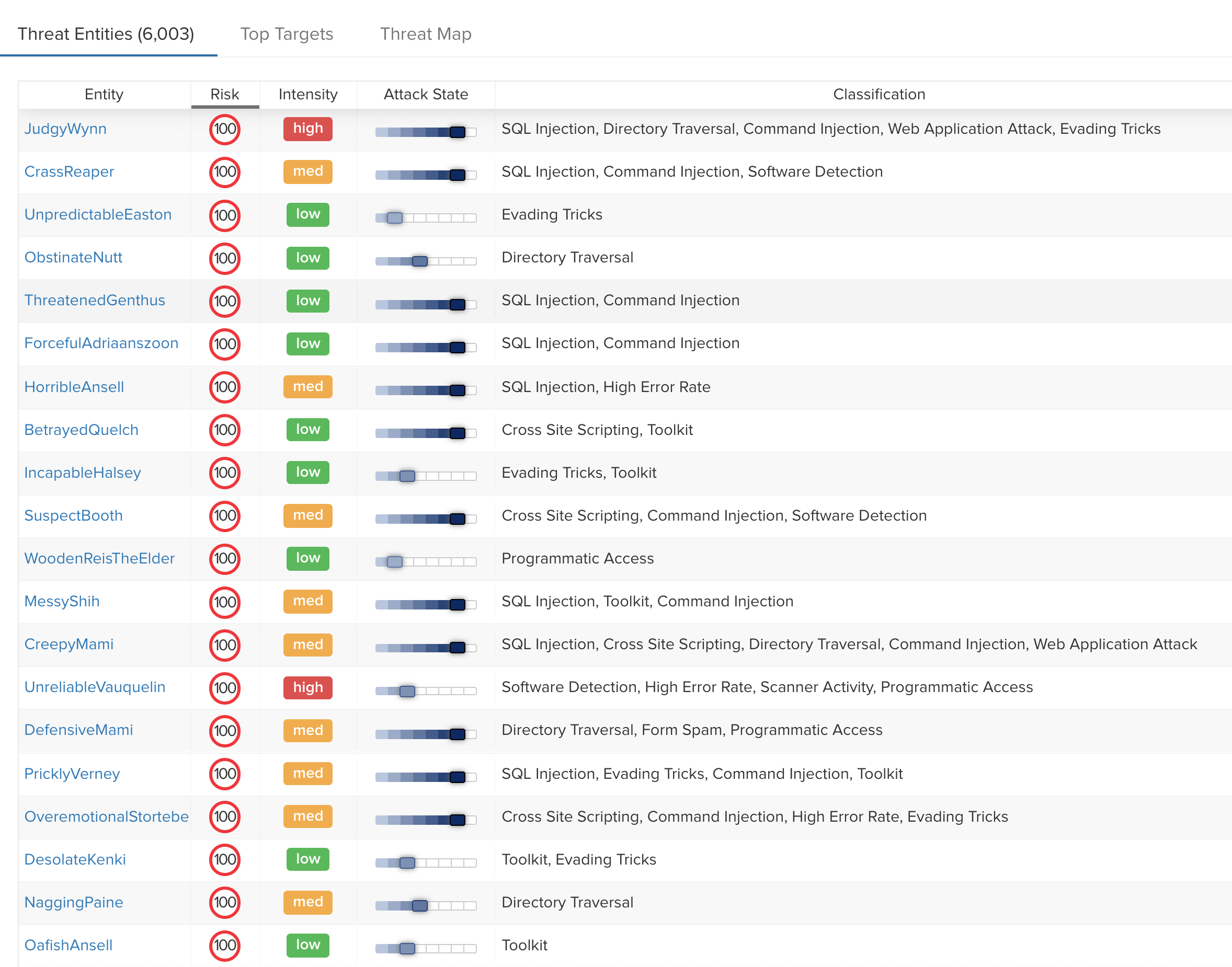
Say Goodbye to Endless Custom Rules and Maintenance
ThreatX automatically responds to changing attack patterns over time, as attacks morph, ebb and flow, adjusting to the motions of security defenses
The methods, modes, and cadence of attacks are far from consistent. Adversaries probe APIs and applications for vulnerabilities – and may retreat before relaunching an attack. Attackers deploy bots and DDoS attacks, as well as other sophisticated techniques, that make it challenging – if not impossible – to rely on signatures as a means of protection.
