LAST UPDATED July 26, 2022
APIs are critical building blocks of modern applications and also represent one of the fastest-growing facets of an organization’s attack surface. Naturally, enterprises need to ensure that these assets are properly managed, provisioned, and remain protected from threats and attackers.
API protection solutions and API gateways both play key roles in this regard, and in some cases will have overlapping capabilities. However, this does not mean that they are interchangeable, and it can be confusing to know exactly how and when to use each technology. With that in mind, let’s take a look at their respective strengths and how API attack protection and API gateways can work together as part of an overall API security strategy.
API Gateway Security Capabilities vs API Threat Protection Capabilities
API threat protection and API gateways have some similarities and even may have some overlapping capabilities. For example, both are typically deployed at an ingress point in front of APIs and both can play important roles in controlling and monitoring authentication.
However, they also have very different core purposes and perspectives. At the highest level, API threat protection remains focused on risky behavior and attacks, while API gateways excel at the operational aspects that keep APIs running properly. The following figure helps to highlight some of these differences.
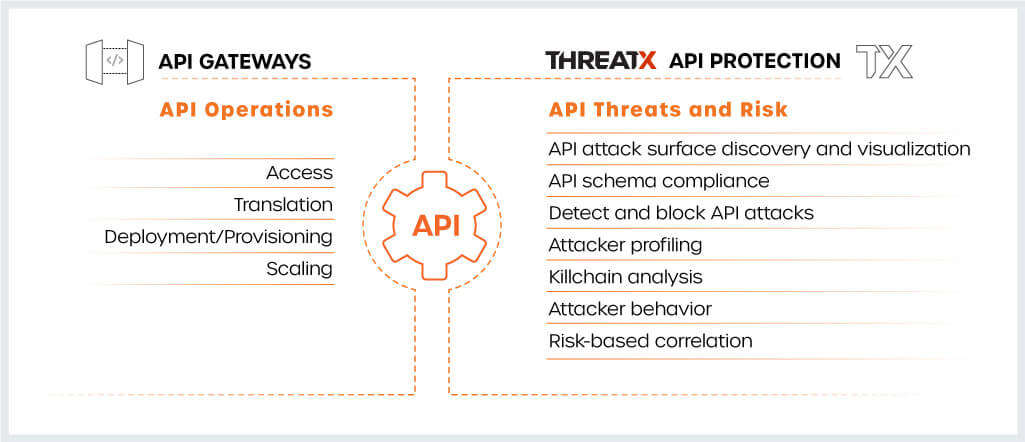
For example, API gateways cover a variety of operational tasks such as controlling access, translating a RESTful request to SOAP, or elastically scaling resources if there is a spike of traffic hitting an API.
API threat protection, on the other hand, focuses on understanding the API attack surface, detecting and blocking the ever-growing spectrum of modern API threats, and keeping up with the changing techniques attackers use to evade detection. This demands considerable expertise and focus to keep pace with evolving threats.
API Gateway Security Features
- Authentication and Encryption
- Rate Limiting
- Transaction Logging
- Runtime Governance Policy
API Threat Protection Features
- API Discovery
- Attack surface visualization
- API Schema Compliance
- API Attack Detection and Response
- Real-time API Risk Management
- Killchain Analysis
API Threat Protection Focuses on Sophisticated Modern Attackers
The modern threat landscape is both incredibly diverse and sophisticated. Attackers have become patient and highly skilled at evading traditional security signatures and rate-based rules. Simply slapping outdated WAF signatures onto an API gateway does little to dissuade these attackers, and they often end up causing more pain than value. These signatures have plagued application and security teams for years due to high rates of false positives and the constant tuning and updating that they require.
Attackers are also highly adept at avoiding these traditional signatures. Attackers use bots and malicious automation in order to blend in with normal user traffic and abuse application features while also obscuring the true nature of the attack. Attacks will often develop over time as attackers steadily look for weak spots in the defenses while staying below the thresholds of rate-based rules.
ThreatX’s API Protection Solution is purpose-built to find and stop these modern threats. In addition to blocking traditional OWASP injection attacks and exploits, ThreatX brings together the industry’s best analysis and prevention techniques, including behavioral analysis of applications, attacker fingerprinting, attacker behavioral analysis, active interrogation, deception, and many others. This ensures that ThreatX can see every event from multiple perspectives to get a true picture of whether an event is benign or malicious.
ThreatX also keeps track of attackers over time and across multiple phases of the kill chain. The platform uses proprietary technology to fingerprint and track attackers even as they change their IP address, user agent, and other traits. Intelligence automatically correlates across all phases of attack to deliver a consolidated, up to the second view of risk so that security teams can proactively take the right action at the right time, even for low and slow attacks.
Advanced API Protection Requires Multi-Cloud Coverage and Context
API security is so critically important that API and cloud infrastructure providers can’t not offer some form of security along with their API offerings. However, this “fries with that” approach to security not only lacks the depth of expertise required, it also misses the breadth of the attack surface. This problem compounds with every different API provider that an organization uses. Hybrid and multi-cloud strategies are quickly becoming the norm, and each cloud provider will have its own proprietary API protections. An Amazon gateway will have different capabilities than the Google gateway, and neither will have the other’s context. As organizations continue to adopt multi-cloud architectures, they can easily end up with many providers, each with their own point solution.
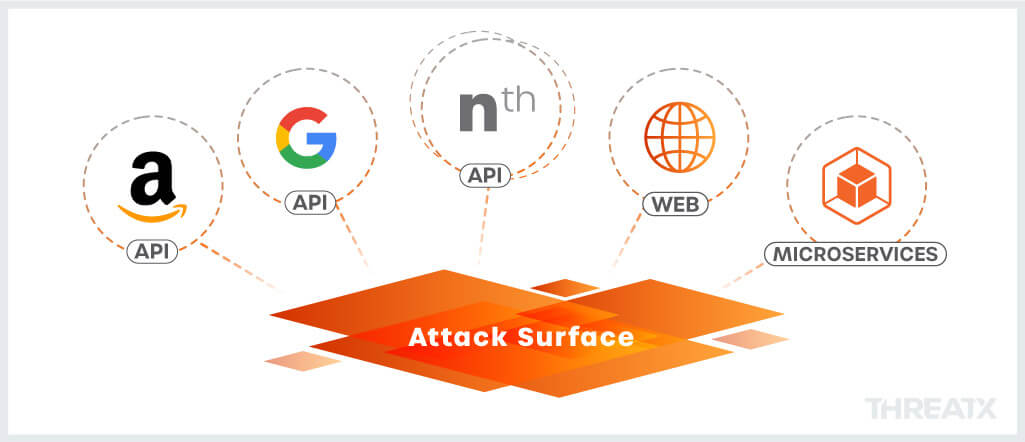
An organization’s security strategy must be able to plug in and support ALL of these API infrastructures as well as the many traditional web assets. The same is true for services and microservices. Security must be able to remain focused on the attacker and recognize that the same attacking group that was testing and probing for weaknesses in one area is now doing the same in the other. This integrated view of risk is essential in order to repel modern attacks.
It is an old adage, but security is still only as strong as its weakest link. This is particularly true when it comes to APIs. These critical technologies are an integral part of modern applications and they must be treated as an integral part of application security. They require security with continuous dedication and expertise to keep pace with the latest changes in the threat landscape. They require consistent protection regardless of where or how they are deployed. They need to benefit from the collective intelligence and context of an organization’s best security tools. ThreatX helps organizations do all of these things and more. Learn more from our educational overview: APIs: Built for Ease of Connectivity. Targeted for High Value Content Delivery.
