LAST UPDATED March 25, 2025
What Is a DDoS Attack?
DDoS stands for distributed denial of service attack. It is a brute force cyberattack where perpetrators target a server with multiple unique IP addresses or devices, aiming to overwhelm it’s computing resources to result in an outage. When a DDoS attack targets a server, its services become slowed or inaccessible for users.
Unlike other cyberattacks, DDoS attacks are, by default, designed to disrupt business operations rather than take over the system. DDoS attacks last anywhere from a few hours to several months. Generally speaking, DDoS attacks targeted at the network layer last 48 hours, while application layer attacks can last up to 70 days.
DDoS attacks are carried out for different reasons. Ideologists might attack a site or server to make a statement or express disapproval. DDoS attacks have also been used for financial gain. A blackhat competitor might overwhelm their competitor’s resources to channel customers back to their site during the period under which their competitor’s site is inundated with spam traffic.
The yearly number of DDoS attacks has been rising alarmingly. In fact, according to Cisco’s Annual Internet Report, DDoS attacks could reach an all-time high in 2023. Cisco predicts that DDoS attacks will reach 15.3 million globally.

DDoS attacks projection
The Covid-19 pandemic forced many entities and individuals to conduct business online, providing hackers with more targets for an attack and many potential bots they could utilize to push traffic to a website.
Below are some of the factors that have caused a rise in DDoS attacks in recent years:
- E-commerce
- Mobile payments
- Cloud computing
- Public Transportation
- Public services
- Big data and analytics
- Social media
- Machine learning
Also, many businesses now rely on IoT devices. However, these devices are the most susceptible to manipulation by DDoS attackers because they are usually unprotected.
Unfortunately, DDoS attacks can be targeted at any business, from small non-profit organizations to multi-million-dollar conglomerates. To demonstrate that no organization is safe from DDoS attacks, below are the five most famous DDoS attacks orchestrated against industry giants:
| Company | Year | Effects |
| June 1, 2022 | Google says it recently fended off the largest HTTPS DDoS attack in history. The attack used the Meris botnet and peaked at 46 million requests per second. | |
| Amazon Web Services | February 2020 | This attack lasted three days, targeting an unidentified customer using Connectionless Lightweight Directory Access Protocol reflection. |
| Krebs’ blog and OVH | September, 2020 | The cybersecurity blog by Brian Krebs was attacked using DDoS. The attack peaked at 620 Gbps – almost triple the largest of the 269 attacks directed at his site since 2012. It was the first Mirai botnet big attack. Layer, the same botnet targeted O.V.H., one of the largest European hosting providers, driving over 145000 bots. |
| Dyn | October 21, 2016 | Another Mirai botnet attack targeted at the domain name service provider Dyn was perpetrated. This was just months after the Mirai software source coder caused multiple replications of the Mirai DDoS platforms. This attack rendered many high-profile websites inaccessible. Some affected websites were Reddit, Paypal, Netflix, Twitter, Airbnb, and HBO. |
| Github | February 28th, 2018 | This DDoS attack clocked at 1.35Tbps and lasted for about 20 minutes. The attackers used a Memcached DDoS attack technique. |
Effects of DDoS Attacks on Businesses
While such attacks do not aim at taking over a server, they can severely ruin a brand’s reputation. Customers are satisfied when they know that their information is safe online. When a DDoS attack is orchestrated on their favorite platform, they can’t help but consider the possibility of their data being exposed. Also, part of the customer’s trust in a brand comes from knowing they can access the services at will. That trust might dwindle when they can’t do that during a DDoS attack.
In addition to a tainted reputation, businesses lose a lot of revenue during a DDoS attack. Going by their 2020 revenue report, AWS generates about $4,097,222 per hour. In the event of a DDoS, they could potentially lose a similar amount every hour.
How Does a DDoS Attack Work?
DDoS attacks are a subcategory of a broader form of cyberattacks known as DoS, denial of service attacks. While a DoS attack is a system-on-system attack, a DDoS attack involves several computers or resources focused on a single server.