Through ThreatX’s ACBA, customers can identify tactics and procedures being deployed and escalation of the kill chain over time, determine whether an attempt is legitimate – or an attack, and secure their APIs and applications. We analyze IP reputation, TOR exit node status, geo IP, user agent, TLS fingerprint, and a number of behavioral attributes to identify entities and codify the risk associated with their behavior.
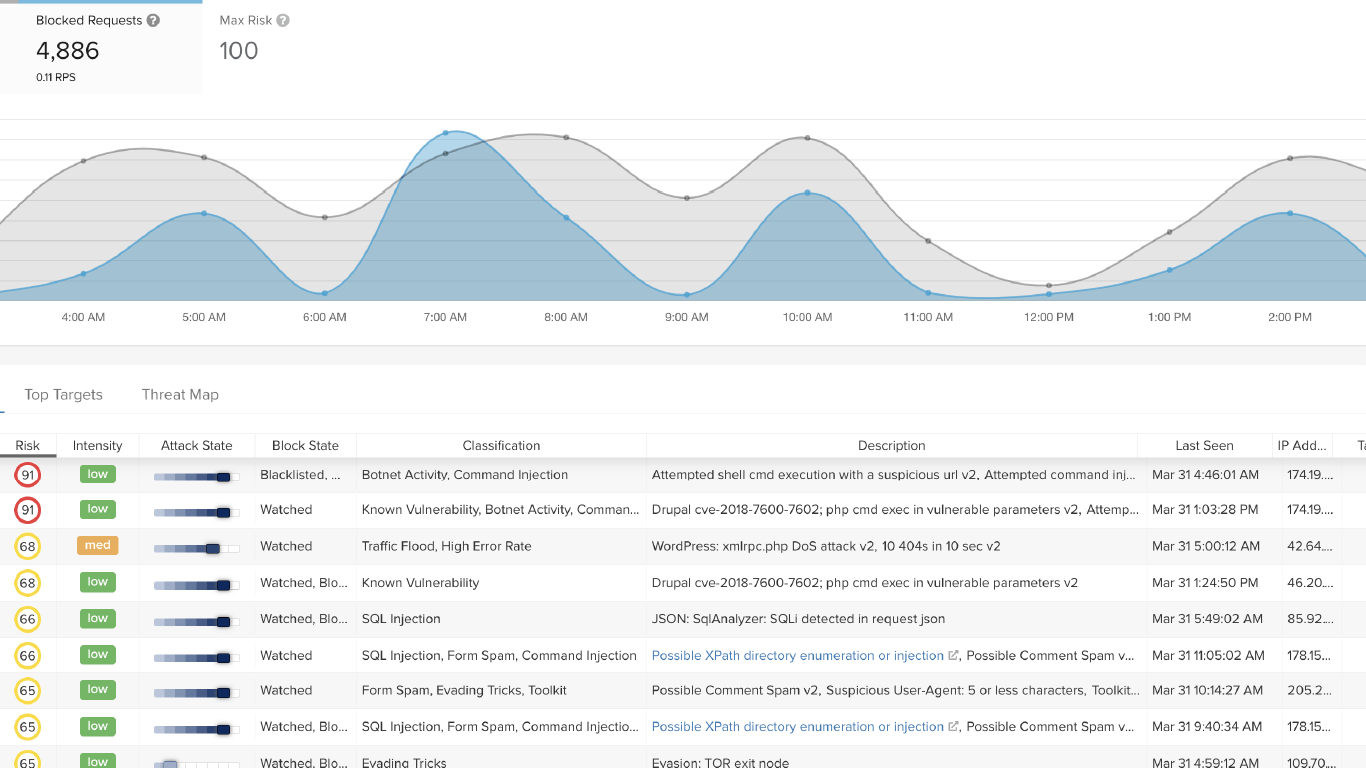
High Confidence Automated Blocking
Block suspicious entities from accessing APIs or applications when behaviors have surpassed an acceptable threshold of risk
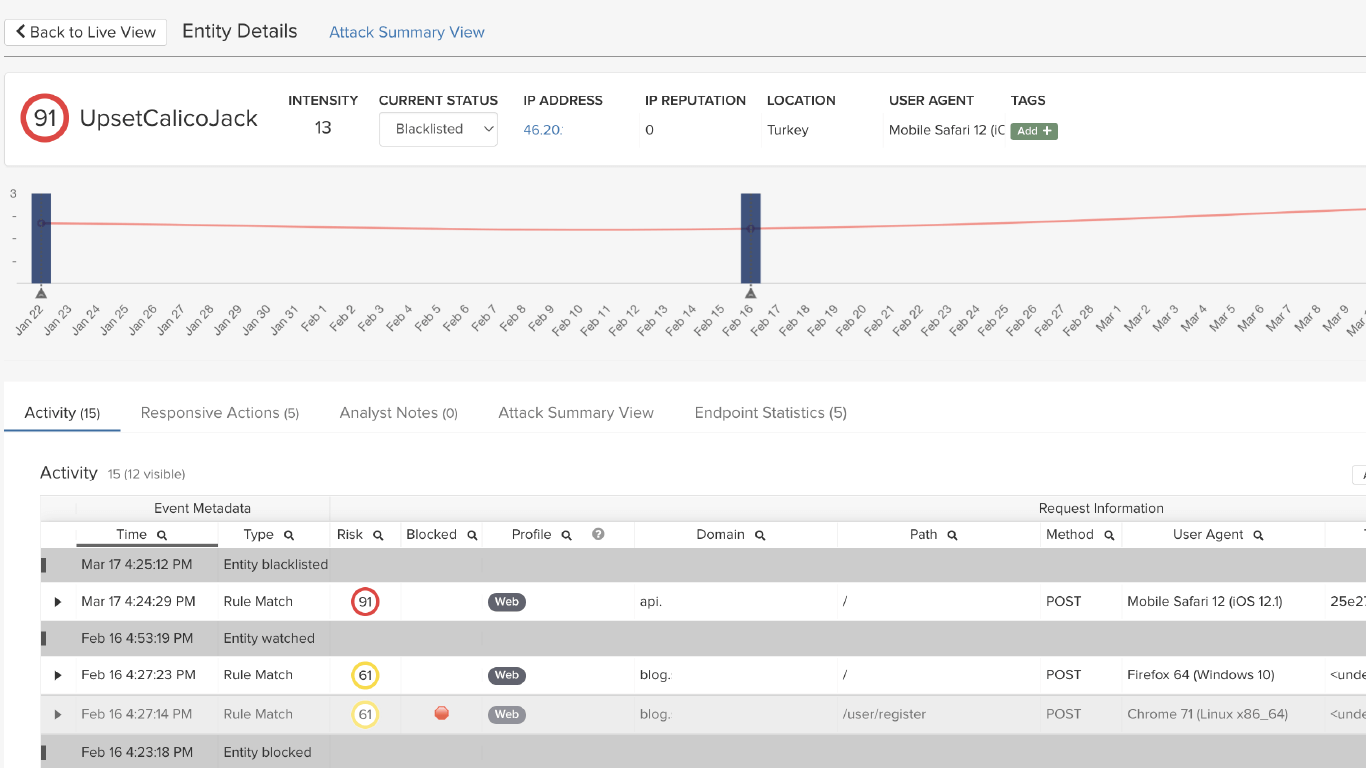
Attacker-Centric Behavioral Analytics, coupled with our single risk engine, blocks a suspicious entity from accessing an API or application when behaviors have surpassed an acceptable threshold of risk. Because the IP address of an entity currently exhibiting suspicious or malicious behavior may later be reassigned to a legitimate user, each entity is allowed three opportunities to exhibit questionable behavior before they’re permanently blocked.
-
ThreatX’s blocking modes are designed to block malicious requests and deter suspicious entities from attacking your sites, while allowing benign traffic and real users through.
-
ThreatX’s ACBA engine identifies and blocks persistently malicious entities.
-
ThreatX analyzes IP reputation, TOR exit node status, geo IP, user agent, TLS fingerprint, and a number of behavioral attributes to identify entities and codify the risk associated with their behavior.
-
ThreatX analyzes behaviors from multiple vantage points – rather than requiring a single, significantly risky event or identifying a known signature – to block a suspicious entity.
Learn how our Single Risk Engine correlates entity behavior over time and across tactics

Key Benefits
Secure APIs and applications with Observability, Prevention, and Protection
Eliminate risks without compromising your time or peace of mind.

Easy-to-Use
Experience user-friendly security designed to focus on what matters most. Leverage simplified dashboards so you can effortlessly oversee your API and application’s security posture and risks.
Easy-to-Manage
Get your nights and weekends back with always-active security that ensures your APIs and applications stay safe. Our visionary technology provides continuous protection and prevention without the need for manual intervention. Enjoy peace of mind knowing that your APIs and applications are secure even when you’re off the clock.
Eliminate Risks
ThreatX solutions are always monitoring, assessing, and identifying risks to APIs and applications continuously based on behavior. Our technology learns to recognize threats and vulnerabilities specific to your system, and proactively stops them based on risk level. This ensures your business remains operational and efficient, without interruptions.