LAST UPDATED April 2, 2024
We recently analyzed data collected on the ThreatX API and Application Protection platform from October through Decemeber 2023. Two stand-out trends we see across industries are 1) the prevalence of bot attacks, which are rampant across companies of every size and in every industry, and 2) the diversity of the threat landscape, with different industries facing a variety of attack types.
Below we share details of and analyze ThreatX platform data from Q4 2023.
Attack Types by Industry
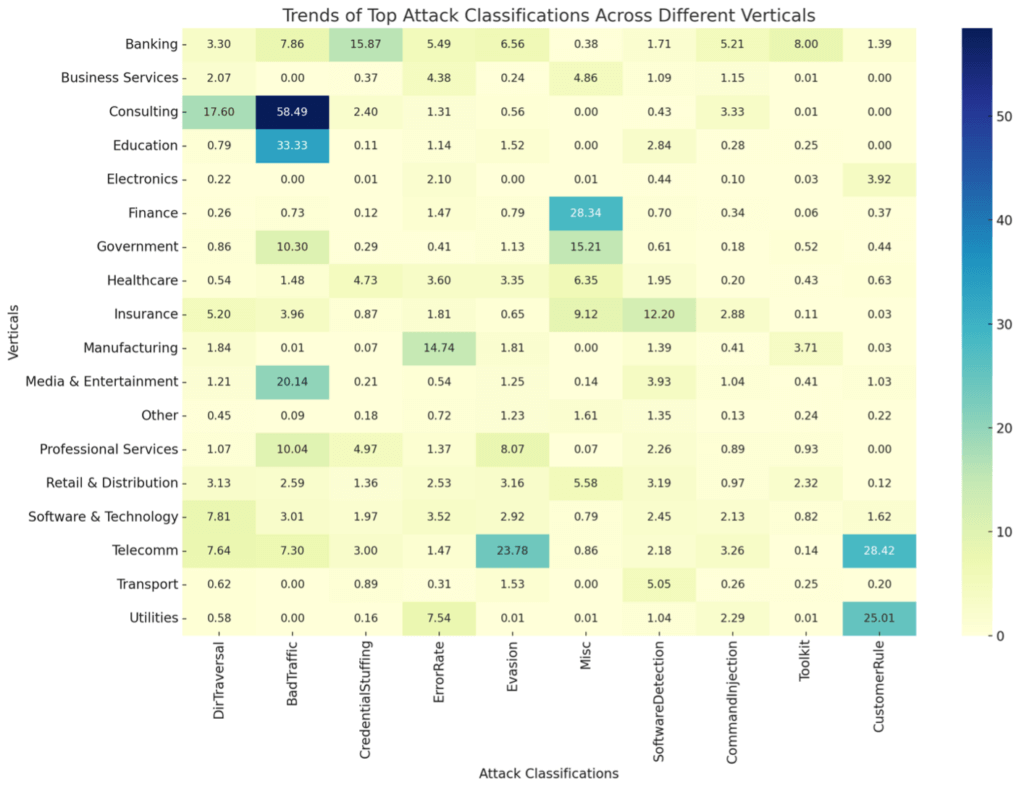
The heatmap above provides a visual representation of top attack classifications across different verticals. Here are some key observations:
Varied impact across verticals: Different verticals are impacted differently by each attack classification. This variation underscores the need for vertical-specific cybersecurity strategies.
High prevalence in certain verticals: Some verticals, like government and education, show high prevalence in specific attack types like Bad Traffic. The finance sector exhibits significant levels of Command Injection, which is a critical concern given the sensitive nature of financial data.
Consistent threats across verticals: Bad Traffic appears to be consistent across most verticals, indicating a widespread challenge with malicious traffic.
