Looking for an alternative to Traceable API Security?
Secure all your APIs AND applications with observability, prevention, and protection.
- Visualize your application’s network and runtime traffic
- Discover all APIs and maintain documentation effortlessly
- Protect APIs (and apps) against botnets and threats
- Mitigate vulnerabilities faster with continuous detection, testing, & remediation workflows
Why ThreatX Protect Might Be a Fit for Your Organization
The top challenges we hear from prospects trying to protect their APIs & applications from threats starts from insufficient detection capabilities, struggles deploying in cloud infrastructure, and an abundance of false-positive alerts affecting user experience. ThreatX Protect offers a simpler and more effective approach.
| Compare our Solutions | ThreatX Protect | Traceable Attack Protection |
| Real-time HTTP Traffic Visibility | ||
| Behavioral Threat Detection | ||
| Native Web Application Firewall | ||
| Automated Threat Response | ||
| Protection for API Attacks | ||
| Protection for Web Application Attacks | ||
| DDoS Protection | ||
| Bot Mitigation | ||
| Discovery for External APIs | ||
| API Cataloging | ||
| Sensitive Data Exposure | ||
| API OWASP Top 10 | ||
| Fully Managed |
Why Prospects Choose ThreatX Protect Over Traceable Attack Protection
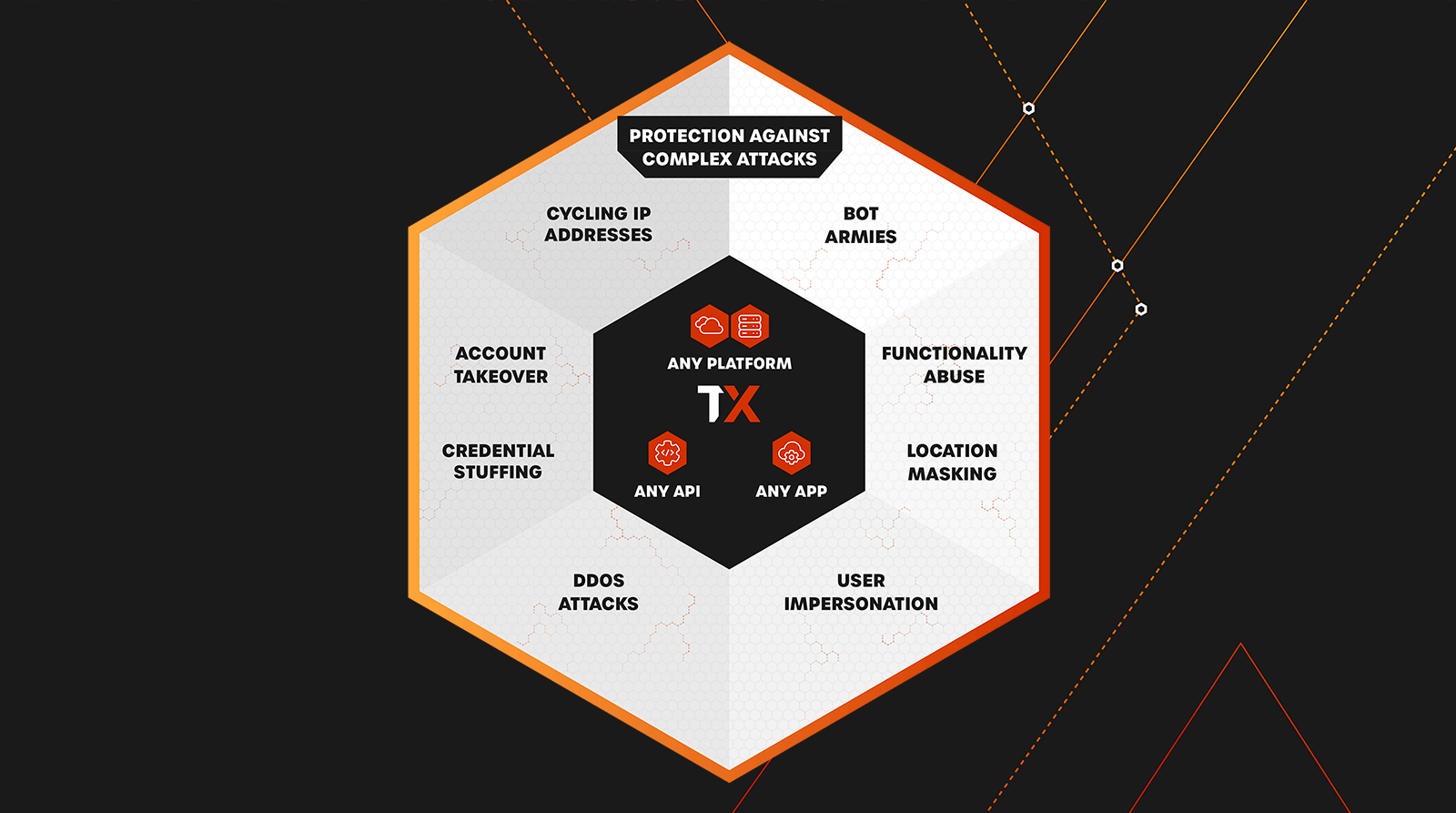
Protect APIs AND Applications
Protect more of your infrastructure from real-time attacks without managing multiple tools
Everything is increasingly complex.
