LAST UPDATED June 14, 2022
We’re pleased to announce that we have expanded and enhanced our API protection capabilities to give customers better protection and better visibility into their API attack surface. The new capabilities will give customers:
- Deeper insight into the scope of API attacks
- Better visualization of API attack surface
- Ability to identify API schema compliance gaps that attackers can exploit
We know from our conversations with prospects and customers that these new capabilities will help address two big pain points: Lack of API visibility and awareness, and accountability for acceptable API usage. Organizations know they have a lot of APIs, but not how to discover or inventory them all. Most have an assortment of APIs sitting behind various gateways, some being stood up by developers outside of any gateway, some with no schema attached, or some that have been essentially orphaned.
In addition, most organizations are struggling to understand who is using their APIs, and what acceptable usage is – things like the amount of information they should be providing, how they are providing it, and the levels of authentication and authorization are often a mystery.
In response to these pain points, ThreatX has added the following capabilities:
API Schema Compliance
For many organizations, particularly those with distributed DevOps teams, API schemas provide a central way of defining how APIs should work. Without a schema, it is difficult for security teams to understand whether any API call is legitimate or malicious, creating a significant security risk for organizations.
To address this challenge, ThreatX’s new API schema compliance capabilities will allow customers to centrally manage OpenAPI 3.0 schemas for the API endpoints ThreatX discovers and protects. Users can build custom schemas for APIs that are outdated or even have no schemas available. This enables organizations to compare API traffic to specifications to determine whether compliance gaps exist so that they can work to mitigate them.
This new capability complements ThreatX’s real-time discovery capabilities, which shine a spotlight on API endpoints that may be out of the view of security and development teams, such as zombie and rogue APIs. These two views combined give customers a holistic and clear picture of their API attack surface, along with an understanding of when and where APIs are being managed appropriately.
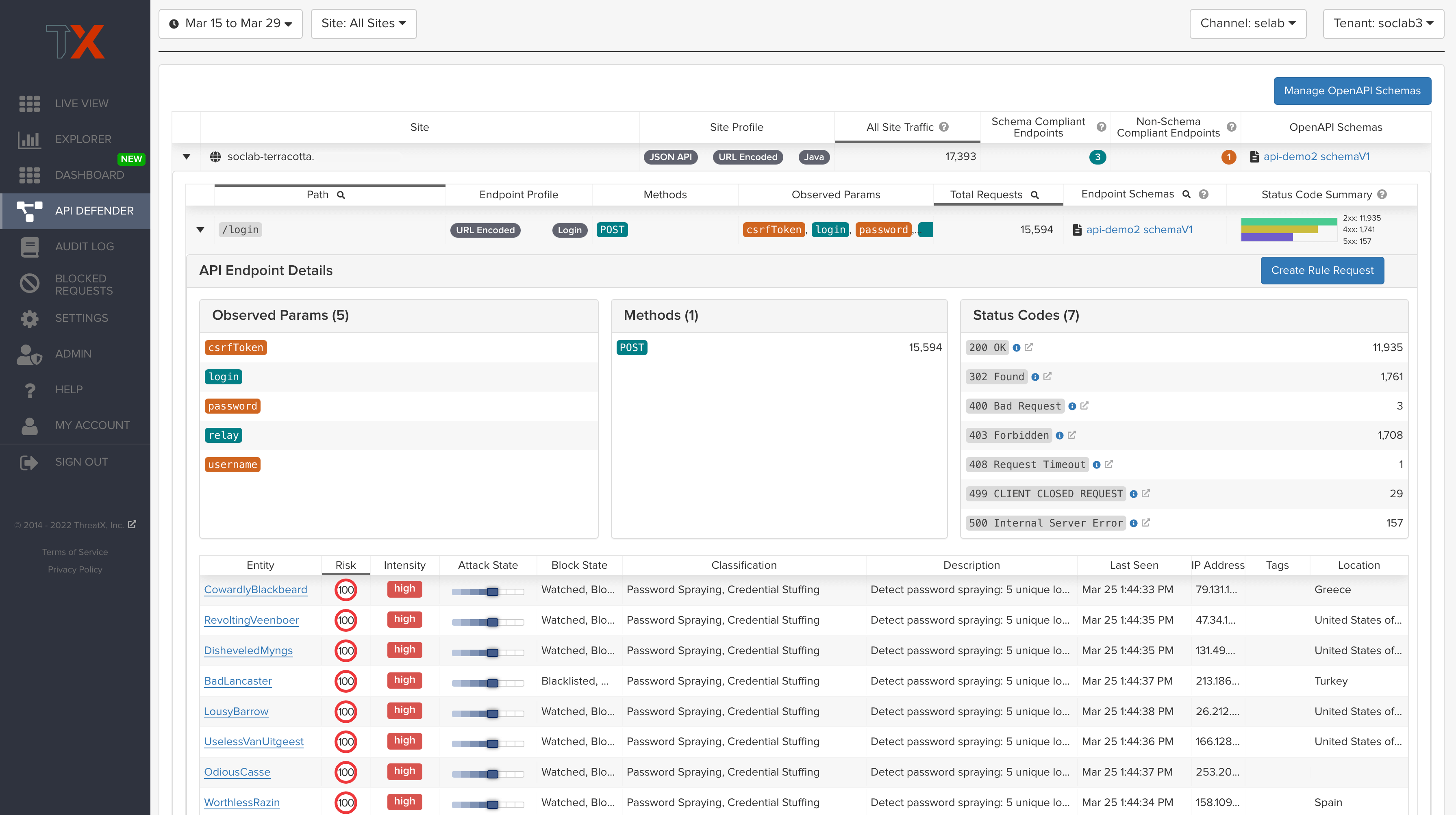
API Dashboard
ThreatX’s enhanced API Dashboard details:
- API endpoint usage and how it compares to expected behavior, as defined in actions from the schema
- API traffic analytics
- Error code summaries
In addition, users now have the ability to filter traffic in the Attack Dashboard by API or web traffic – giving a more precise view into attack targets.