Key Insights by Attack Classification
| Attack Type | Definition | Industry Most Affected |
| Programmatic Access | This type of attack involves automated or non-human interactions with web applications and APIs, potentially aiming to scrape data, perform unauthorized transactions, or exploit vulnerabilities. | Electronics Extremely high values, indicating significant automated access attempts. |
| Bad Traffic | Anomalous traffic may be a malformed request or something unexpected based on the expected traffic behavior. This could be an invalid HTTP request that does not better fit in a specific attack category, like HTTP smuggling (for example). Bad Traffic is usually HTTP traffic that does not meet the standard specifications of the HTTP protocol. This could include mismatching headers and values, invalid or unexpected characters, for example. | Consulting Indicates substantial traffic from known malicious sources. |
| Customer Rule | Custom rules written in a custom application context. | Telecom High custom rule matches could imply targeted attacks or unique threat landscapes. |
| Misc | Misc is an attack type category we assign to match events that do not fit in other categories. This is often used for matching on traffic that is specific to the context of a customer’s applications or business use-cases. This may include things like restricting access to particular parts of the application, or tracking specific types of traffic like what time does somebody access particular pieces of the system. | Finance Could indicate a variety of unspecified threats or anomalies in financial services. |
| Web Attack | An attacker uses known attack parameters or a known payload. | Transport This might indicate specific web application vulnerabilities or targeted attacks exploiting these weaknesses in the Transport sector. |
| Evasion | Attackers frequently now use a variety of techniques to try to evade security solutions. If we see activity like varying timing of requests, randomizing header values, IP rotation, or encoding, we start tracking. | Telecom High evasion tactics could indicate sophisticated threats targeting communication networks. |
| Denial of Service | Inundation of computing resources in order to shut down a machine or network. | Business services Reflects the risk of service disruptions in this sector. |
| Brute Force | Attacks that feature attackers using trial and error to try to access a system. | Banking High incidence of forceful breach attempts is a significant risk for financial data. |
| Bad Bot | Bots performing malicious activities like scraping, fraud, and spam. High prevalence indicates automated attacks. Bad Bot is known bad bots, such as Mirai, or bot traffic that Threatx has determined to be bad based on the actions it is taking. | Significantly higher in Government, Healthcare, Manufacturing, and Transport. This could be due to the high value or sensitivity of data in these sectors, making them attractive targets for automated malicious activities. |
| SQL Injection | In a SQL injection attack, an attacker injects a SQL query via the input data from the client to the application. | Notably higher in Education, Finance, Government, and Manufacturing. These verticals might be more prone to web application vulnerabilities, or they might be specifically targeted due to the critical nature of their operations and data. |
| Cross-Site Scripting | In a cross-site scripting (XSS) attack, an attacker injects malicious executable scripts into the code of a trusted application or website. | Significantly higher in Business Services, Consulting, Insurance, Retail & Distribution, and Telecom. These sectors might have web applications that are more exposed or vulnerable to XSS attacks, possibly due to the nature of their online services. |
| RFI (Remote File Inclusion) | Allows an attacker to include a file on a server | Particularly high in Consulting and Software & Technology This suggests potential vulnerabilities in web applications or targeted attacks exploiting these vulnerabilities in these sectors. |
Most Widesepread Attack Types
Bad Bot, SQL Injection, Web Attack, and XSS (Cross-Site Scripting) stand out with their widespread impact across industries. Here’s an overview of each classification and the potential strategies for mitigation:
Bad Bot:
- Overview: Bots performing malicious activities like scraping, fraud, and spam. High prevalence indicates automated attacks.
- Implications: Can lead to data theft, fraud, and degraded user experiences.
- Mitigation Strategies:
- Implement bot management solutions.
- Use CAPTCHAs and challenge-response tests.
- Monitor and analyze traffic patterns for anomalies.
SQL Injection:
- Overview: Injection of malicious SQL queries exploiting vulnerabilities in web applications.
- Implications: Can result in data breaches, unauthorized data manipulation, and complete system compromise.
- Mitigation Strategies:
- Use prepared statements and parameterized queries.
- Implement regular code reviews and vulnerability assessments.
- Apply web application firewalls (WAFs) to detect and block SQL injection attacks.
Web Attack:
- Overview: Various forms of attacks targeting web applications, including SQL injection, XSS, and more.
- Implications: Threatens data security, can lead to unauthorized access and data loss.
- Mitigation Strategies:
- Employ comprehensive web application security practices.
- Conduct penetration testing and vulnerability scanning.
- Ensure up-to-date patching of all software and use of security-enhanced frameworks.
XSS (Cross-Site Scripting):
- Overview: Injecting malicious scripts into web pages viewed by others.
- Implications: Can hijack user sessions, deface websites, or redirect users to malicious sites.
- Mitigation Strategies:
- Implement strong input validation and output encoding.
- Use Content Security Policy (CSP) headers to prevent script injections.
- Educate developers about secure coding practices.
