Greetings InfoSec UK Attendees
Thanks for visiting with ThreatX at the 2023 InfoSec UK conference.
New ThreatX Content Resources
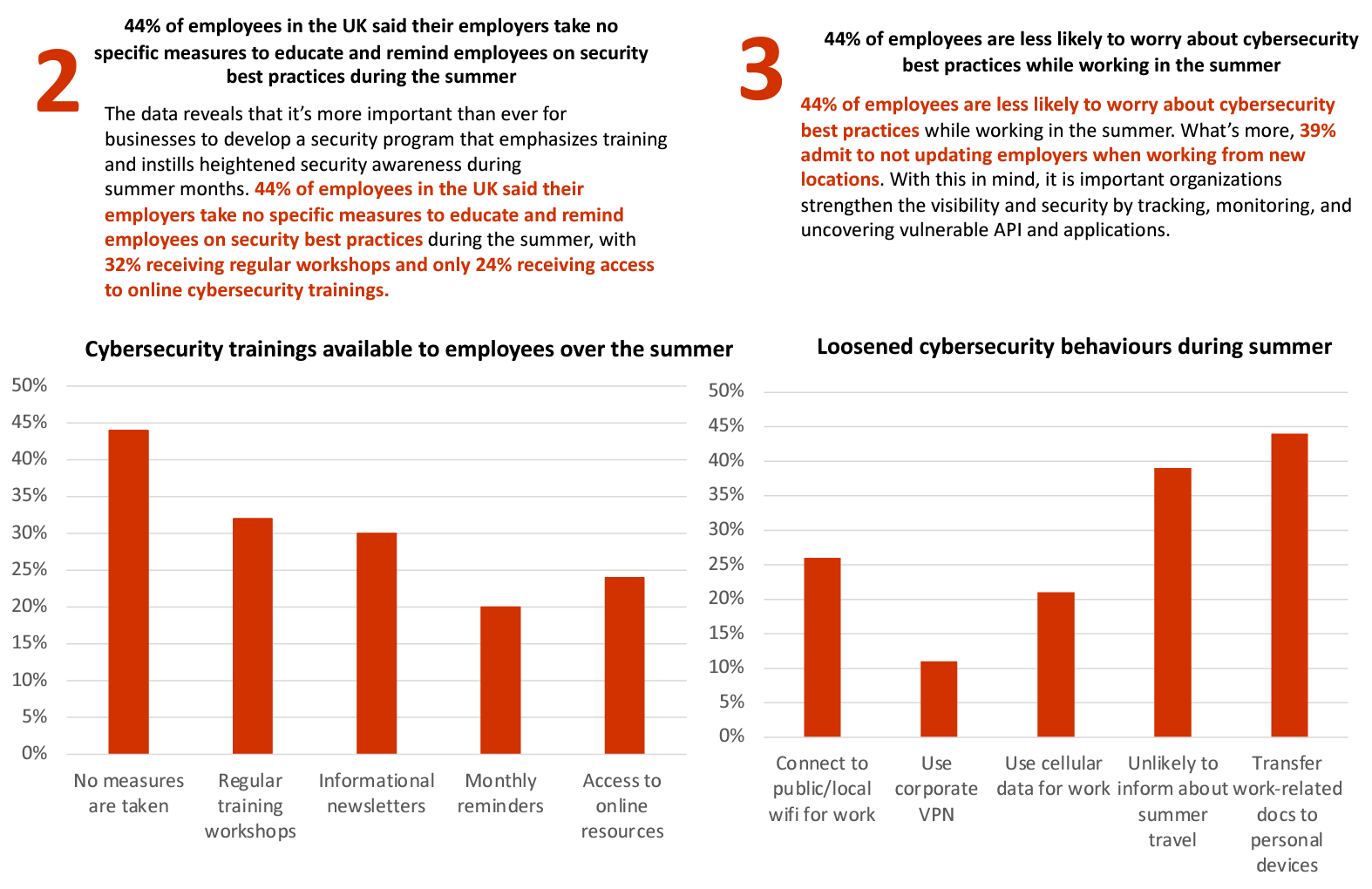
*Source: June 2023 Dynata survey of 2,000 US and UK based consumers ranging from 21+ years of age. This infographic is reflective of the 1,000 UK respondents, exclusively.
