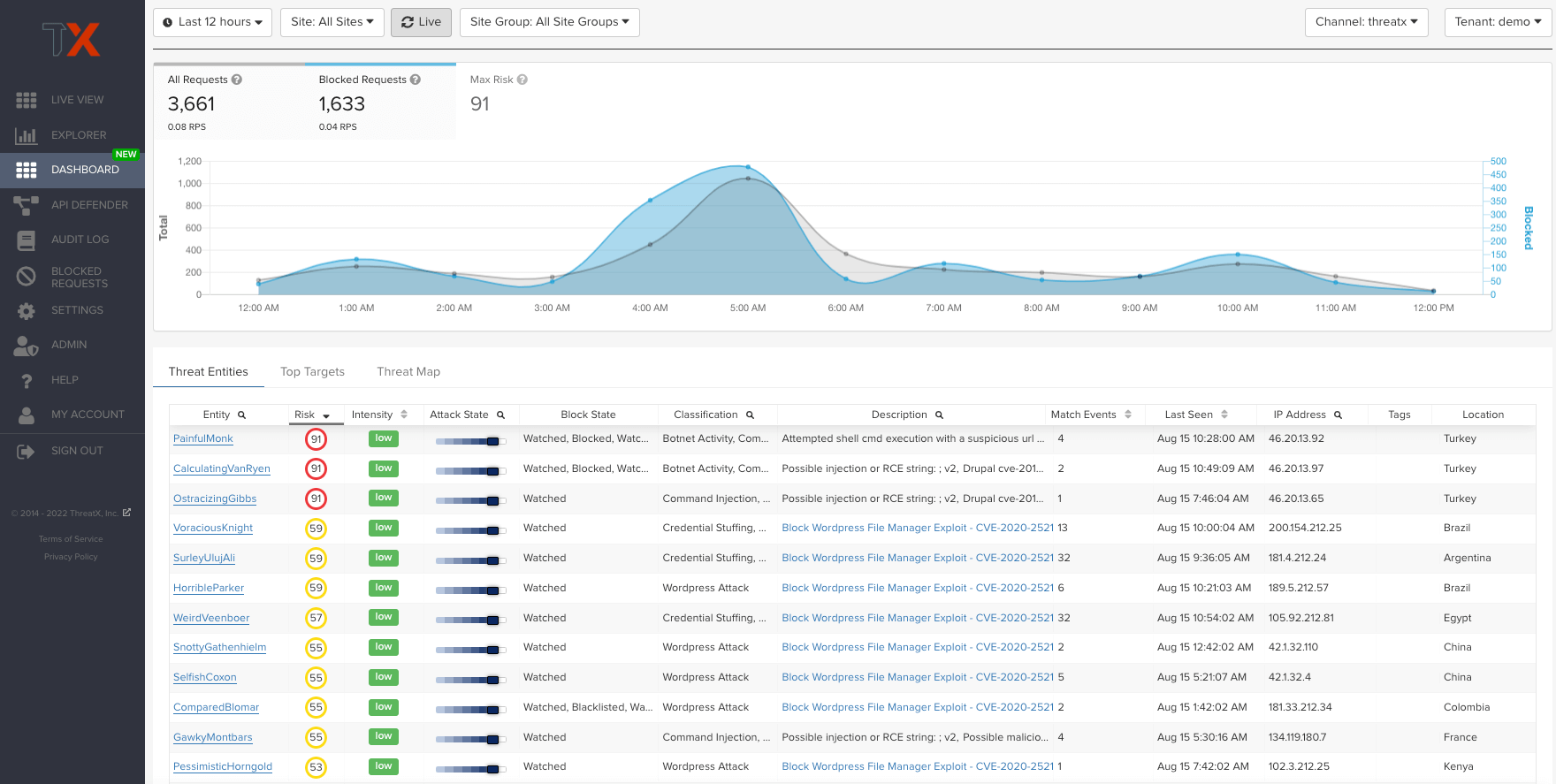
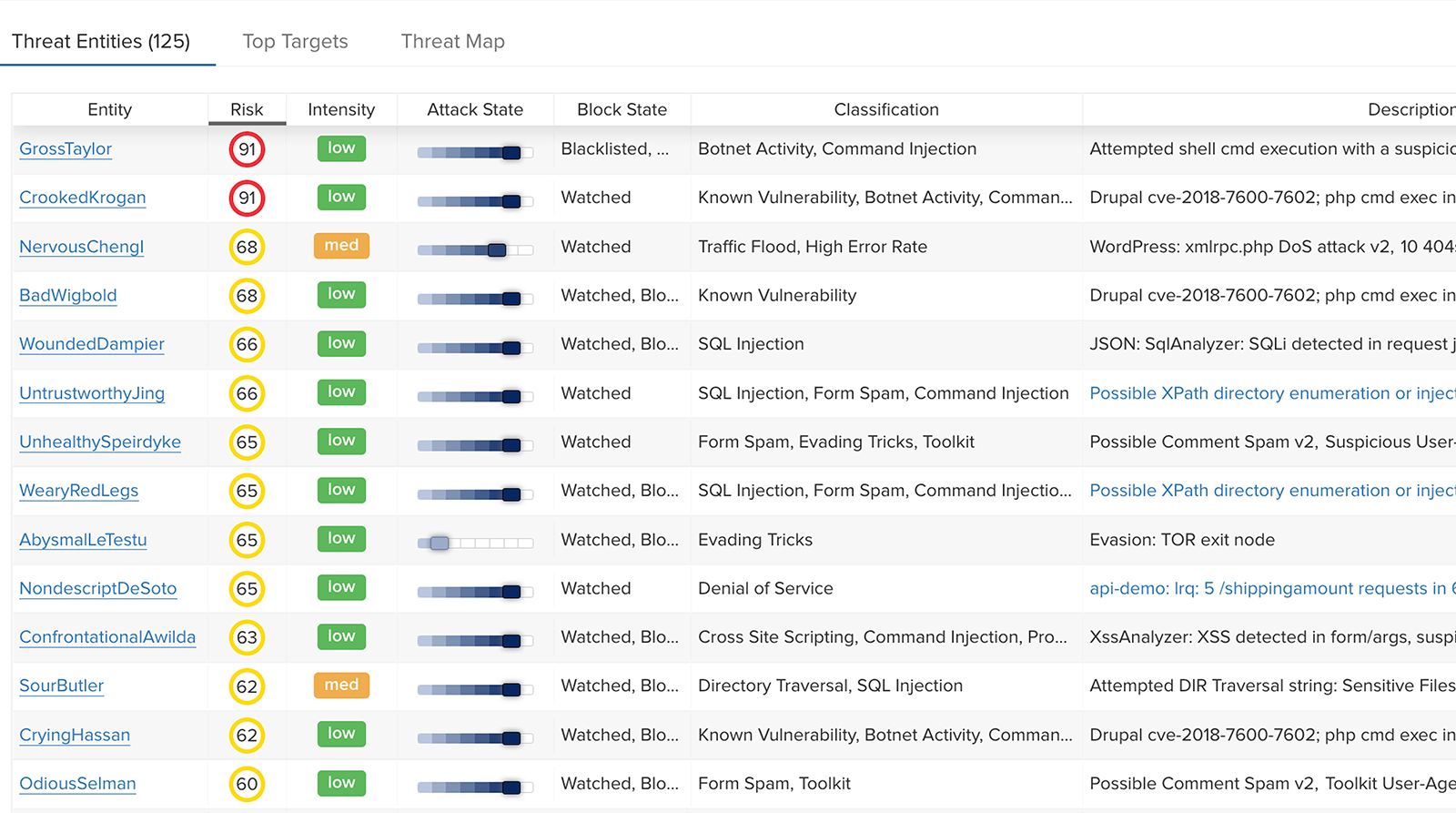
“With ThreatX, I’m in the console a lot, but not because I’m trying to troubleshoot and stop threats, I just like going in there and taking screenshots and showing them, ‘look at all the blocks.’”
Information Security Analyst, Large Financial Services Organization
View all case studies