What is a DDoS botnet?
The primary way DDoS attacks are carried out is through botnets.
A botnet is a group of connected computers or devices under the control of a malicious party. The word botnet comes from shipping two words – robot and network. A DDoS attacker hacks into computers or other devices and installs malicious code, otherwise known as malware bots.
There are several ways through which attackers gain access to bots. It could be through a Trojan Horse Virus, exploitation of a website’s vulnerabilities, or cracking weak authentication. Each of these methods allows them remote access to the computers in question. Once remote access is acquired, the attacker installs botnet malware that allows remote control of the device. Additionally, the malware connects the infected computers to form a botnet.
The attacker then instructs the botnet to flood the targeted site or server with more connections than the target can handle, causing a denial of service.
Botnets are created for several reasons, ranging from activism to state-sponsored disruptions.
DDoS attacks have increased in recent times because attackers can hire DDoS attack tools inexpensively. Creating a botnet has a low barrier of entry, making it an attractive business for low-level developers, especially in countries with lenient cyberactivity regulations.
How are DDoS botnets controlled?
Botnets designs, and by inference, their control structures, vary. Botnet models can be divided into three categories as described below:
- Client-server botnet model. Each device connects to a central server to access information, mimicking a traditional workstation structure. Client-server models are the most common type of botnet. Each bot in the network connects to a central command & control server. The C.N.C. server receives and then serves commands to the bots in the network. Sometimes, botnets can be connected to several small servers to form a multi-server network.
- Peer-to-peer (P2P) botnet model. Since a client-server botnet uses a centralized server, you can remove it by disrupting the centralized server. To circumvent this vulnerability, attackers have designed a botnet model that uses components of decentralized peer-to-peer file sharing. With the P2P model, every bot functions as a server and client (bot), thus circumventing the single-point-of-failure vulnerability common with client-server models. Additionally, since each bot is only connected to adjacent devices, it is harder to track or disrupt the botnet when in action.
- Compliant/controlled model. This model is similar to the client-server model. The only difference is that malware is installed on a compromised server, which then connects to the CnC server, where the botmaster feeds it with tasks to execute.
How to identify a DDoS attack
DDoS attacks are difficult to identify because the symptoms are usually similar to those experienced every day by Internet users. Unless you inspect closely, you might not notice that it’s a DDoS attack. Also, since you’re not constantly scrolling through your website unless you have threshold alerts, DDoS attacks might go undetected until a customer points it out.
Despite that, DDoS attacks can damage your online business’s reputation and revenue, so it’s essential to understand the telltales of a DDoS attack. The following are some of the ways you may identify a DDoS attack:
- Too many requests from a specific IP address
- A massive spike in website traffic
- Files load slowly or don’t load at all
- Odd traffic patterns. For example, similar requests after a consistent interval or huge spikes during odd times of the day
- Large amounts of traffic coming from similar devices, geolocation, or web browser version
- Website becomes unavailable
What are some of the common types of DDoS attacks?
While all DDoS attacks aim at inundating the target, they can be executed in multiple ways depending on the motive and attack technique. DDoS attacks can be classified into three broad categories:
- Volume-based attacks
- Protocol attacks
- Application layer attacks
Below are some of the common types of DDoS attacks:
Memcached DDoS attacks
Instead of storing data in disks or S.S.D.s, Memcached systems store data in memory, meaning they are faster and can be used for high-performance systems because they do not need to seek data from disks upon request.
A Memcached DDoS attack works similar to other amplification DDoS attacks.
How amplification attacks work
Amplification attacks involve three parties – an attacker (botnet), a reflector, and a target. The attacker spoofs the target victim’s IP address and send requests to the reflector. The reflector is essentially a compromised server that’s been fed with a large amount of data. While attempting to be helpful to the attacker’s requests, it responds to the target’s server instead. The response contains a large amount of data – more than the data in the request, thus causing an amplification.
