Looking for an alternative to Imperva Application Security?
Secure your APIs and apps with observability, prevention, and protection – within one easy-to-use platform.
- Identify and stop attacks with risk-based, real-time blocking
- Continuous API discovery, analytics, and threat investigation
- Protect APIs (and apps) against botnets, DDoS, and advanced attacks
- Fully-managed, with 24/7 support
- On-board and enable protection in minutes
Why ThreatX Might Be a Fit for Your Organization
Prospects often come to us disappointed in legacy WAF solutions or frustrated that the dedicated API Security platform they just turned on is creating too much noise to manage themselves. From struggles deploying in cloud infrastructure to an abundance of false positive alerts resulting in negative impacts to user experience, ThreatX offers a simpler and more practical approach.
ThreatX customers often value best-of-breed protection, simple management and deployment, and the partnership they form with our Protection-as-a-Service team as an extension of theirs. Our platform is cloud-native and easily protects APIs and apps across any mix of cloud infrastructure.
| Compare our Solution Features | ThreatX | Imperva |
| Behavioral Threat Detection | ||
| Risk-based Blocking | ||
| Web Application Firewall | API Protection | |
| Bot Defense | DDoS Protection | |
| Protection-as-a-Service | ||
| API Specification Generation | ||
| API OWASP Top 10 |
Why Prospects Choose ThreatX Over Imperva
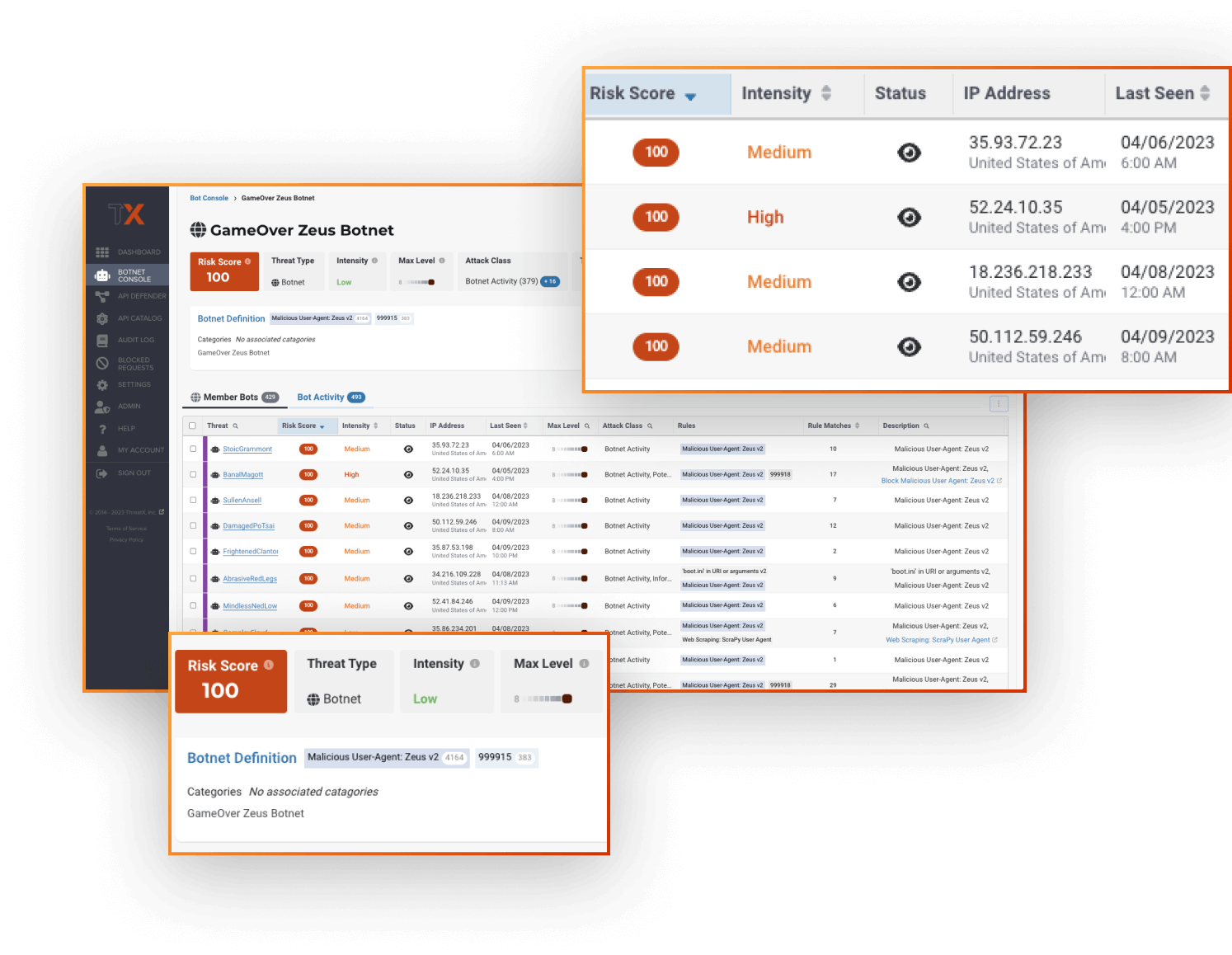
Behavioral Threat Detection
Stay ahead of cyber threats for good so you can ditch the game of cat and mouse.