2023 Survey Research Released
Survey reveals 33% of employees in the US and UK are less likely to worry about cybersecurity best practices while working in the summer; 38% admit not updating employers when working from new locations
New research released today from ThreatX, the leading API and application protection platform, reveals that IT teams are struggling to monitor and enforce BYOD (Bring Your Own Device) policies during summer months when more employees are often traveling or working remotely. With more endpoints and applications in use, and often personal rather than corporate issued, the risk to corporate data may increase. Given APIs are the driving force behind these connections, the study reinforces the need for prioritizing API and application security.
ThreatX Platform Overview
Block attacks in real time with API and app protection you can trust 24×7 (without having to manage it yourself).
These days, everything’s more complex – from your infrastructure itself to the attackers who want to exploit it. The use of APIs and applications has exploded, making attackers’ jobs easier and yours a lot harder. You can never let your guard down, even on a Friday night or at your kid’s basketball game.
Today’s sophisticated threats persistently target your assets with attacks like API abuse, credential stuffing, account takeover, vulnerability exploits, and DDoS. Most of these attacks leverage botnets designed to evade detection with solver software and other techniques like IP rotation.
API Threat Protection Overview
Learn How ThreatX is Blocking Attackers in Their Tracks
APIs Power Business Today
APIs are the foundation of the Internet today; nearly every modern software application uses – or is – an API. As companies undergo digital transformation, APIs enable DevOps teams to quickly deliver new services and capabilities. According to Gartner, by 2025, over 75 percent of organizations will directly or indirectly monetize APIs.
APIs Are Under Attack
Gartner believes that by 2024, API abuse and related data breaches will nearly double. The proliferation of APIs leapfrogged security’s ability to protect these assets, resulting in many high-profile security breaches such as Peloton, Venmo, Facebook, and the U.S. Postal Service, to name a few. Organizations continue to struggle to track all their APIs, protect all their APIs, and, now more than ever, identify which security vendors can deliver on the promises and capabilities they claim.
ThreatX Bot Defense Overview
Stop bot attacks and other forms of malicious traffic automation.
The Rise of Bot Traffic
Malicious bots interfere with a customer’s online experience, affect product availability, erode application performance, steal data, and even take over user accounts. And bot traffic continues to rise; up to 50 percent of Internet traffic is now generated by bots.
Organizations are awash in a sea of automated visitors, and the situation is only getting worse.
Attackers are now using solver services — software packages for purchase on the dark web that have “solved” vendors’ bot detection defenses — to evade detection, along with other techniques like cycling IPs to avoid geo-location and low/slow bot attacks. All in all, attackers are finding new ways to make their botnets smarter and harder to detect.

Runtime API & App Protection Overview
Bringing Real-Time Threat Detection & Blocking to Runtime
The use of cloud infrastructure – and, often, multiple cloud providers – creates new sets of risk. Many attackers now prioritize finding backdoors – often by exploiting vulnerabilities in running applications – to circumvent edge and perimeter defenses.
Protecting runtime APIs and applications in real time
With attackers eyeing running APIs and applications, the ability to detect, track, and block attacks – in real time – is an increasing priority. With the patent-pending ThreatX Runtime API & Application Protection (RAAP) capability, CISOs and their teams can bolster runtime security without slowing developers or requiring deep expertise in cloud-native applications. By leveraging ThreatX RAAP, organizations can deploy ThreatX’s proven risk-based blocking capabilities at the edge to running applications and APIs.
Protection-as-a-Service Overview
Protecting APIs and Applications From Threats – Everywhere, All the Time
More than just software. More than just managed services. ThreatX is people-powered threat protection that takes the worrying off your plate for good.
Organizations often struggle to find the time and talent needed to meet the daily demands of security and keep pace with advancing threats. That’s why ThreatX provides a dedicated team of highly trained experts who continuously focus on the API and application threat landscape and its impact on our customers.
Through the ThreatX Protection-as-a-Service (PaaS) offering, our team of security experts provide 24×7 proactive monitoring and streamlined threat response. Our team partners with your security staff to ensure you are informed and confident that your APIs and applications are protected.