From the infrastructure you’re defending to the attacks against it – security professionals need solutions that simplify.
With ThreatX, you can get deep threat protection for all your APIs and applications from a single platform. Not only can you protect both APIs and apps, but you can also enable real-time observability, discover APIs, detect threats, track behaviors, and block with one powerful but simple platform.

Fully Managed Services
Stay ahead of constantly evolving threats without straining your team’s resources
Stopping zero-day threats requires more than just software. You need real live people – but it doesn’t have to be you.
That’s where ThreatX comes in with 24/7/365 support.
With ThreatX’s Protection-as-a-Service, businesses have access to cybersecurity experts who are available around the clock to mitigate advanced bot and DDoS attacks on your organization’s APIs and apps.
In addition to threat hunting and fine-tuning rules, ThreatX experts also customize defenses for business use cases and provide zero-day protection backed by ThreatX Labs. By leaning on ThreatX’s Protection-as-a-Service, businesses can rest assured they have the resources and expertise needed to protect their operations and reputation from ever-evolving threats.
Learn more about Protection-as-a-Service.
DDoS Attack Mitigation
Defend against any threat targeting APIs and applications without managing multiple products.
Simplify your stack and protect your APIs and applications against DDoS attacks.
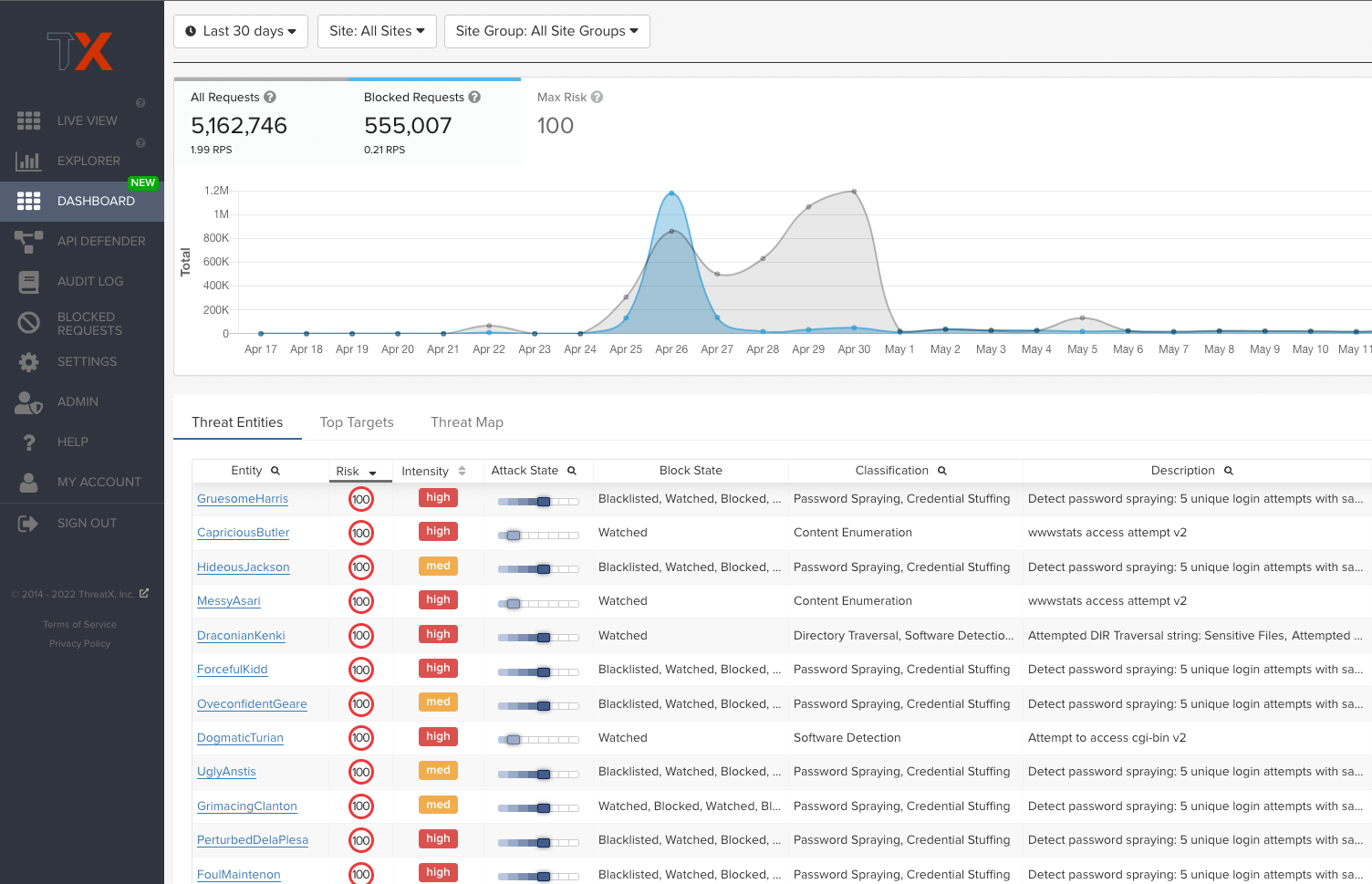
Immediately shut down DDoS attacks targeting your APIs and applications. Ensure your websites and services aren’t impacted by high volume, botnet-powered DDoS attacks. ThreatX blocks malicious bots automatically, rather than giving you information to analyze then transfer to another solution for blocking. And we only block when the behavior reaches a certain risk threshold, so confidence is high and false positives are low.
