LAST UPDATED September 12, 2022
With up to 50 percent of Internet traffic generated by bots, organizations are awash in a sea of automated visitors. Some bots are benign, others aren’t. Bad bots can interfere with a customer’s online experience, affect product availability, erode application performance, steal data, and even be used to take over user accounts.
What are bad bots?
Simply put, bots are software robots that are programmed to automate specific tasks and usually operate over a network. A bot turns bad when the automated task it’s programmed to perform is for malicious purposes. A botnet is when many of these bad bots can be controlled to orchestrate a large volume of malicious tasks, together.
Attackers build, buy, or rent botnet capacity and construct their bots in such a way that they can operate across a federated bank of systems, each with its own IP address. In this way, they both increase the speed, frequency, and intensity of their attacks, and reduce the collateral damage to their network of bot soldiers if one node is discovered and blocked.
Learn how to stop malicious bots by understanding their behavior and the variety of ways attackers leverage them. Watch our recent Live Q&A: Malicious Bots in Modern Threats now.
What are bad bots used for?
Attackers most commonly use bots to aid in accessing sensitive data and systems, to hamper or shut down systems completely, or to disrupt inventory for financial gain.
To access or disrupt systems, attackers leverage bots to:
- Perform active enumeration and identify vulnerabilities in apps and APIs.
- Generate overwhelming noise to distract from their real intent – a more targeted attack.
- Bring legitimate systems to their knees, overwhelming them with distributed denial of service attacks.
They’re also commonly used for somewhat less malicious, but still harmful, activities. For instance, during last year’s Christmas holiday season, we saw so-called “Grinch bots,” which bought up all the “hot” holiday items in order to sell them for a markup on the black market. These retail bots simulate real buyers’ behaviors and target e-commerce applications, sometimes resulting in taking down entire sites and making it even harder for buyers to surprise their families with the latest Michael Jordan Nike sneakers, Play Station 5 consoles, or even concert tickets.
Although these bots may not be used for malicious attacks, they do disrupt user’s online buying experience and can diminish the brand’s reputation.
How are bad bots used?
Savvy attackers know that they can map your applications to understand which pages or API calls consume resources such as memory, session handles, or CPU cycles. Armed with that information, they can design a sophisticated, multi-mode attack to consume resources, degrade your app’s performance, and generally muddy the water while trying more pointed exploits. This is the outline of a modern bot-based attack.
There are many ways attackers use bots in their cyberattacks, let’s break down how these bad bots are used in the stages of a sophisticated, multi-mode attack.
- Bot Reconnaissance- Attackers use bots in this phase to gather reconnaissance information because it allows them to quickly explore and test systems of potential vulnerabilities without being detected and without much effort on their part. Common reconnaissance actions for bots are API fuzzing or enumeration attempts, web scraping, credential harvesting, or seeing how an application reacts to requests being sent from IP addresses from certain countries.
- Tuning Bot Tasks- In this stage, attackers will begin acquiring or renting botnet capacity and tuning the bot’s activity based on the results from their recon attempts. These tasks could be sending requests to an old, out of date API endpoint that was discovered to steal user data, using user credentials to access a vulnerable system, or flood an application past its resource capacity to be taken offline.
- Launching a Multi-mode Attack- Now that the attacker has bots targeting known weaknesses in the attack surface of their victim, it’s time to launch the attack. A federated network of attack bots can make the attack “low and slow” and thus hard for defenders to detect. Each IP address is only making one request, maybe every minute, or maybe even five minutes. These requests look legitimate, but they’re trying to steal credentials or sensitive data.
- Bot Evasion- More and more, attackers are using bots as distraction so they can go after the real target unnoticed. To create this needle in a haystack approach, they’ll generate large, volumetric but “obvious” attacks like DDoS, SQLi, or XSS to overwhelm a security solution or trigger thousands of alerts for security to chase down. Then, the attacker’s targeted exploitation attempts get buried under the alerts and are left unnoticed.