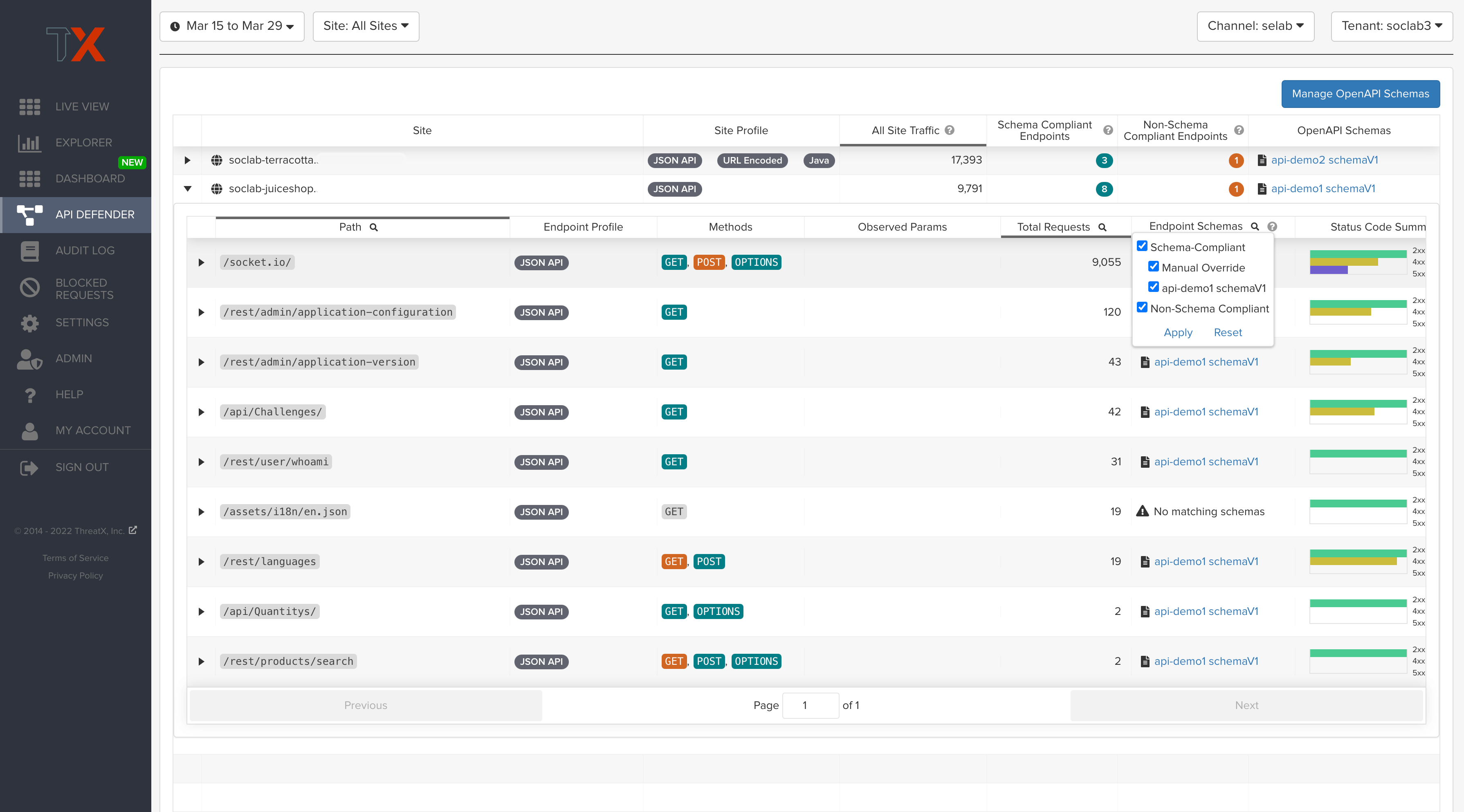
Ultimately, ThreatX’s dashboards makes it easier than ever for organizations to drill into the finer points of API attacks. With a comprehensive set of data available, customers can quickly take responsive actions, such as enabling automatic blocking, establishing geo-fencing to block traffic from parts of the globe where there shouldn’t be clients, or tarpitting attacks to prevent overconsumption of backend resources.
For More Details
Learn more about ThreatX’s API protection capabilities in our new datasheet. To see the solution in action, please request a demo, or sign up for our 30-day free trial.
