Stop Paying for and Managing Multiple Application and API Protection Products
Protect your all your APIs and web applications deployed across any mix of public and private clouds by automatically detecting and blocking only the riskiest traffic in real-time.
The right technology for any challenge
The modern threat landscape is sophisticated and continuously evolving, that’s why security must similarly be both broad and deep. ThreatX has brought together the industry’s most complete set of features into a unified approach that leverages every available perspective and technique for every event.
Learn more in a personalized demoPRODUCT FEATURES
Protection for All Your Apps and APIs
A comprehensive, integrated platform to protect against the wide breadth of security threats facing web apps and API endpoints
Web Application Firewall
ThreatX’s Next-Gen WAF (also known as WAAP) takes an attacker-centric approach to detect a wide variety of threats including traditional exploits, bots, API-specific risks, and DDoS attacks.
- OWASP Top 10 Threats
- Credential Stuffing
- Advanced Multi-Layered Attacks
- Bot Management
- DDoS Protection
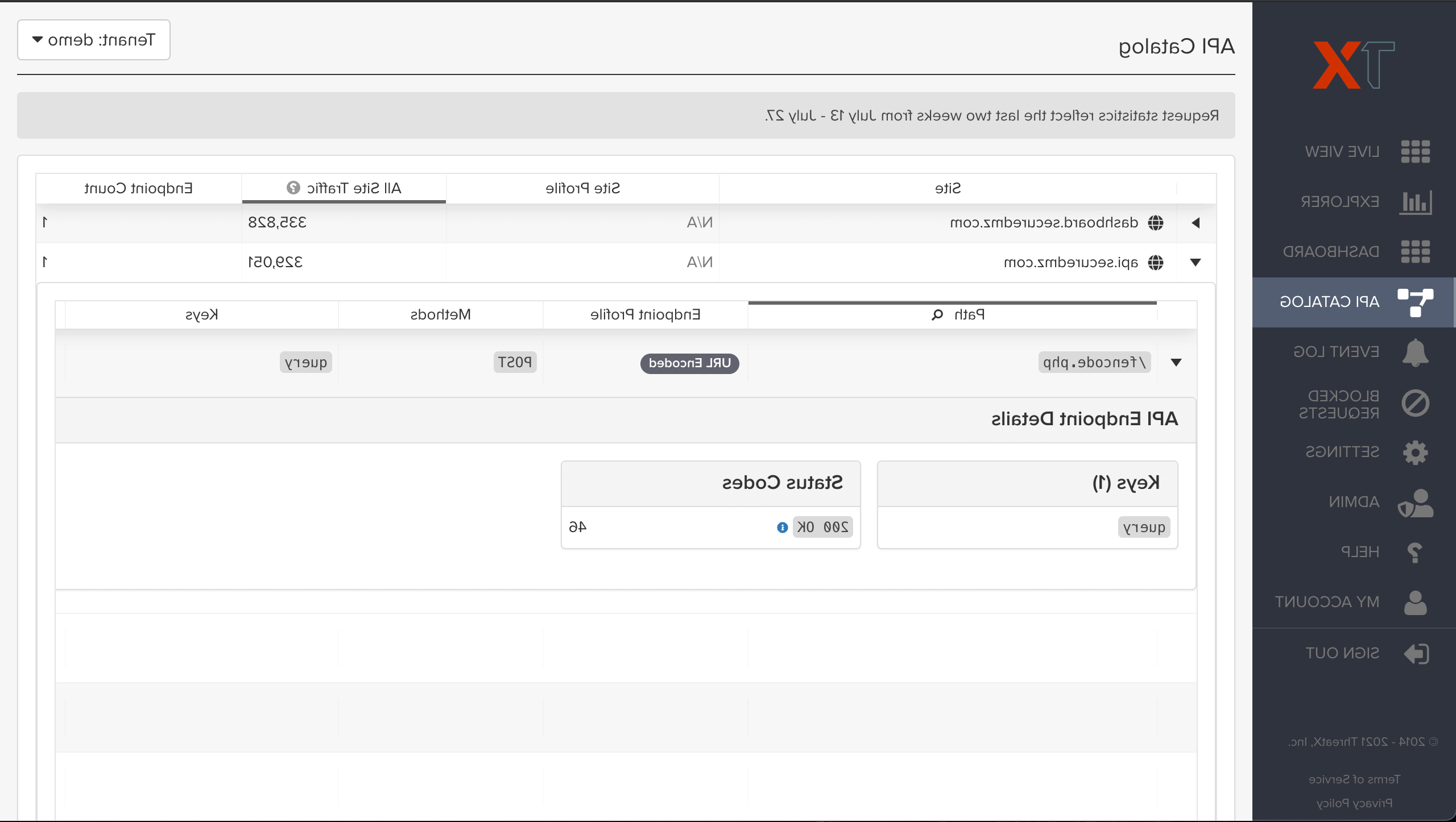
API Security
APIs are the building blocks of modern applications, yet the adoption of API-based architecture has expanded organization’s attack surface. For this reason, ThreatX not only protects API endpoints but also provides unparalleled visibility and intelligence about the threats these APIs face.