Here is a better analogy to help you understand how amplification attacks work: A kid calls a restaurant and orders everything on their menu. The kid then requests the restaurant to call them back and describe the details of their order. However, instead of the kid leaving the restaurant with his number, he provides them with the target’s number. In obedience to the kid’s request, the restaurant calls the target victim’s number with a lot of information they didn’t request. In this scenario, the kid signifies one bot. This process is repeated thousands or millions of times depending on the botnet’s size, inundating the target victim with the information they didn’t request.
Going back to Memcached attacks, the attacker attacks in four steps:
- The attacker starts by feeding a vulnerable Memcached server with a large amount of data
- The attacker then sends a request to said vulnerable server masquerading as the target victim’s IP address
- The vulnerable Memcached server receives that request and sends a significant response to the target
- The targeted network receives a large number of information from thousands of requests from each bot and is unable to handle it, thus resulting in a denial of service for legitimate users

memcached DDoS attack
Memcached DDoS attacks work because Memcached systems, by default, operate with a User Datagram Protocol (U.D.P.) that doesn’t require both parties to authorize the communication. A study conducted by F5 labs found that UDP-based attacks accounted for over 83% of all DDoS attacks between January 2020 through March 2021.

NTP amplification attack
Another reflection-based volumetric attack, N.T.P. amplification attacks utilize the Network Time Protocol instead of a Memcached server. The N.T.P. is a networking protocol used for clock synchronization between computer systems.
Attackers exploit the ‘get monlist’ command, which is supposed to return the last 600 source IP addresses of requests made to the N.T.P. server.
One ‘get monlist’ request gets magnified 206 times, meaning that each bot in the botnet initiates a request that is amplified 206 times. Therefore, if an attacker sent 1 Gb worth of requests, they could deliver a 206 Gb attack on the target victim’s server.
DNS amplification attack
In a DNS amplification attack, an attacker sends a DNS name lookup request to an open DNS server with an IP address spoofed to the target victims. The DNS recursor receives the query and then passes the DNS record to the target instead of the attacker. To maximize the attack, attackers often ask questions of the type ‘ANY’ to ensure that a lot of information is sent to the target through a single request.
This process is replicated for each bot in the botnet, flooding the target victim with information and consequently slowing their systems down.
S.S.D.P. Attack
The Single Service Discovery Protocol is a networking protocol used to advertise and discover network services. It allows universal plug and play (UPnP) devices to broadcast their existence to computers within a network.
When the computers receive a notification from the UPnP, they send a discovery packet requesting the UPnP to send a complete description of its services, which often contains much more data than the computer’s discovery packet.
That last stage is what DDoS attackers exploit. They scan a network system, identify the UPnP devices connected, create a U.D.P. packet spoofed with the target’s IP address, then send the spoofed discovery packet using a botnet to each plug-and-play device in a network. The discovery packet requests as much data as possible from each device. Consequently, each device could return as much as 30 times the amount of data in the initial request. The target receives a large amount of unrequested information from all devices multiplied by the number of bots in the botnets, which could result in denial of service to regular users.