Most Popular Attack Types Across Industries
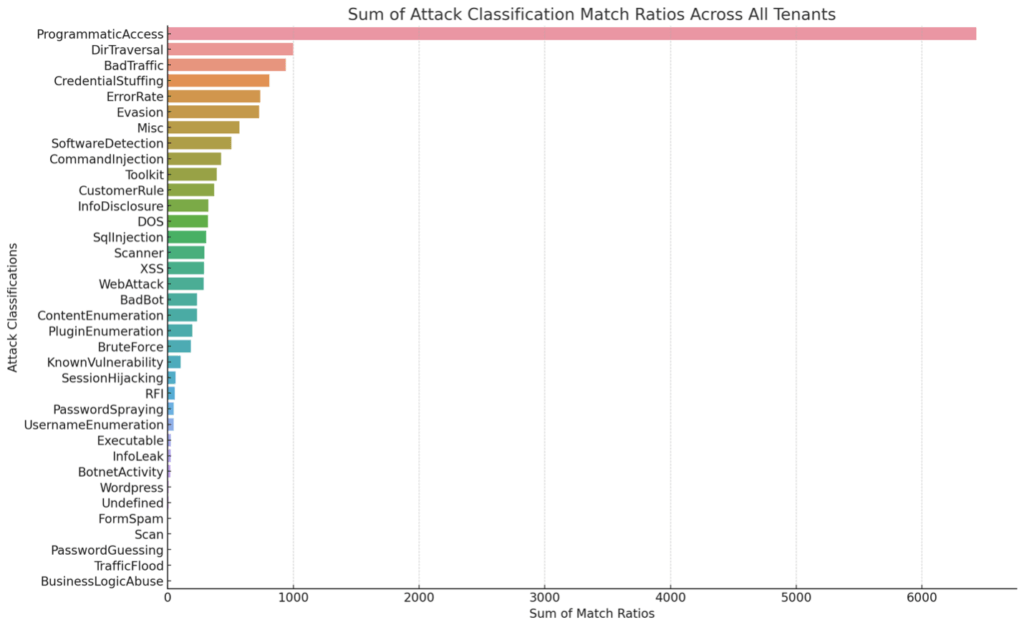
The bar graph above displays the sum of match ratios for each attack classification across all tenants. The length of each bar represents the cumulative prevalence of each attack type, giving a visual representation of which classifications had the most matches in the dataset.
From the graph, you can identify which attack classifications are most common across all tenants, providing valuable insights into the prevalent security threats. These insights can be particularly useful for understanding the broader security landscape and for informing security strategies and priorities.
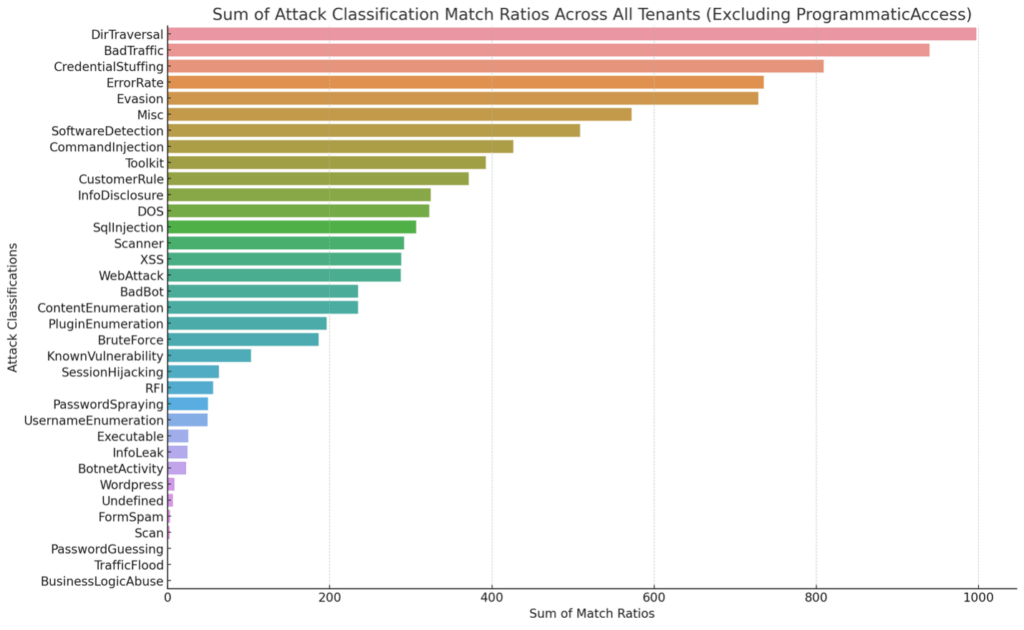
The updated bar graph now excludes the “Programmatic Access” classification, providing a more balanced view of the other attack classifications. This visualization should offer a clearer perspective on which types of attacks are more prevalent across the tenants, excluding the skewing effect of the outlier.
To learn more about how our solution collects these data points, take a quick, self-guided tour of the ThreatX platform.