- API Profiling and Operational Health
- Automated Discovery
- Native JSON and WebSocket Support
- API Host Enumeration and Recon
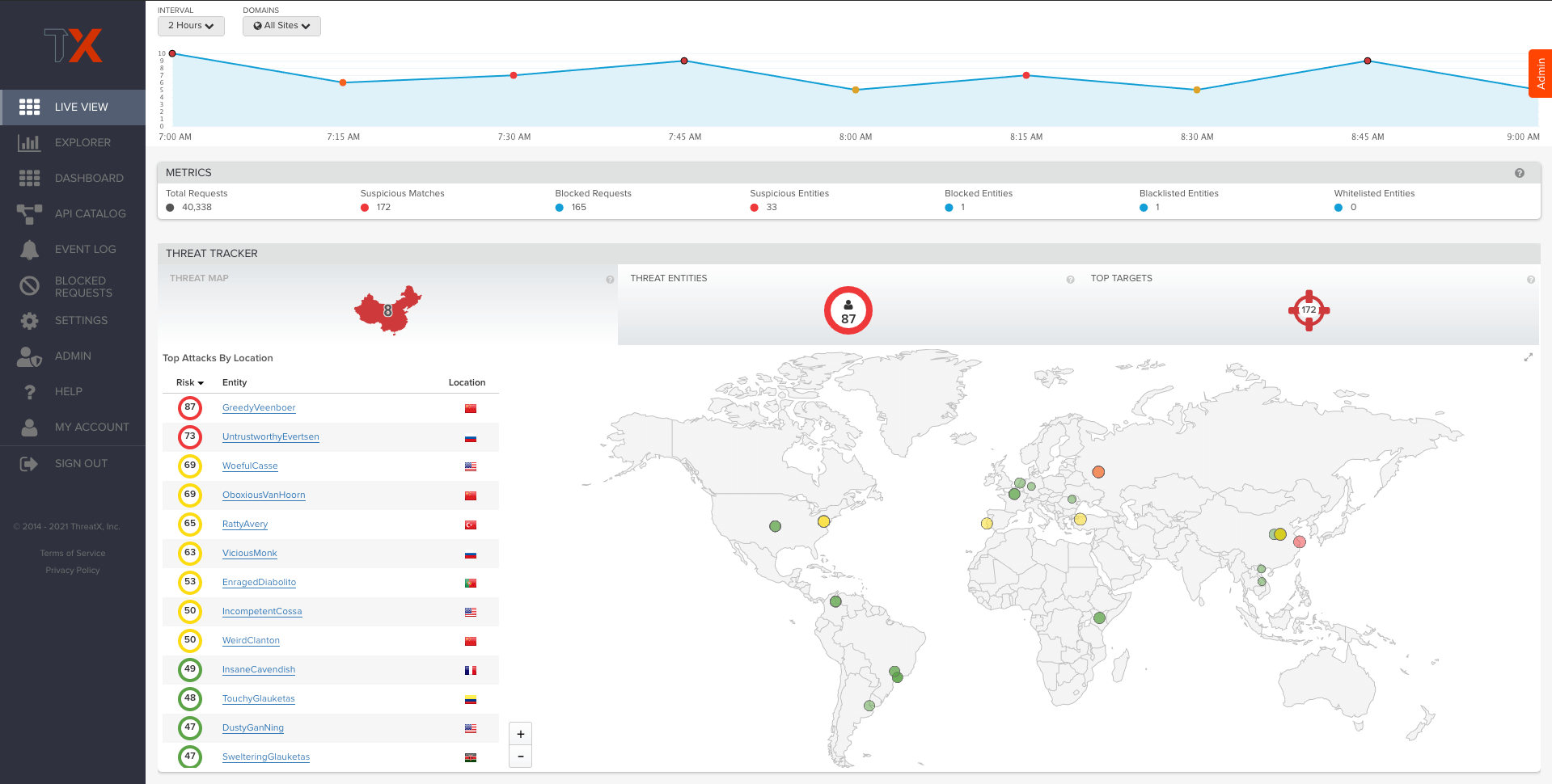
Entity and Behavior Analytics
ThreatX goes far beyond the signatures and anomaly detection used in other AppSec tools today. Our unique approach is able to identify and track malicious entities even as traits such as IP addresses and user agents change. This lets us track and compile and complete picture of an entity’s risk so that enforcement is both highly accurate and laser-focused on the threats that matter the most.