Attackers are always switching up their methods and tactics. With solutions that are signature-based or reliant on static rulesets, this quickly devolves into a never-ending game of cat and mouse. Your team ends up wasting valuable cycles on menial tasks that aren’t making you safer.
ThreatX is always monitoring, assessing, and correlating attacker behavior to quickly and accurately identify threats. Continuously tracking attackers over time, ThreatX provides a complete view of the evolving threats targeting your APIs and applications.
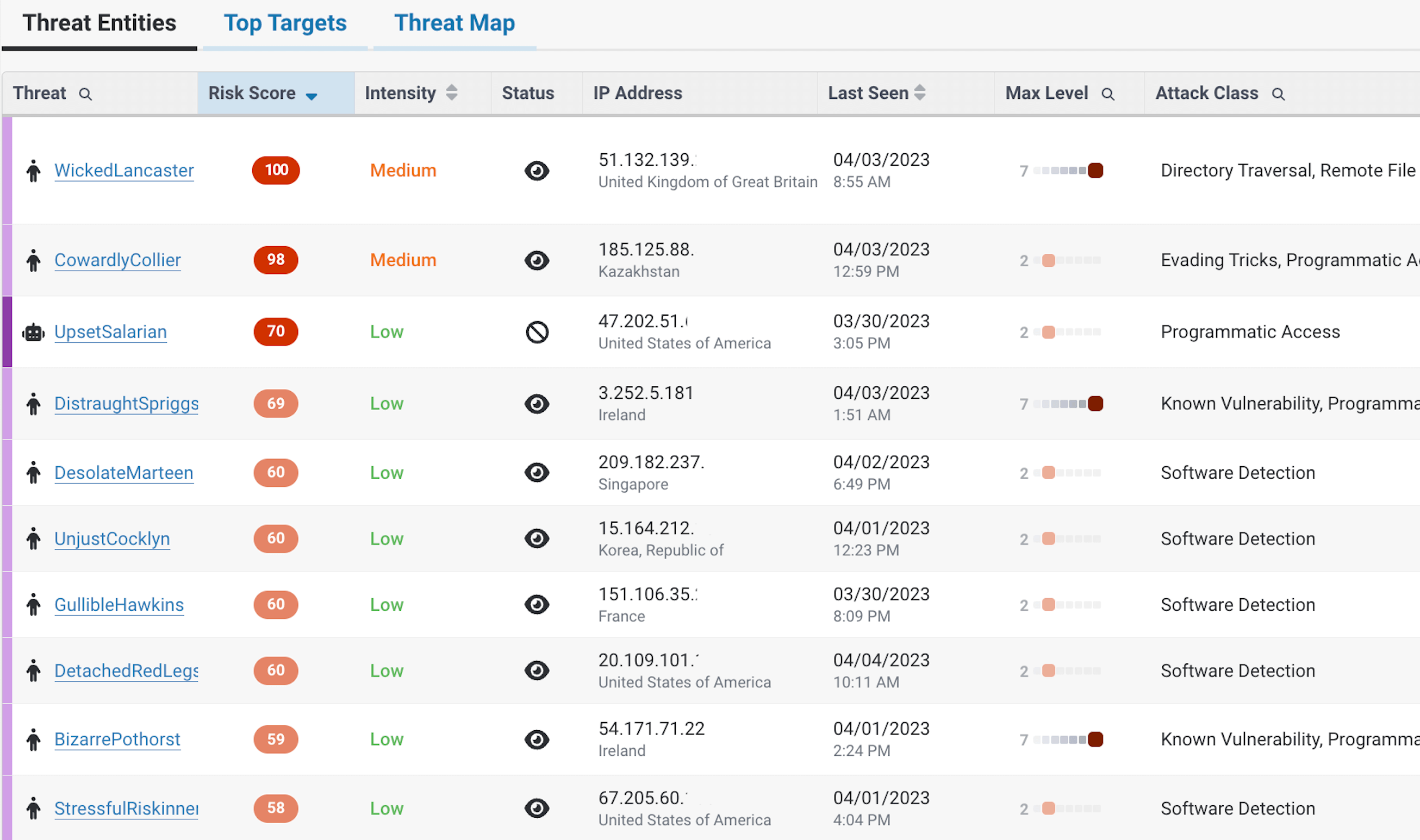
Risk-Based Blocking
Block attacks automatically, based on behavior being tracked over time.
Get the ability to discover, detect, track, and block attackers all with a single solution.
There’s nothing more frustrating than the challenge of bolting solutions together only for latency or misconfiguration to miss real attacks. That’s why it was so important to architect a solution that could quickly protect, out-of-the-box against a wide range of threats.
Furthermore, with ThreatX’s risk-based approach to blocking, false positives and alert fatigue will become problems of the past.
Learn more about risk-based blocking with ThreatX.
Protection-as-a-Service
Stay ahead of constantly evolving threats without straining your team’s resources.
Stopping zero-day threats requires more than just software. You need real live people – but it doesn’t have to be you.
That’s where ThreatX comes in with 24/7/365 support.
With ThreatX’s Protection-as-a-Service, businesses have access to cybersecurity experts who are available around the clock to mitigate potential attacks. In addition to threat hunting and fine-tuning rules, ThreatX’s experts also provide businesses with options to customize defenses for business use cases and zero-day protection backed by ThreatX Labs. By leaning on ThreatX’s Protection-as-a-Service, businesses can rest assured they have the resources and expertise needed to protect their operations and reputation from ever-evolving threats.
Learn more about Protection-as-a-Service.


Key Benefits
Secure APIs and applications with Observability, Prevention, and Protection
Eliminate risks without compromising your time or peace of mind.

Easy-to-Use
Experience user-friendly security designed to focus on what matters most. Leverage simplified dashboards so you can effortlessly oversee your API and application’s security posture and risks.
Easy-to-Manage
Get your nights and weekends back with always-active security that ensures your APIs and applications stay safe. Our visionary technology provides continuous protection and prevention without the need for manual intervention. Enjoy peace of mind knowing that your APIs and applications are secure even when you’re off the clock.
Eliminate Risks
ThreatX solutions are always monitoring, assessing, and identifying risks to APIs and applications continuously based on behavior. Our technology learns to recognize threats and vulnerabilities specific to your system, and proactively stops them based on risk level. This ensures your business remains operational and efficient, without interruptions.
Protect Your APIs and Applications with Confidence, Not Complexity
ThreatX is managed API and application protection that lets you secure them with confidence, not complexity. It blocks botnets and advanced attacks in real time, letting enterprises keep attackers at bay without lifting a finger. Trusted by leaders like Lenovo, BMC and Epsilon, ThreatX profiles attackers and blocks advanced risks to protect APIs and web apps 24/7.