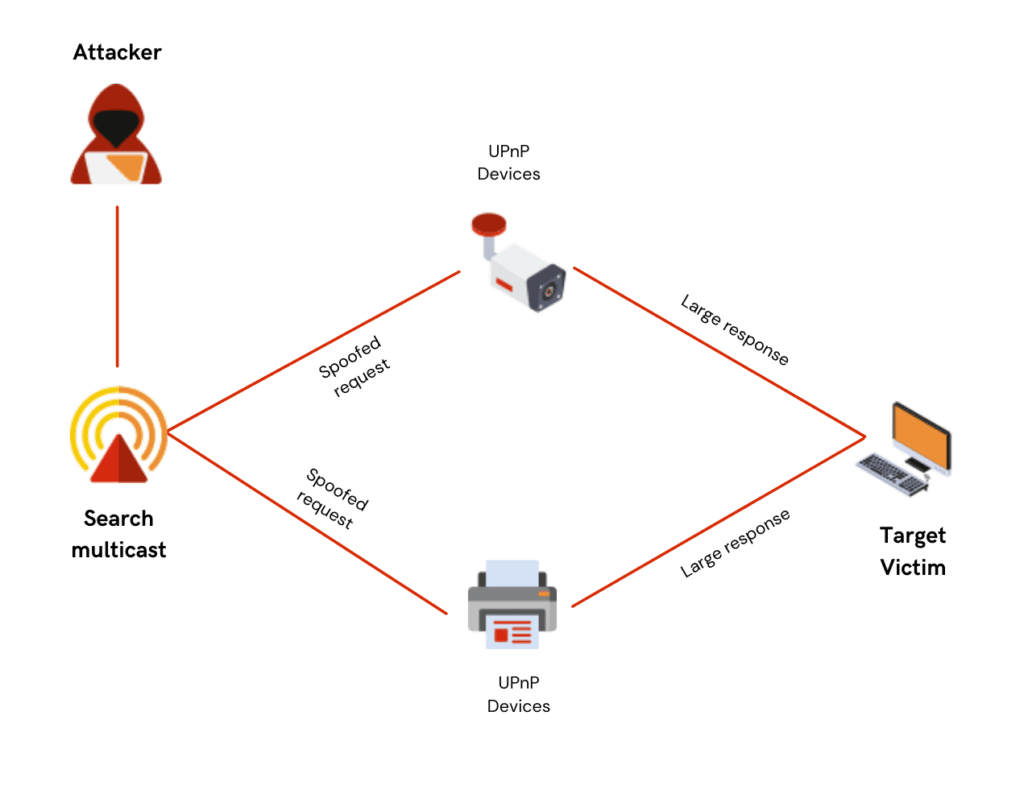
SSDP DDoS attack
Low & slow attack
This DDoS attack targets thread-based web servers. Thread-based web servers process each request on an individual thread instead of an individual process. Attackers exploit this by sending many slow requests that engage all of the server’s lines, thus preventing legitimate users from accessing the service.
The requests are designed to be slow enough to expend the server’s resources but fast enough not to time out.
Low & slow attacks are challenging to detect because requests resemble regular traffic, and unlike other brute-force attacks, they do not overwhelm the system instantaneously. They can go undetected for long periods.
Application layer attacks
Application layer attacks target the 7th layer of the Open Systems Interconnection stack. This layer is implemented by network applications to produce the data to be transferred and displayed over the network. Your web browser is an excellent example of an application layer.
This attack works by inundating a specific application with requests from a botnet, overwhelming the targeted server and consequently resulting in a denial of service to legitimate users.
An example of an application layer attack is a botnet requesting to log into accounts. The browser sends more authentication requests than the server can handle, thus significantly slowing down the website.
HTTPS flooding
The attacker sends thousands or millions of process-intensive requests to the target using a botnet, causing the server to freeze as it tries to respond to each request.
Smurf attack
In a smurf attack, the attacker first creates a network packet with a spoofed IP address. The packet contains an ICMP ping message that requests every device connected within the network to reply to the victim’s address. Consequently, the target victim receives ICMP echo replies from each device in the network, which could potentially overwhelm it.
Ping of death attack
This attack works by sending an oversized packet to the targeted system to destabilize, crash, or freeze it.
The Internet Protocol only allows packets of up to 65535 bytes. Attackers usually exploit this by sending fragmented packets to the target victim, which sum up to a number greater than the allowed limit. When received, the target device attempts to reassemble the fragments, but since the packets are more significant than the allowable size, it runs into memory overflow, resulting in a crash.
ping of death attack
What are the most common DDoS attack tools?
The constant tug-of-war between cyberattackers and defenders has resulted in the birth of many DDoS attack tools. While some tools are created specifically to launch DDoS attacks, some were made for legitimate stress testing purposes but have been leveraged to launch DDoS attacks by malicious parties.
Below are some of the typical DDoS attack tools:
Low Orbit Cannon
Low orbit cannon (L.O.I.C.) is one of those tools that network testers initially created to perform stress tests on networks. However, after being made open source, the low orbit cannon application has been used to launch DDoS attacks over the years.