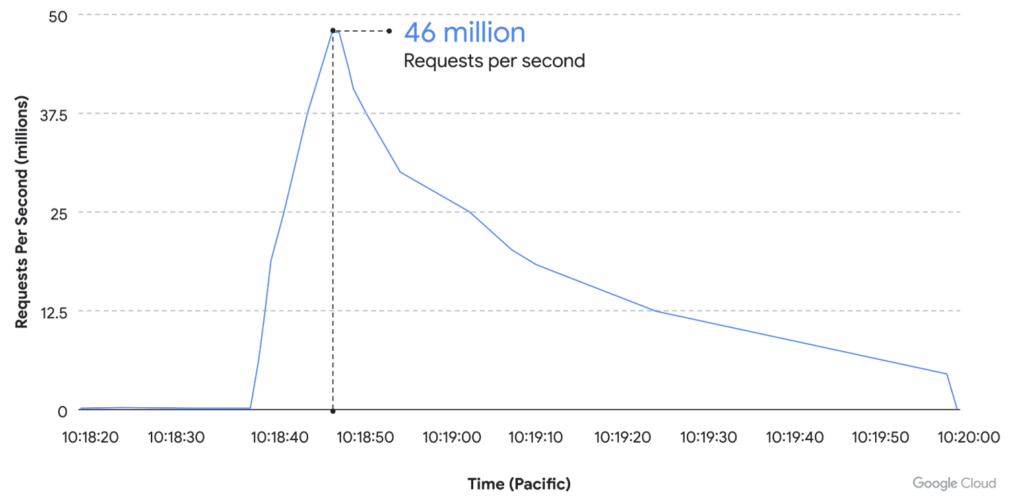
The use of bot-based cyberattacks is increasing, and attackers are scaling these attacks to new heights. Back in June 2022, Cloudflare reported a 26 million request per second (RPS) DDoS attack launched at one of their customer’s sites. Now, Google reports in August 2022 that they detected a DDoS attack that escalated from 100,000 RSP to 46 million RPS, within an hour. To stop these sophisticated and large-scale attacks, security teams must consider a solution that can detect the breadth and depth of attack techniques being used.
Bots are targeting APIs more than ever. With API adoption accelerating and APIs becoming the #1 attack vector, more organizations are formalizing their API security programs. Get started and download the Definitive Guide to API Attack Protection.
How to stop bad bots?
It is important to note that bots and malicious automation are always evolving. Detection that works on one form of automation may not work on another. If an attacker is thwarted by a particular technique, they are likely to shift to others the next time. This makes it important to utilize a solution that takes a combined approach to protecting your web application attack surface against modern bot-based attacks.
- Behavioral analysis continuously monitors the actions of visitors and correlates behaviors over time. Building the historic context of attacker activity provides the ability to identify and block even the “low and slow” attacks that would normally fly under the radar.
- Application profiling learns the behaviors and traits of an application to establish a baseline, providing the context needed to identify suspicious usage.
- Active interrogation or deception technology to challenge a visitor can confidently–and accurately–distinguish a bot from a valid user.
- DDoS protection may be required to protect the allocated resources and ensure applications remain available, on line.
- Inline, Real-time blocking is the only way to ensure applications and APIs are protected against exploitation attempts. If the solution doesn’t provide immediate defense with its own WAF capabilities, then your attack surface isn’t protected.
Evolving bots — How ThreatX can help
Bad bots are one of the few cyber threats that can impact almost every team and functional group within an organization. If the business relies on its online presence, then the effects of automation are likely to be pervasive throughout the organization. The very fact that bots can affect so many teams may actually make it unclear which group should own responsibility for solving the problem. Yet while many teams will be affected, it is ultimately the AppSec and operational security teams who have the hands-on opportunity to address the problem at its source. This provides an ideal opportunity for security teams to step in as problem solvers for a wide variety of teams. Likewise, organizations should have access to experts who are used to dealing with malicious automation. This can allow teams to quickly adapt as attackers shift to new techniques.
Bots can impact a business and uniquely affect each functional team within an enterprise. Techniques and considerations within each functional team can vary. Here’s how:
- Bots vs. The Business Teams: protect the company’s bottom line by making sure your apps serve real customers instead of bots
- Bots vs. The Marketing Team: focus on real visitors and clicks to drive better ROI, conversions and market data
- Bot vs. Operations Team: improve performance and uptime by unloading the burden of unauthorized automation and bots
- Bots vs. Finance & Fraud Team: stop account fraud and takeover at the source before damage is done
- Bots vs. AppSec Team: automate your defense for automated threats
ThreatX provides a fully integrated platform that can detect and mitigate bots by using a variety of active deception techniques to identify automated traffic and block it. The platform also comes with built-in managed security services that provides 24/7 on-demand access to ThreatX experts so that organizations can get the help they need–when they need it.
To learn more about ThreatX and its bot detection and management capabilities, contact the team to schedule a demo.