- Entity Fingerprinting
- Entity Tracking and Risk Attribution
- Entity Actions and Response
- Application Profiling
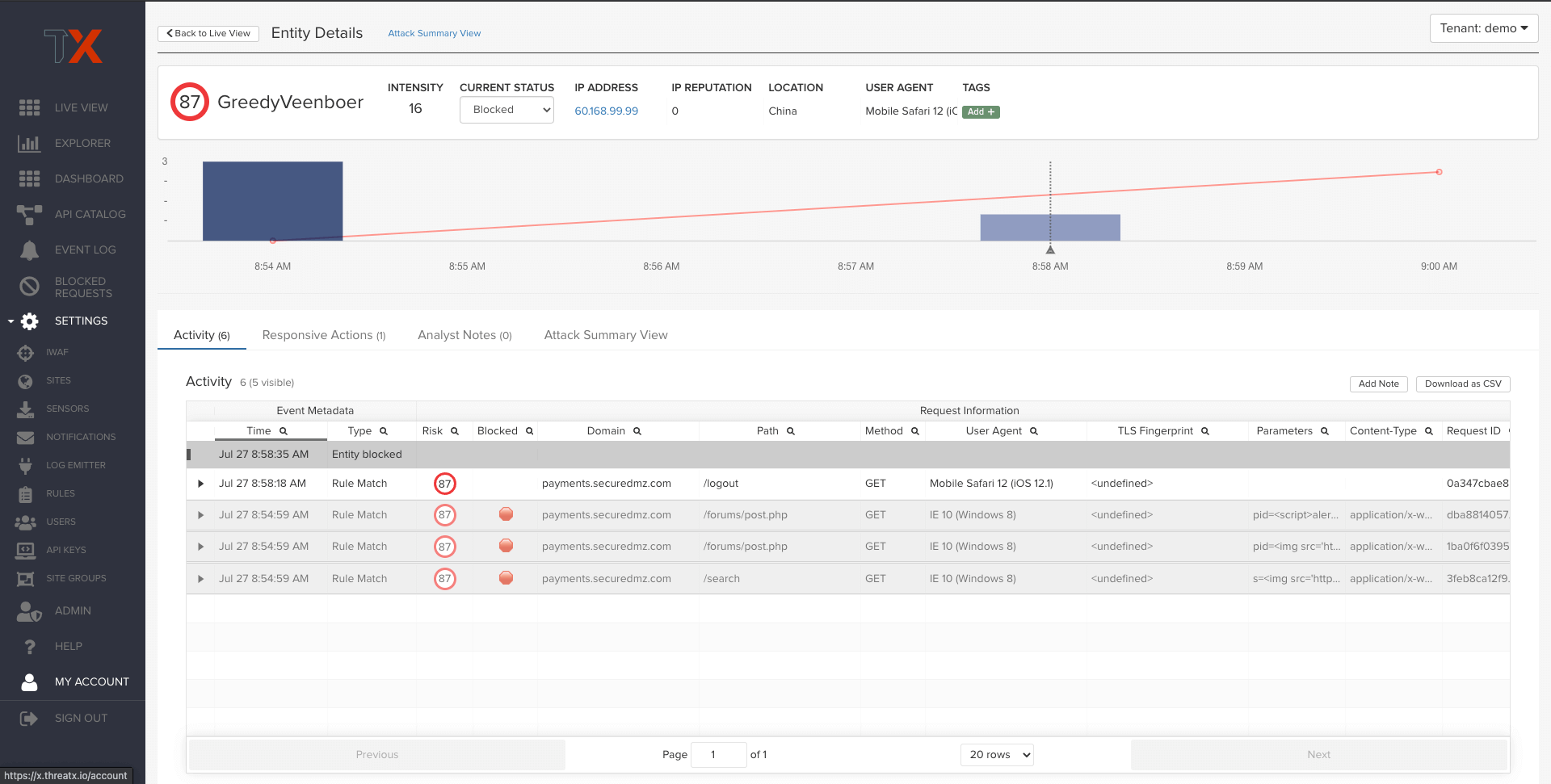
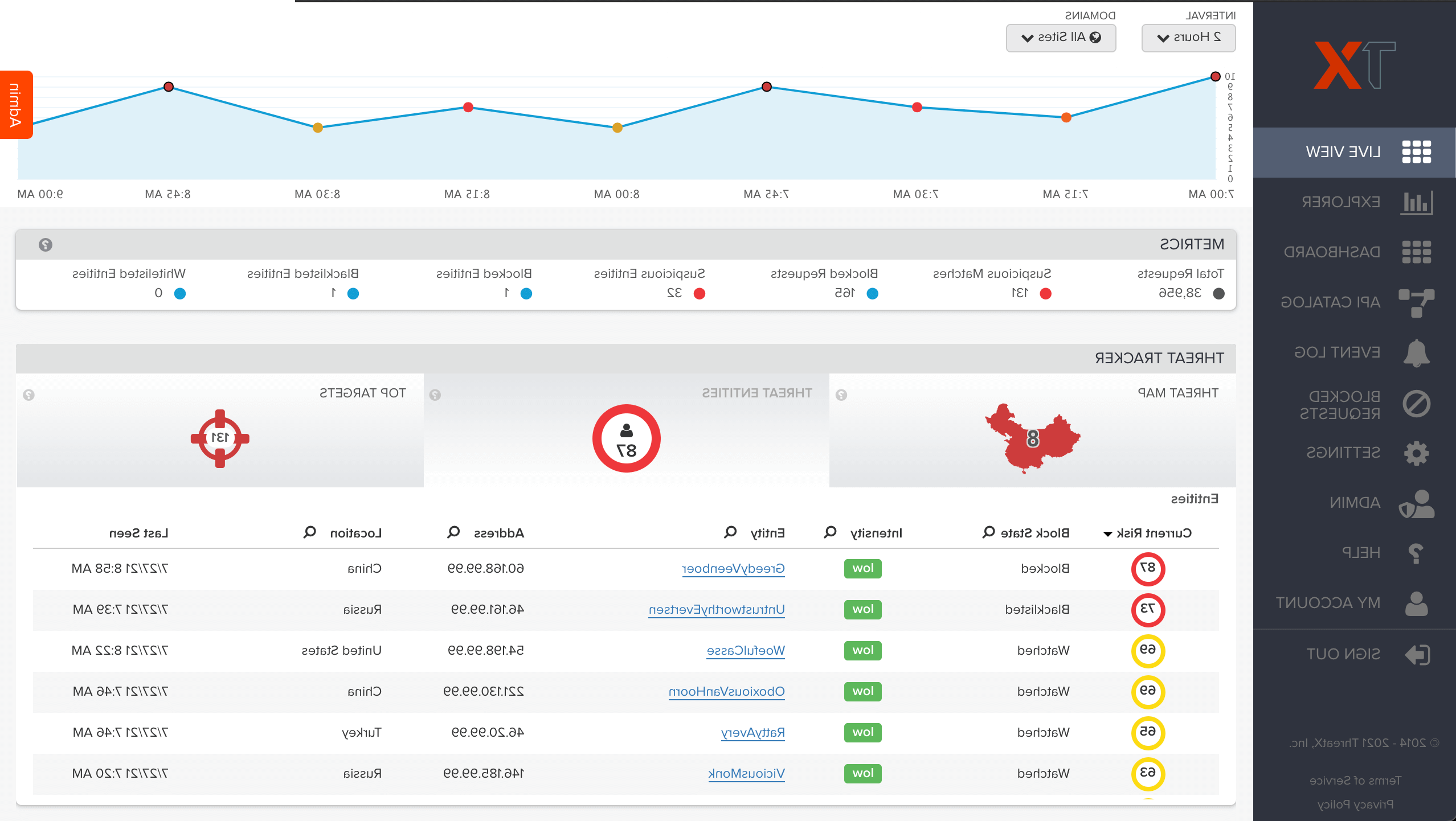
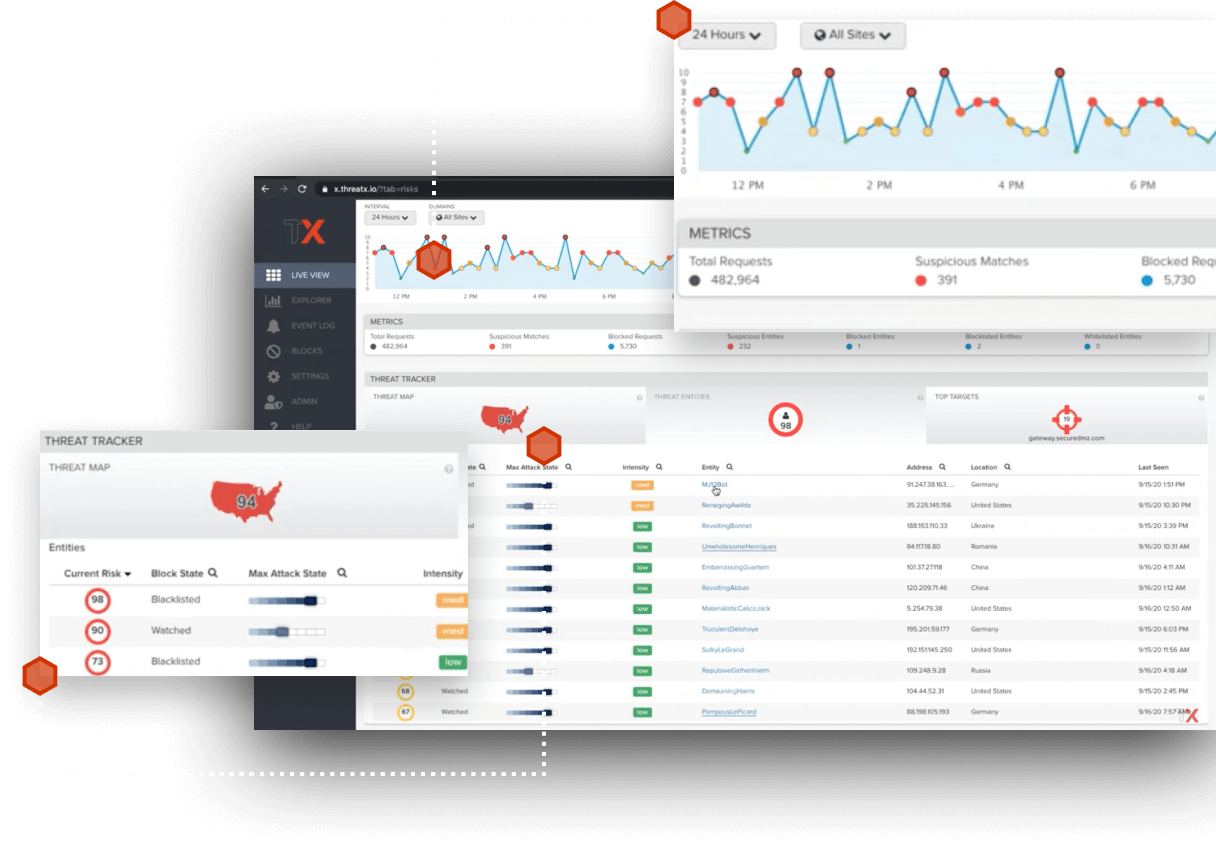
Attack Analytics
ThreatX analytics automatically correlates large amounts of data so that security teams have the real-time situational awareness needed to keep their applications safe. Teams can immediately see the riskiest entities, the assets under attack, and exactly how they are being attacked.
- Find and Take Action against High-Risk Entities
- Detailed Risk and Behavior Analysis
- Progressive Interrogation
- Automated Correlation