It works by sending multiple requests to a targeted IP with TCP or U.D.P. requests and, by so doing, flooding the targeted IP
L.O.I.C. is a popular tool among DDoS attackers because it doesn’t require much technical knowledge. An attacker can download the L.O.I.C. application off of the Internet and use it to launch an attack within minutes.
L.O.I.C. has launched several high-profile attacks over the years, the most famous being Project Chanology and Project Payback.
High Orbit Cannon
Also known as H.O.I.C., the high orbit cannon is a successor of L.O.I.C. It improves L.O.I.C.’s capabilities and adds customizations such as proximity redirecting. One of the significant drawbacks of L.O.I.C. is that it doesn’t provide anonymity, and an attack can be traced back to the source.
It is used to launch application layer attacks by flooding the victim’s server with HTTP ‘G.E.T.’ and ‘POST’ requests. Another significant difference with L.O.I.C. is that it can accommodate up to 256 concurrent attacks, meaning that different players can join forces to launch simultaneous attacks on several targets.
It was developed by Anonymous, a hacktivist collective that used it to launch some of the most significant attacks in history, targeted at R.I.A.A. and the F.B.I. During the F.B.I. attack, there were over 27,000 computers simultaneously using H.O.I.C.
Slowloris
Slowloris is a DDoS attack tool that facilitates low and slow layer seven attacks. It works by keeping as many ports as possible open on a server by sending incomplete HTTP requests.
It periodically sends headers before the connection times out so that ports do not close.
Once all the ports are engaged, any additional request – including from legitimate users- will be denied service.
R.U.D.Y.
R-U-Dead-Yet? is another low and slow layer 7 DDoS attack tool that allows users to launch an attack from a simple point-and-click interface.
Like Slowloris, it works by tying up all available connections. The only difference is that instead of sending incomplete HTTP requests, R.U.D.Y. works by submitting form data at an absurdly slow pace.
When aimed at a target, it crawls the website looking for a form. Once found, it sends a header that informs the server that a large amount of data is about to be submitted and then goes ahead to offer small bits of information at slow intervals indefinitely.
Any website with form submissions is vulnerable to R.U.D.Y. Such attacks can go undetected for weeks as the Internet traffic resembles legitimate traffic from a user with a slow Internet connection.
IP spoofing
Data sent over the Internet is broken down into multiple packets that are reassembled at the end of the transmission. Each packet usually contains an IP header that bears information about the packet, such as the source and destination IP addresses.
IP spoofing involves creating IP packets with a false source IP address to masquerade as a trustworthy entity to avoid detection or gain entry into a system.
As alluded to earlier, IP spoofing is commonly used to facilitate amplification of DDoS attacks by sending a request and directing a bulkier response from the server to the target victim’s computer.
IP spoofing is a powerful DDoS attack tool with the potential to bring even the most robust sites down. For example, in 2018, Github’s website was down for nearly 20 minutes following one of the most significant DDoS attacks in history, which involved IP spoofing. The attack had an outstanding throughput of 1.3 Tbps, as seen in the image below.
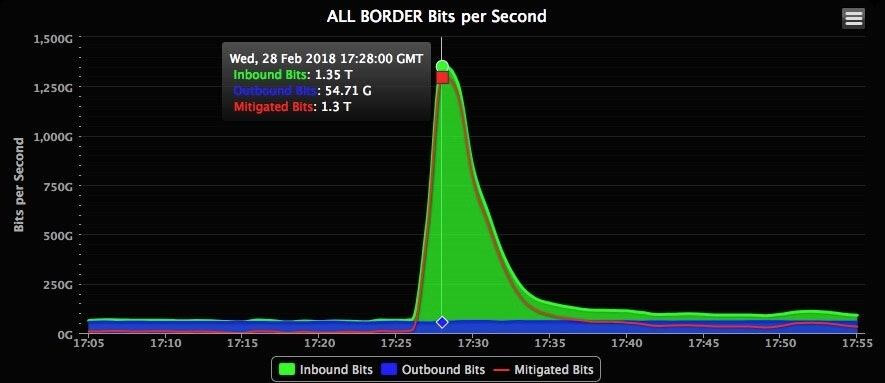
real time traffic from github’s ddos attack in 2018
Mirai Botnet
Mirai is an Internet of Things (IoT) botnet that came into the spotlight in 2016. This tool scours the Internet for unsecured smart devices running a specific version of Linux called A.R.C. The Mirai malware then tries to gain access to the smart device by finding the correct password, often the default one.