In addition, our experts are available 24/7 to support active monitoring and incident response at the onset of a DDoS attack. Our Protection-as-a-Service team will have your back and ensure your websites and API-driven services remain protected and operational to legitimate users.
Learn more by reading the ThreatX DDoS Data sheet.

Key Benefits
Secure APIs and applications with Observability, Prevention, and Protection
Eliminate risks without compromising your time or peace of mind.

Easy-to-Use
Experience user-friendly security designed to focus on what matters most. Leverage simplified dashboards so you can effortlessly oversee your API and application’s security posture and risks.
Easy-to-Manage
Get your nights and weekends back with always-active security that ensures your APIs and applications stay safe. Our visionary technology provides continuous protection and prevention without the need for manual intervention. Enjoy peace of mind knowing that your APIs and applications are secure even when you’re off the clock.
Eliminate Risks
ThreatX solutions are always monitoring, assessing, and identifying risks to APIs and applications continuously based on behavior. Our technology learns to recognize threats and vulnerabilities specific to your system, and proactively stops them based on risk level. This ensures your business remains operational and efficient, without interruptions.
Protect Your APIs and Applications with Confidence, Not Complexity
ThreatX is managed API and application protection that lets you secure them with confidence, not complexity. It blocks botnets and advanced attacks in real time, letting enterprises keep attackers at bay without lifting a finger. Trusted by leaders like Lenovo, BMC and Epsilon, ThreatX profiles attackers and blocks advanced risks to protect APIs and web apps 24/7.