Upon successful entry, the device is then added to a botnet used to perpetrate DDoS attacks. Mirai is especially dangerous because it is self-propagating – it replicates itself by finding, attacking, and infecting other vulnerable devices in the same network.
At its peak in 2016, the Mirai botnet was used to perpetrate DDoS attacks on high-profile services such as Krebs on Security, O.V.H., Dyn, and Minecraft servers.
How to prevent DDoS attacks
DDoS attacks can ruin a company’s reputation, expose its users’ data, and result in massive financial losses. To avoid this from happening and react to a DDoS attack that’s already in progress, here are some ways to prevent DDoS attacks:
DDoS blackhole routing
Also known as blackholing, blackhole routing involves routing or dumping all traffic into a null route, otherwise called a black hole.
When executed without filtering criteria, blackhole routing can dump legitimate traffic along with the attacker’s traffic. While that might help the attacker achieve their goal – to cause a denial of service to users – it is necessary for specific situations. For example, suppose a DDoS attack is targeted on a small website as part of a more extensive network. In that case, it may be prudent to route all the traffic to a different IP address to protect the more significant infrastructure.
If not executed carefully, a black hole can result in serious problems. For example, the world witnessed the power of blackhole routing in 2008 when YouTube was down for hours due to an error made by Pakistan’s state-owned telecommunications company in an attempt to blackhole YouTube in the country.
Rate limiting
As the name suggests, this solution limits the rate at which users repeat an action within a specific timeframe.
While rate limiting doesn’t prevent DDoS attacks, it helps to mitigate the ones already in progress by limiting the strain on the server and, by so doing, avoiding denial of service to all users. It also helps to slow down the attack as you seek a solution.
Rate limiting works by monitoring the time between requests from each IP address. If the number of requests exceeds a set threshold, the server will not fulfill those requests through rate limiting.
WAF
A web application firewall (WAF) is a security application that protects a server by filtering malicious information from the application level. It acts as a buffer between the application and the server, monitoring and filtering HTTP requests to ensure that only legitimate HTTP requests reach the server.
A web application firewall operates through a set of rules called policies. This framework comes in handy during a DDoS attack as the rules can be modified to thwart an attack after detection.
AWS recommends that upon detection, you should create rule statements in your web access control list that match the unusual behavior detected. You should then monitor the number of requests to determine if you want to block the matching requests. If you decide on the latter, you should change the A.C.L. rules to stop the matching requests.
Network diffusion
This solution works by scattering incoming requests across different servers so that the oncoming traffic is manageable and doesn’t take down the site by straining it.
The biggest problem with DDoS attacks is that they are distributed. There could be tens of thousands of bots in a botnet, and tracing each one is no easy feat.
In the event of a DDoS attack, your first response should be to stop the attack. During this step, you should filter malicious traffic, block the botnet, redirect the traffic to a content delivery network or use a web application protection service to minimize the intensity of the attack.
You may trace specific IP packets that can potentially lead you back to particular bots by doing the following:
- Tracing the bot’s IP address
- Tracing its geolocation
- Identifying the source’s network providers
Since it’s impossible to trace an entire botnet, it’s best to call forensics to reconstruct and investigate the attack.
Learn How to Protect Against DDoS Attacks With ThreatX
Defending organizations from the many forms of modern DDoS attacks is one of the key capabilities of ThreatX. We provide offerings that align with the unique demands of any organization, with comprehensive Layer 7 Distributed Denial of Service Protection that scales with your environment.
Request a demo now to learn how to protect against DDoS attacks and more with ThreatX.
